Employee Privacy Templates
Employee privacy is a fundamental aspect of the employer-employee relationship. It refers to the protection of an employee's personal information and maintaining their right to privacy within the workplace. Organizations understand the importance of safeguarding employee privacy to ensure trust, maintain legal compliance, and foster a positive work environment. This collection of documents, also known as employee privacy policies or guidelines, provides a comprehensive framework to address the various aspects of employee privacy. These documents help employers establish clear guidelines on how employee information is handled, stored, and protected. They cover a range of topics, such as social media and electronic device monitoring agreements, authorization for the release of medical information, and agreements related to the privacy and security of protected health, confidential, and sensitive information. By implementing these documents, employers can demonstrate their commitment to respecting employee privacy rights while balancing the need for workplace security and compliance.
Documents:
5
This form is used for implementing a social media and electronic device monitoring agreement in the state of Washington. It outlines the terms and conditions of monitoring employee's social media accounts and electronic devices in the workplace.
This Form is used for employees in Indiana to give authorization for the release of their medical information. It allows employers to access and obtain necessary medical records for various purposes such as insurance claims or disability accommodations.
This document is used for employees in Kentucky to agree to protect the privacy and security of protected health, confidential, and sensitive information.
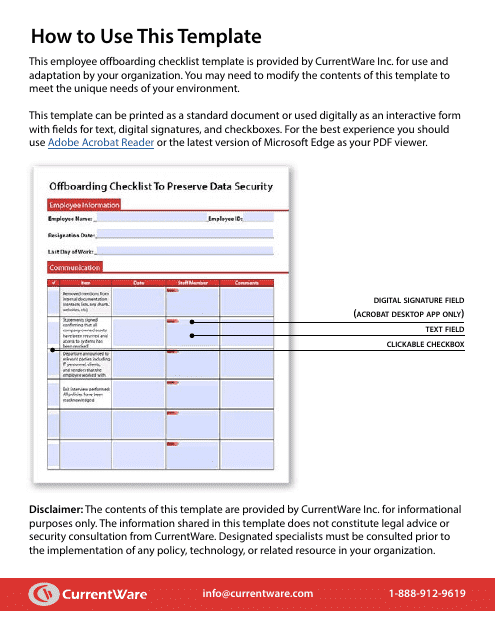
This document provides a comprehensive list of tasks to be completed during the process of an employee leaving an organization, with a focus on maintaining data security. It includes crucial steps like safeguarding sensitive information and proper handoff procedures.