This version of the form is not currently in use and is provided for reference only. Download this version of
the document
for the current year.
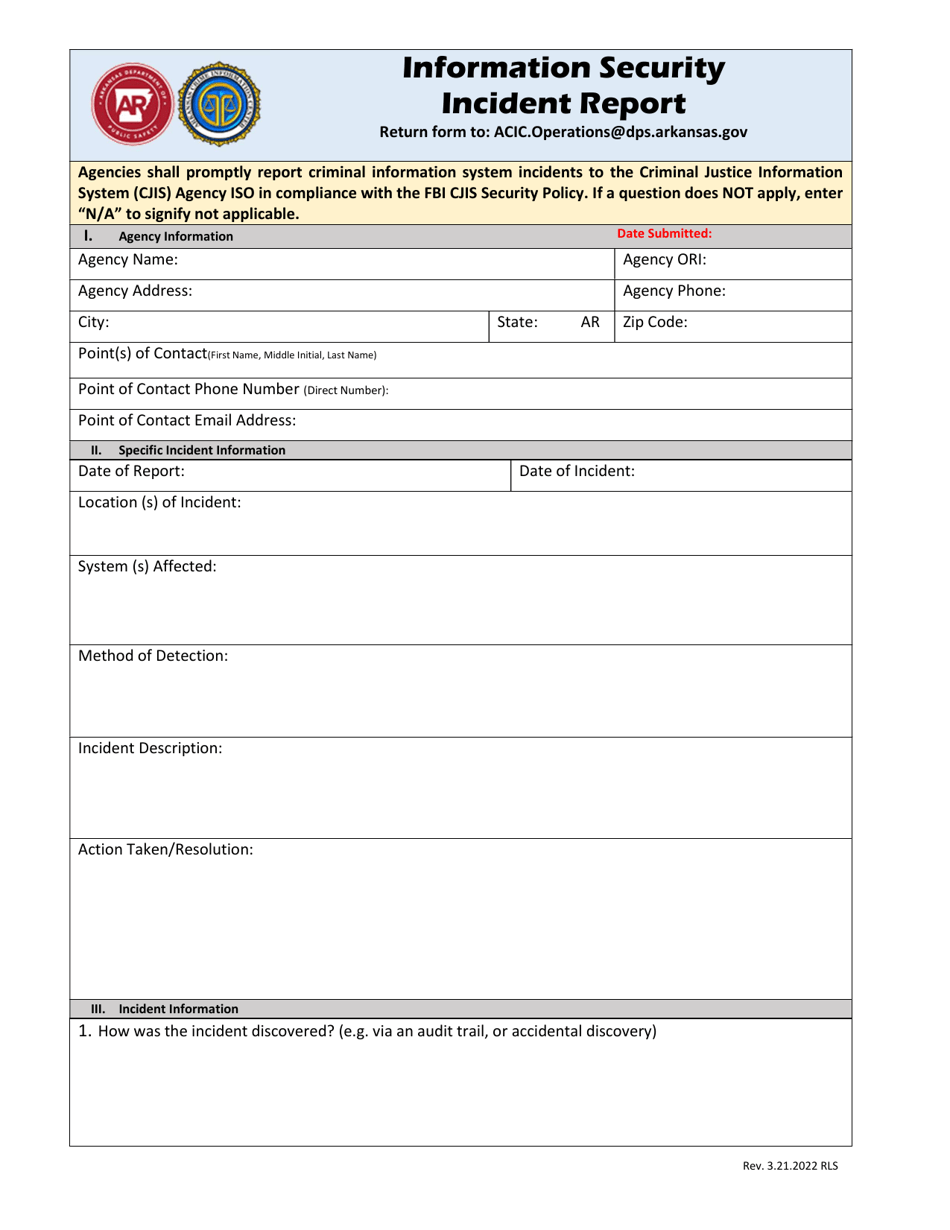
Information Security Incident Report - Arkansas
Information Security Incident Report is a legal document that was released by the Arkansas Department of Public Safety - a government authority operating within Arkansas.
FAQ
Q: What is an information security incident report?
A: An information security incident report is a document used to report any unauthorized (or suspicious) access to, disclosure of, or disruption of information or information systems.
Q: Why is it important to report information security incidents?
A: Reporting information security incidents is crucial because it helps in identifying and addressing potential security vulnerabilities or breaches in order to prevent further damage.
Q: Who should report information security incidents?
A: Anyone who suspects or identifies an information security incident should report it immediately to their organization's designated incident response team or security contact.
Q: How do I report an information security incident?
A: To report an information security incident, follow your organization's established procedures, which may involve contacting the IT department or security team, filling out a specific incident report form, or reporting through a designated incident management system.
Q: What information should be included in an information security incident report?
A: An information security incident report should include details such as the date and time of the incident, a description of what happened, any evidence or artifacts related to the incident, and contact information for the person reporting the incident.
Q: Are all information security incidents considered serious?
A: Not all information security incidents are equally serious. Some incidents may have minimal impact, while others can have severe consequences. It's important to report and assess each incident to determine the appropriate response.
Q: What happens after an information security incident is reported?
A: After an information security incident is reported, it is typically investigated by the incident response team or security professionals. They will assess the incident's severity, gather additional information, and take appropriate action to mitigate the impact and prevent future incidents.
Q: Can I report an information security incident anonymously?
A: Anonymity in reporting information security incidents depends on your organization's policies and procedures. Some organizations allow anonymous reporting, while others may require you to identify yourself when reporting an incident.
Q: What are some examples of information security incidents?
A: Examples of information security incidents include unauthorized access to or theft of confidential data, malware infections, phishing attacks, denial of service attacks, or physical theft or loss of devices containing sensitive information.
Q: Can individuals outside of an organization report information security incidents?
A: While it's preferable for individuals within an organization to report information security incidents, some organizations may have channels for external parties to report incidents, such as customers or vendors.
Q: How can I learn more about information security incident response?
A: To learn more about information security incident response, you can consult resources such as your organization's security policies and protocols, industry best practices, or seek training and certifications in incident response.
Form Details:
- Released on March 21, 2022;
- The latest edition currently provided by the Arkansas Department of Public Safety;
- Ready to use and print;
- Easy to customize;
- Compatible with most PDF-viewing applications;
- Fill out the form in our online filing application.
Download a fillable version of the form by clicking the link below or browse more documents and templates provided by the Arkansas Department of Public Safety.