Security Measures Templates
Are you looking to enhance the security of your organization or facility? Look no further than our comprehensive collection of security measures. Our carefully curated selection of documents encompasses a wide range of topics related to security measures, ensuring that you find the resources you need to protect your assets.
From termination statements to emission security assessments and countermeasures reviews, our collection covers it all. We understand that security needs vary across different industries and regions, which is why we offer documents such as the Request for Approval of Alternative Security Measure specific to the state of Florida and the Marijuana Retailer Inspection Checklist designed for businesses in Oregon.
Whether you need to implement an access control plan or explore various security options for your organization, our collection provides you with the guidance and information you need. By browsing through our documents, you can gain insights into the best practices for securing your premises and preventing unauthorized access.
We understand the importance of maintaining the highest possible security standards, which is why our documents are meticulously crafted to meet the latest industry standards and regulations. Our security measures collection is continuously updated to ensure that you have access to the latest information and recommendations.
Investing in security measures is an investment in the safety and well-being of your organization, employees, and customers. Take advantage of our extensive collection of security measures to optimize your security protocols and mitigate potential risks. Whether you're looking for guidance on implementing specific security measures or seeking inspiration for strengthening your overall security framework, our documents are here to guide you every step of the way.
Documents:
45
This form is used for agreeing to protect classified information and not to disclose it without authorization.
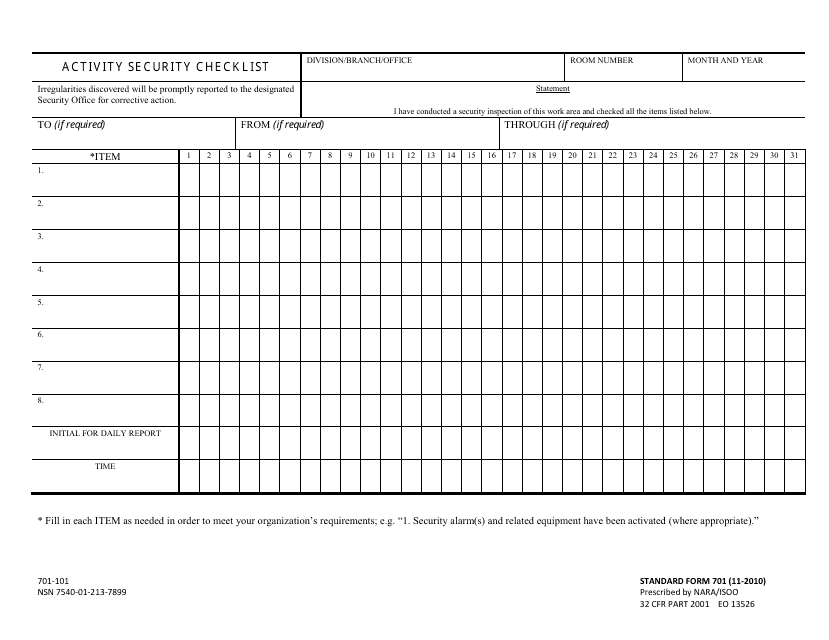
This form is used for conducting an activity security checklist, which is designed to ensure that proper security measures are in place and being followed. It is used to document the completion of security procedures and is typically used in government and military organizations.
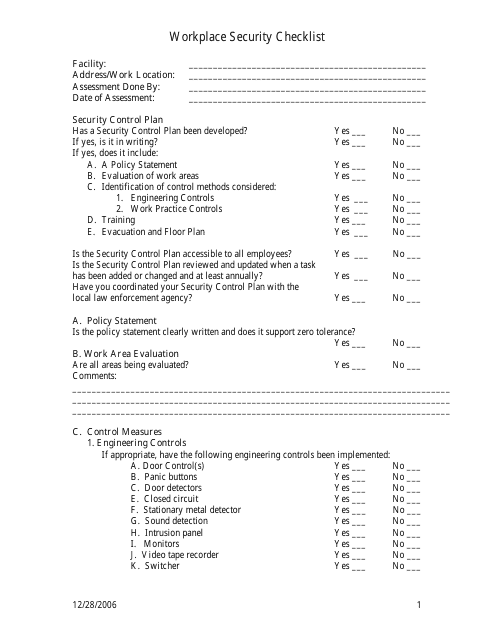
This document is a Workplace Security Checklist Template that can be used to assess the security measures and protocols in place at a workplace. It covers various areas such as access control, emergency preparedness, and physical security measures to ensure a safe and secure working environment.
This document is a template that is used to assess vulnerabilities in a system or network. It provides a structured approach to identify and analyze potential weaknesses, allowing for the development of effective mitigation strategies.
This document provides a report on security awareness conducted by Sans, a trusted organization in the field of cybersecurity. It highlights key findings, trends, and recommendations to enhance security awareness.
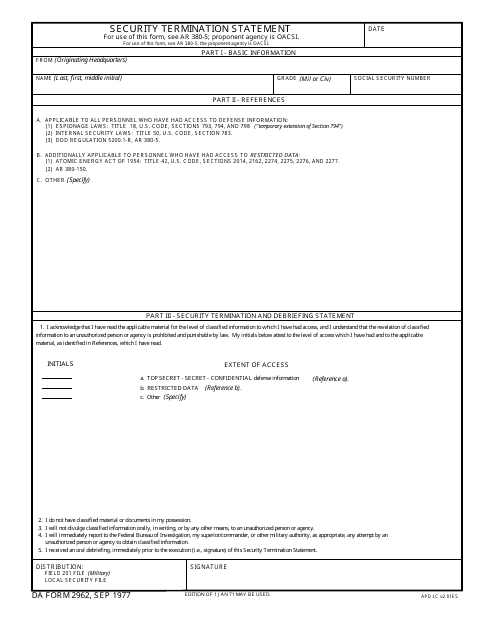
This form is used for submitting a security termination statement in the military.
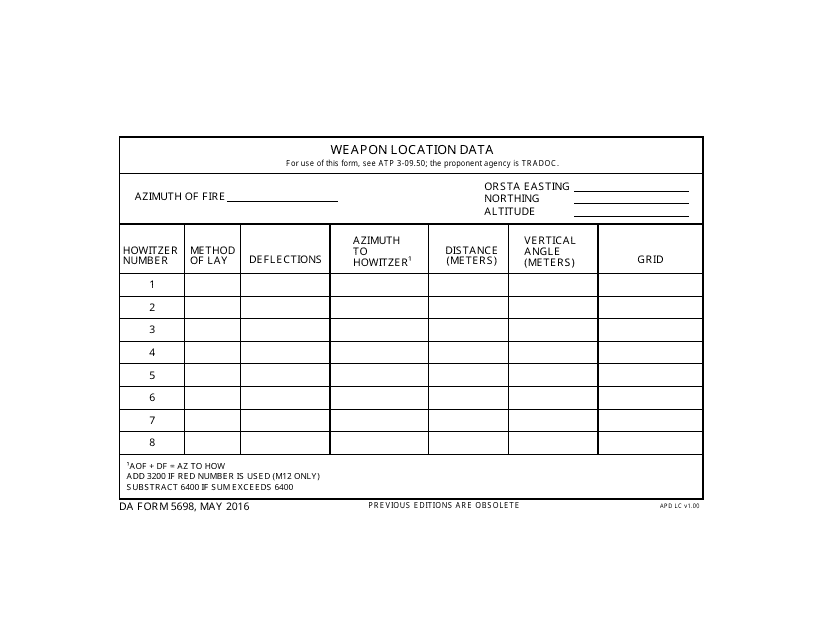
This form is used for capturing and organizing information about the location of weapons.
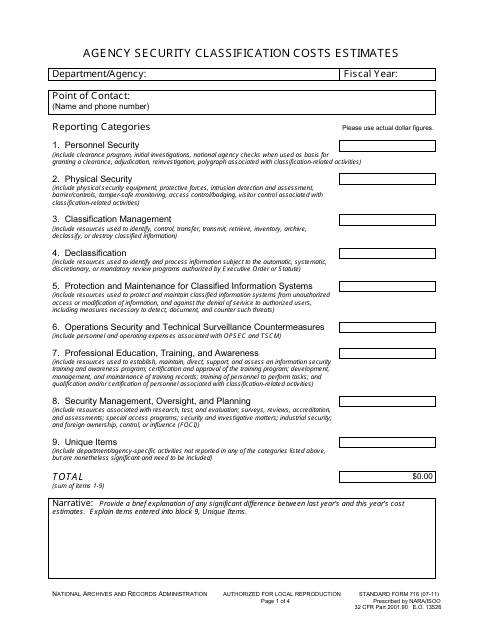
This form is used for estimating the costs associated with agency security classification.
This document is for siluriformes fish farmers and processors to create a food defense plan and implement security measures to protect their products.
This document is used for creating a Food Defense Plan that outlines security measures for protecting food from intentional contamination.
This document provides a template for creating a court security plan in the state of Arkansas. It outlines the necessary measures and procedures to ensure the safety and security of the court and its premises.
This document provides a checklist to help organizations in Colorado prevent and address workplace violence incidents.
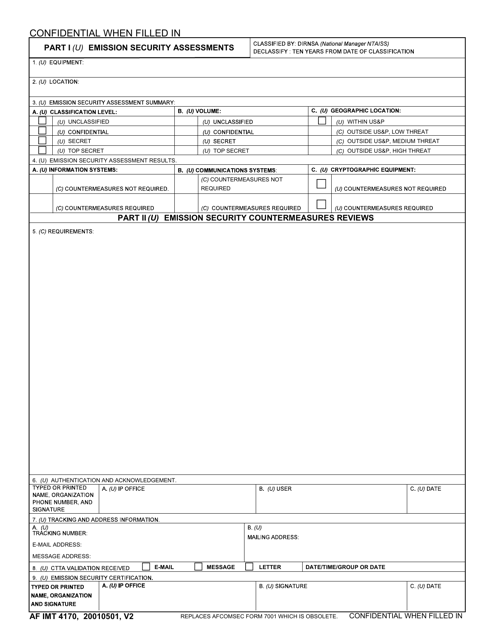
This Form is used for conducting Emission Security Assessments and Emission Security Countermeasures Reviews.
This form is used for applying to the Industrial Hemp Program as a grower in Arizona.
This document is for maintaining the confidentiality of information in the state of Arkansas. It outlines the terms and conditions for keeping sensitive information secure.
This form is used for requesting authorization to enter a close-in security area.
This handbook provides guidance on how to protect private and personal information from unauthorized access or disclosure. It covers best practices for safeguarding sensitive personally identifiable information.
This document is a request for the reallocation of homeland security grants in Tennessee. It is used to redistribute funds to address specific security needs.
This document provides guidance on how to handle and respond to bomb threats in Tennessee. It serves as a reference card for individuals and organizations to effectively deal with such situations.
This type of document is a security addendum for the Federal Bureau of Investigation's Criminal Justice Information Services in New Hampshire.
This document provides a checklist for inspecting marijuana retailers in Oregon. It covers various aspects of compliance and regulations that must be met by these businesses.
This document provides insights from 15 years of research on the impacts of metal detector use in schools. It discusses the effects and benefits of implementing metal detectors to improve school safety and prevent violence.
This form is used for conducting a security risk analysis to ensure compliance with regulations in Alabama.
This document is a checklist for conducting an independent security audit in Virginia. It provides guidance on evaluating the security measures in place and ensuring compliance with relevant laws and regulations.
This document provides a checklist for individuals in West Virginia to follow when dealing with phone threats. It offers guidance on how to respond to and report phone threats, promoting safety and security.
This document is for applying for a grant for loss prevention initiatives in the state of Montana.
This Form is used for submitting an Access Control Plan to the City of Fort Worth, Texas.
This document is an application for a low voltage security alarm in the City of Orlando, Florida.
This document outlines the security measures and protocols implemented by the City of Houston, Texas to protect its residents, infrastructure, and sensitive information. It provides a detailed plan for ensuring the safety and confidentiality of city operations.
This document provides a checklist for assessing the security measures in place at courthouses in Arizona. It helps to ensure the safety of individuals and the proper security protocols are followed.
This Form is used for requesting court security video footage from the County of San Bernardino, California.
This form is used for completing an entrance checklist for crisis nurseries in California. The checklist is designed to ensure that all necessary requirements are met before admitting a child to a crisis nursery facility.
This document is a certificate that ensures the proper security measures are in place during the administration of the New York State Test.