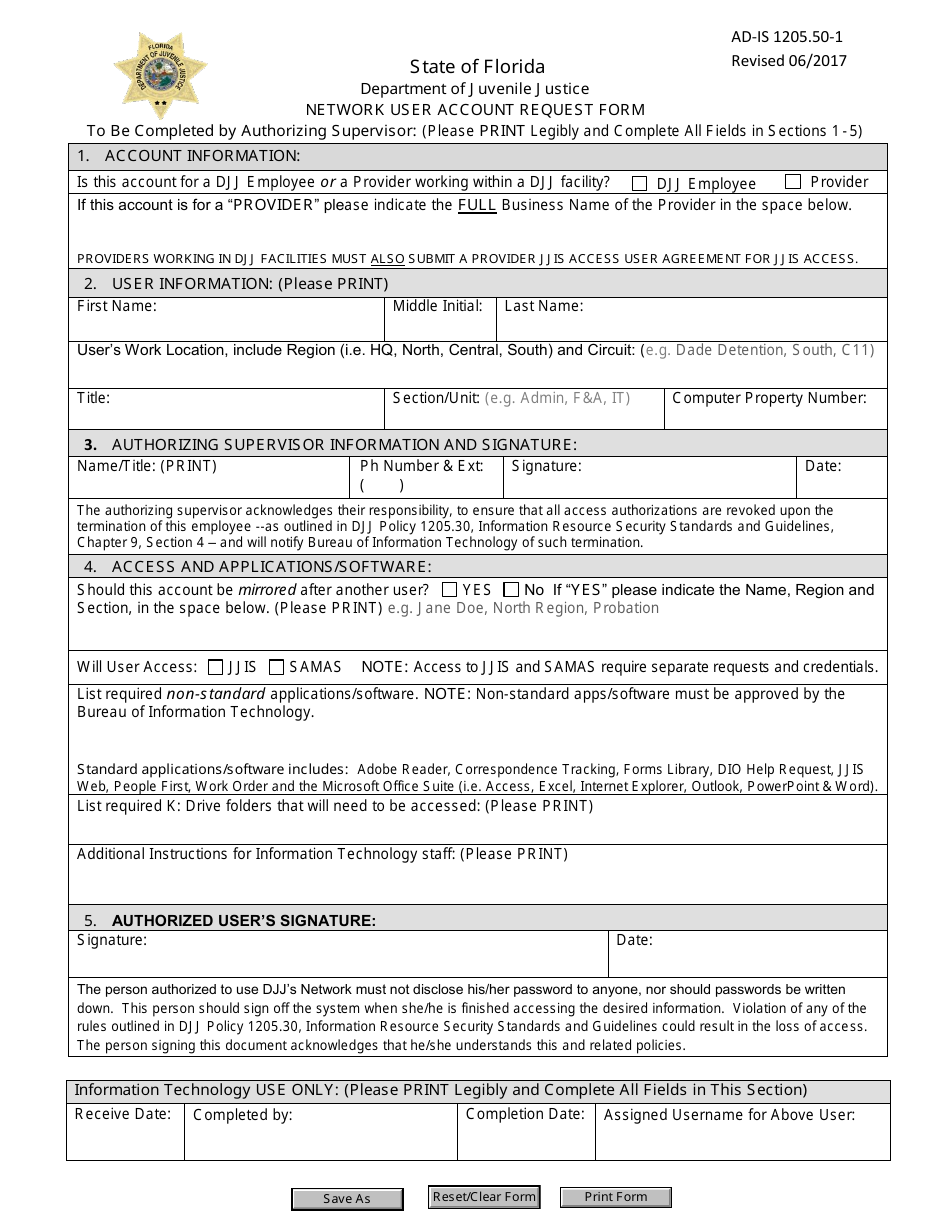
DJJ Form AD-IS1205.50-1 Network User Account Request Form - Florida
What Is DJJ Form AD-IS1205.50-1?
This is a legal form that was released by the Florida Department of Juvenile Justice - a government authority operating within Florida. As of today, no separate filing guidelines for the form are provided by the issuing department.
FAQ
Q: What is DJJ Form AD-IS1205.50-1?
A: DJJ Form AD-IS1205.50-1 is the Network User Account Request Form used in Florida.
Q: What is the purpose of DJJ Form AD-IS1205.50-1?
A: The purpose of DJJ Form AD-IS1205.50-1 is to request a network user account.
Q: Who can use DJJ Form AD-IS1205.50-1?
A: DJJ Form AD-IS1205.50-1 can be used by individuals in the Florida Department of Juvenile Justice (DJJ) who need a network user account.
Q: Is DJJ Form AD-IS1205.50-1 specific to a certain state?
A: Yes, DJJ Form AD-IS1205.50-1 is specific to Florida.
Form Details:
- Released on June 1, 2017;
- The latest edition provided by the Florida Department of Juvenile Justice;
- Easy to use and ready to print;
- Quick to customize;
- Compatible with most PDF-viewing applications;
- Fill out the form in our online filing application.
Download a fillable version of DJJ Form AD-IS1205.50-1 by clicking the link below or browse more documents and templates provided by the Florida Department of Juvenile Justice.