Vulnerabilities Equities Policy and Process
Vulnerabilities Equities Policy and Process is a 14-page legal document that was released by the United States National Security Council on November 15, 2017 and used nation-wide.
FAQ
Q: What is the Vulnerabilities Equities Policy and Process?
A: The Vulnerabilities Equities Policy and Process is a framework used by the United States government to determine whether to disclose or retain information about software vulnerabilities.
Q: What is a software vulnerability?
A: A software vulnerability is a weakness or flaw in software that can be exploited, potentially allowing unauthorized access or compromising the system's security.
Q: Why is the Vulnerabilities Equities Policy important?
A: The policy is important as it helps the government decide whether to disclose a software vulnerability to the vendor for patching or to retain it for intelligence or law enforcement purposes.
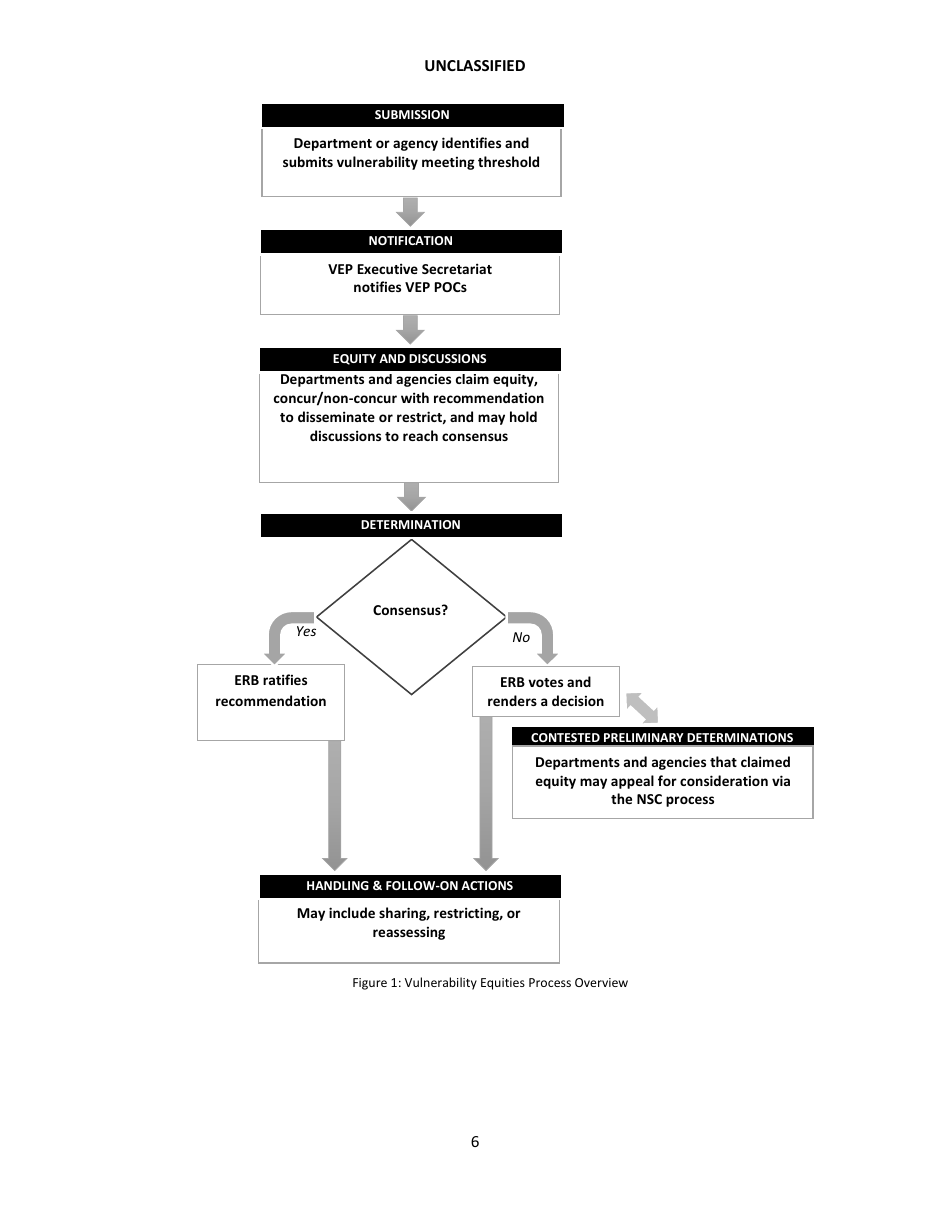
Q: How does the Vulnerabilities Equities Process work?
A: The process involves multiple government agencies evaluating the potential risks and benefits of disclosing or retaining a software vulnerability. It considers factors such as the likelihood of exploitation, potential impact, and the availability of alternatives.
Q: Who is responsible for the Vulnerabilities Equities Policy and Process?
A: The Vulnerabilities Equities Policy and Process is overseen by the National Security Council with inputs from various government agencies, including the intelligence community and law enforcement.
Form Details:
- The latest edition currently provided by the United States National Security Council;
- Ready to use and print;
- Easy to customize;
- Compatible with most PDF-viewing applications;
- Fill out the form in our online filing application.
Download a printable version of the form by clicking the link below or browse more legal forms and templates provided by the issuing department.