This version of the form is not currently in use and is provided for reference only. Download this version of
DD Form 2959
for the current year.
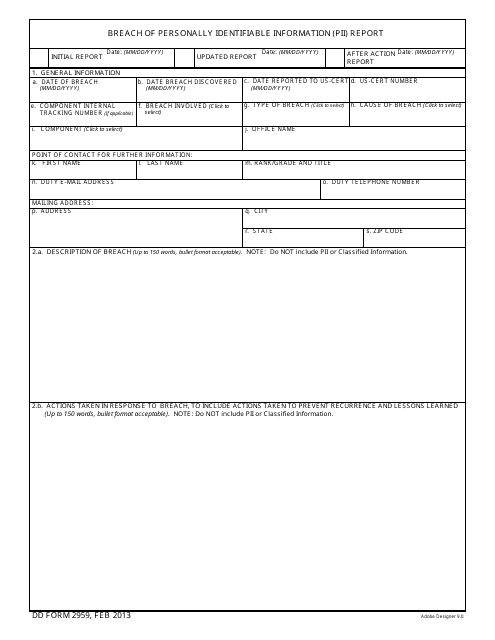
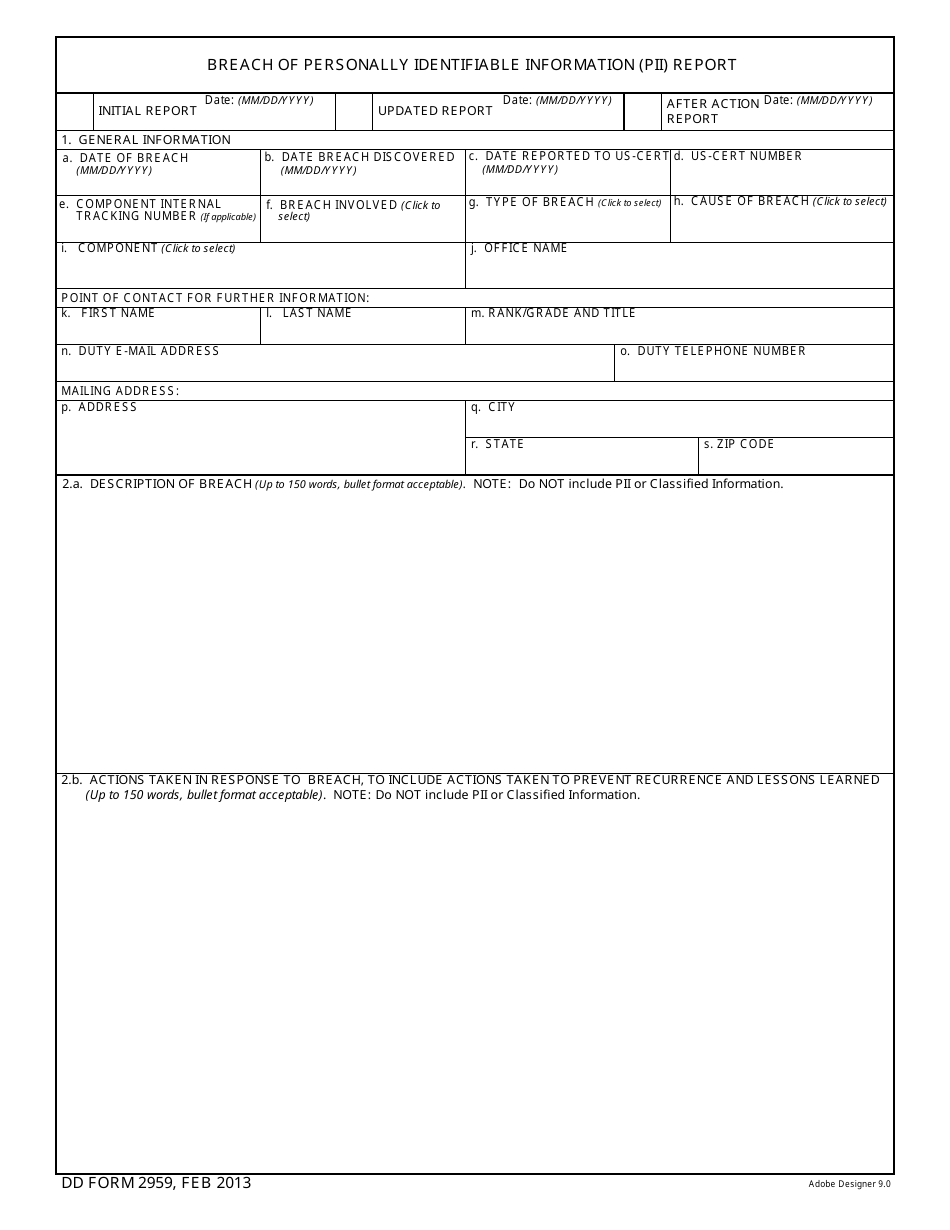
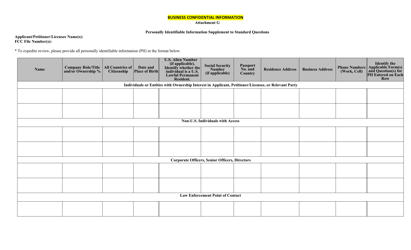
DD Form 2959 Breach of Personally Identifiable Information (Pii) Report
Fill PDF Online
Fill out online for free
without registration or credit card
What Is DD Form 2959?
This is a form that was released by the U.S. Department of Defense (DoD) on February 1, 2013. The form, often mistakenly referred to as the DA Form 2959, is a military form used by and within the U.S. Army. As of today, no separate instructions for the form are provided by the DoD.
Form Details:
- A 3-page document available for download in PDF;
- The latest version available from the Executive Services Directorate;
- Additional instructions and information can be found on page 3 of the document;
- Editable, printable, and free to use;
- Fill out the form in our online filing application.
Download an up-to-date fillable DD Form 2959 down below in PDF format or browse hundreds of other DoD Forms compiled in our online library.