Security Policy Templates
A comprehensive security policy is vital for any organization to ensure the protection of sensitive information, prevent data breaches, and safeguard against potential threats. Our security policy collection offers a wide range of documents that cover various aspects of security measures and protocols.
From cheat sheets, templates, and checklists to regulatory requirements and audit guidelines, our diverse range of security policy documents caters to the unique needs of different industries and organizations.
By implementing effective security policies, you can establish clear guidelines and practices to manage risks, address vulnerabilities, and maintain compliance with industry standards. Our collection covers a broad spectrum of security areas, including network security, physical security, information security, and more.
Whether you are an IT professional, a business owner, or a security officer, our security policy collection provides valuable resources and insights to help you enhance your organization's security posture. Stay informed and take proactive measures to protect your assets, maintain confidentiality, and mitigate potential security threats.
With our extensive selection of security policy documents, you can confidently navigate the complex landscape of security requirements and ensure the utmost protection of your organization's sensitive information. Safeguard your data, secure your systems, and fortify your defenses with our comprehensive security policy collection.
Documents:
10
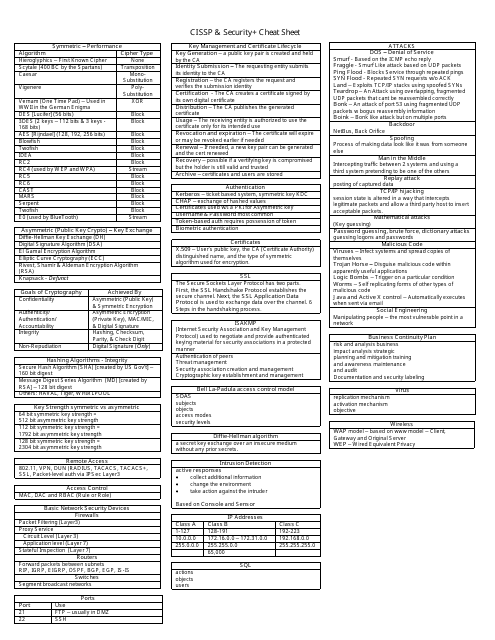
This document is a cheat sheet for the CISSP and Security+ certifications, providing quick reference information and tips for exam preparation.
This document is a template that is used to assess vulnerabilities in a system or network. It provides a structured approach to identify and analyze potential weaknesses, allowing for the development of effective mitigation strategies.
This document provides a report on security awareness conducted by Sans, a trusted organization in the field of cybersecurity. It highlights key findings, trends, and recommendations to enhance security awareness.
This form is used for requesting exceptions to security policies and standards in the state of California.
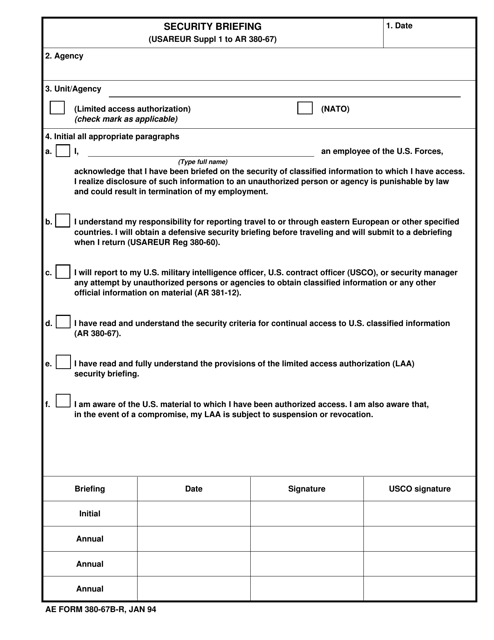
This document is for conducting a security briefing in the U.S. Army. It provides guidelines and procedures for ensuring the security of sensitive information.
This document provides guidelines and best practices for enhancing the cybersecurity of industrial control systems using defense-in-depth strategies. It helps to protect critical infrastructure from cyber threats.
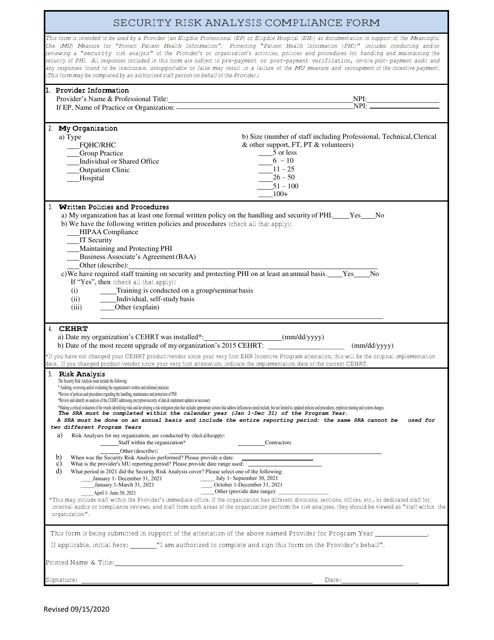
This form is used for conducting a security risk analysis to ensure compliance with regulations in Alabama.
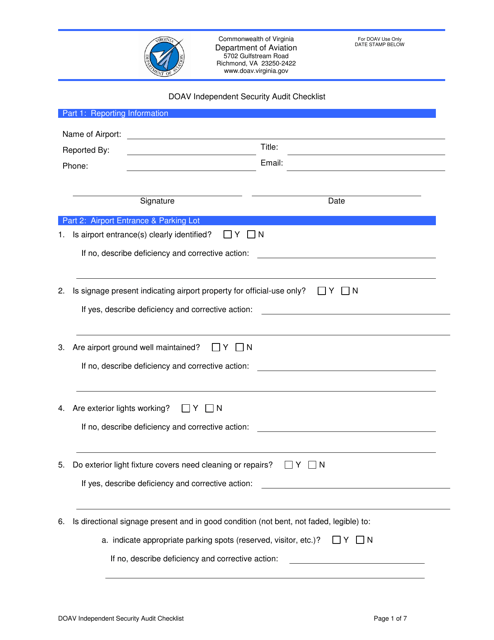
This document is a checklist for conducting an independent security audit in Virginia. It provides guidance on evaluating the security measures in place and ensuring compliance with relevant laws and regulations.
This document outlines the security measures and protocols implemented by the City of Houston, Texas to protect its residents, infrastructure, and sensitive information. It provides a detailed plan for ensuring the safety and confidentiality of city operations.