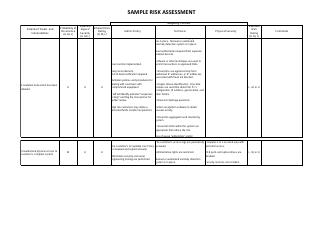
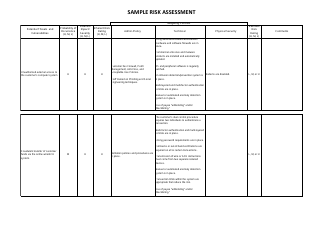
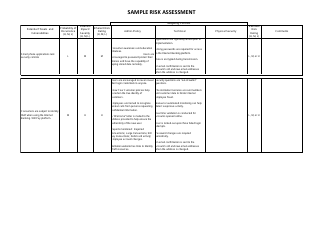
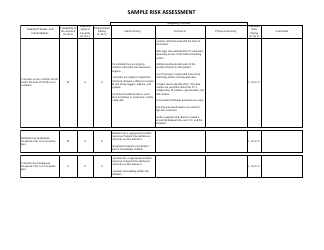
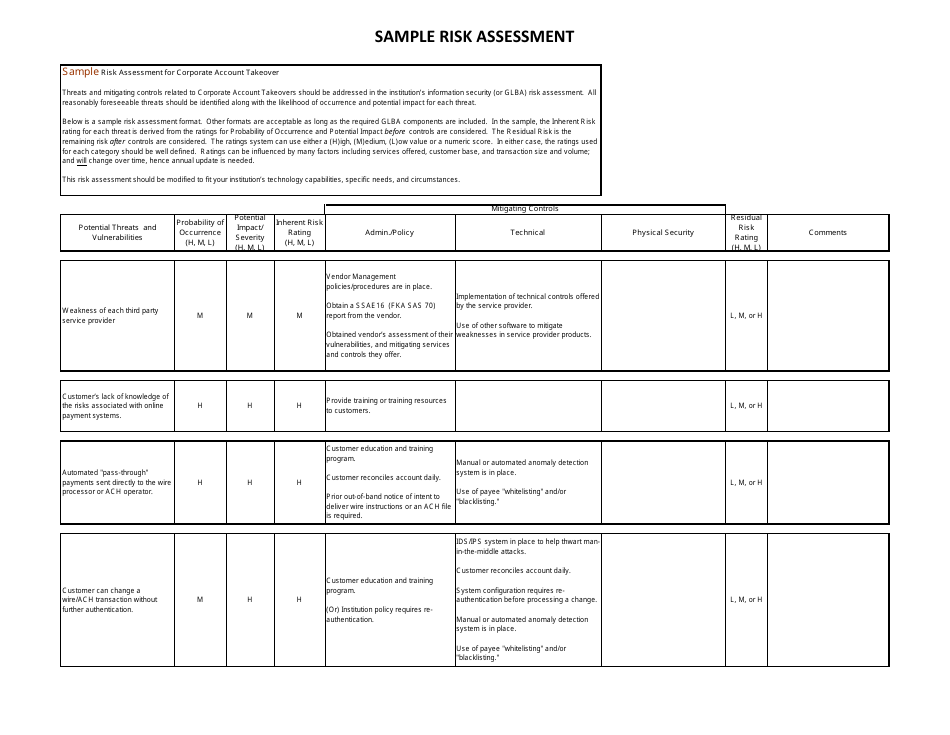
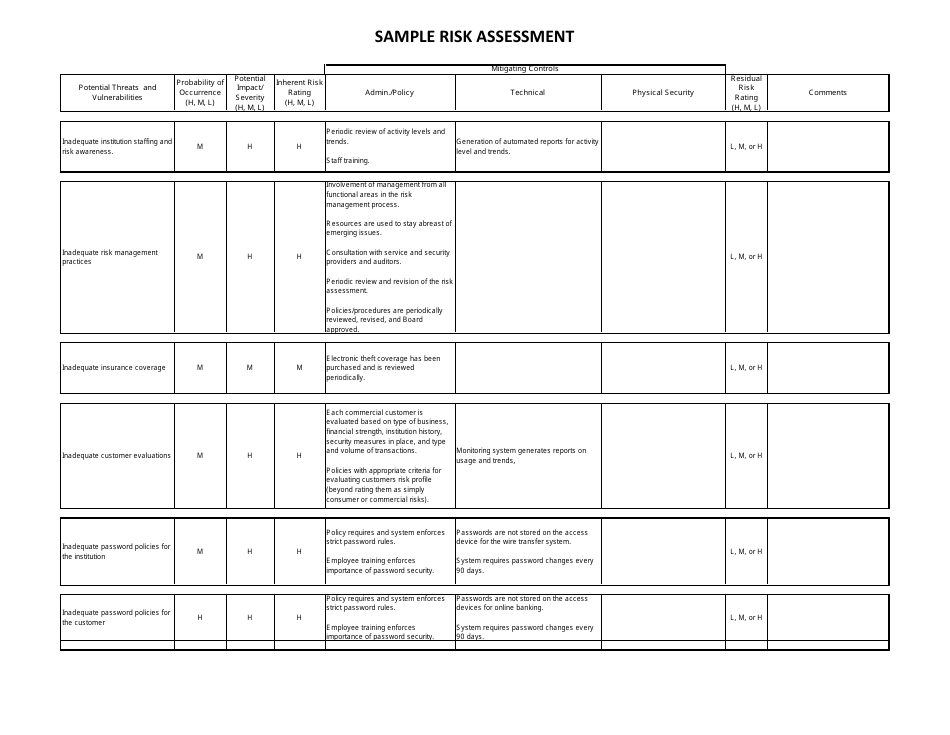
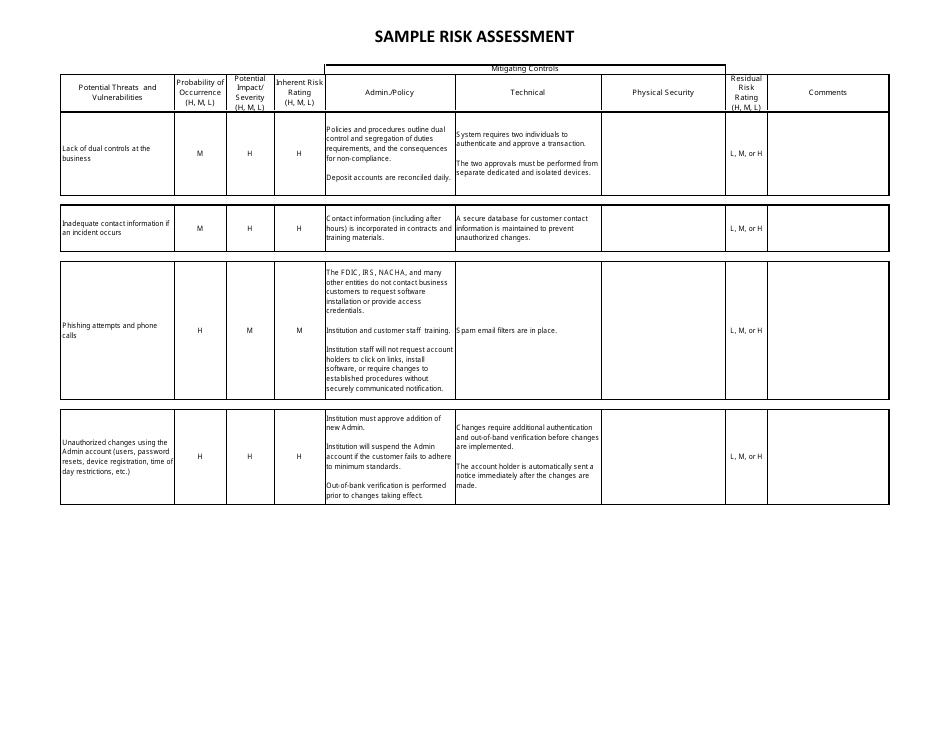
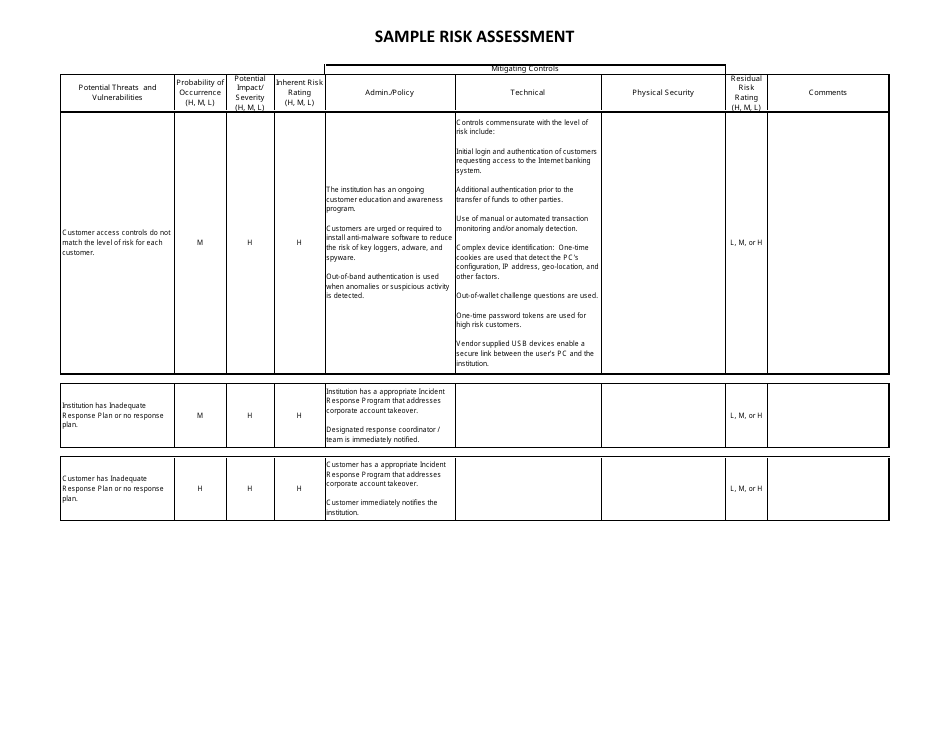
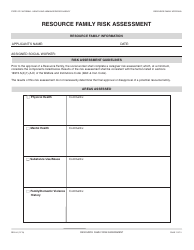
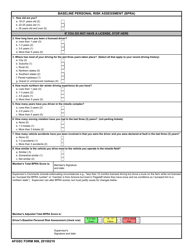
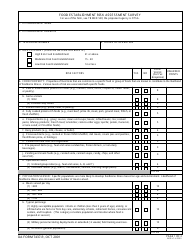
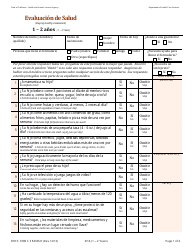
Sample Risk Assessment Form - California
Risk Assessment Form is a legal document that was released by the California Department of Financial Protection and Innovation - a government authority operating within California.
FAQ
Q: What is a risk assessment form?
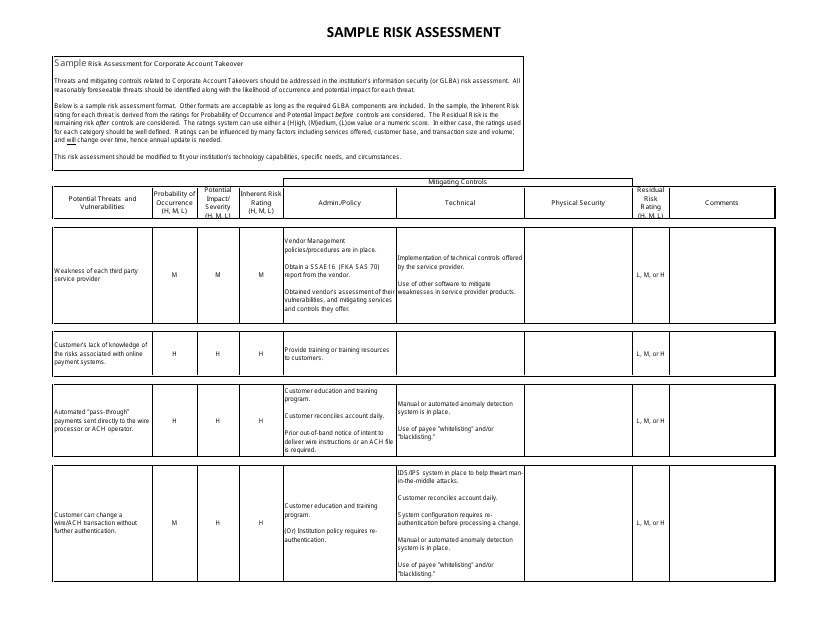
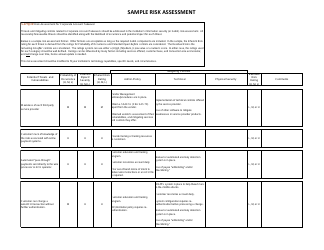
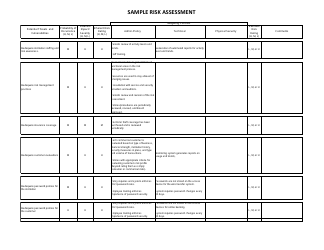
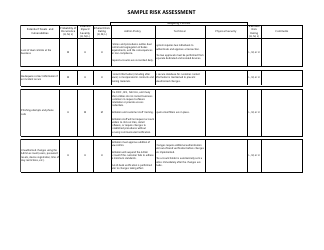
A: A risk assessment form is a document used to identify and evaluate potential risks and hazards in a specific situation or area.
Q: Why is a risk assessment form important?
A: A risk assessment form is important because it helps minimize risks, prevent accidents, and ensure the safety of individuals and the environment.
Q: Who uses a risk assessment form?
A: A risk assessment form is used by individuals, businesses, and organizations to assess and manage risks.
Q: What are the components of a risk assessment form?
A: A risk assessment form typically includes sections for identifying hazards, evaluating risks, implementing control measures, and monitoring and reviewing the effectiveness of those measures.
Q: How often should a risk assessment form be reviewed?
A: A risk assessment form should be reviewed regularly, especially when there are changes to the situation or environment that may introduce new risks.
Q: Is a risk assessment form required by law?
A: In some cases, a risk assessment form may be required by law, particularly in certain industries or for specific activities that involve potential hazards.
Form Details:
- The latest edition currently provided by the California Department of Financial Protection and Innovation;
- Ready to use and print;
- Easy to customize;
- Compatible with most PDF-viewing applications;
- Fill out the form in our online filing application.
Download a printable version of the form by clicking the link below or browse more documents and templates provided by the California Department of Financial Protection and Innovation.