Risk Assessment Checklist Template
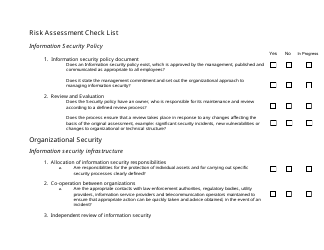
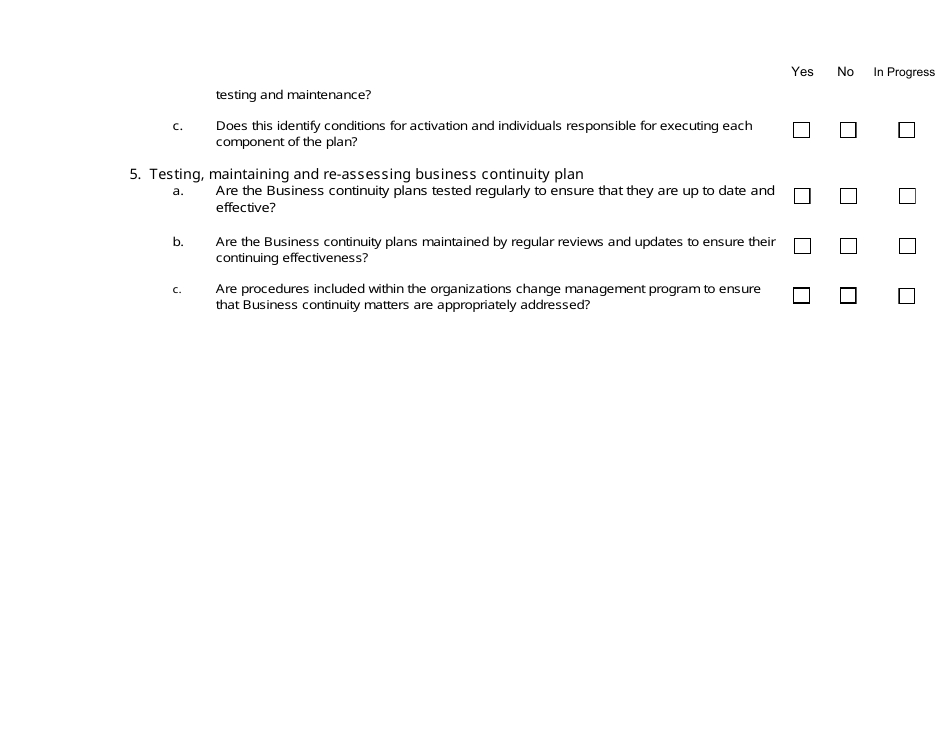
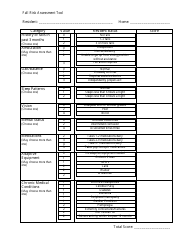
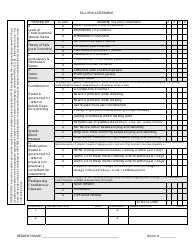
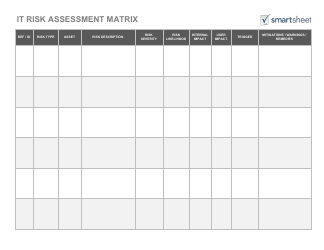
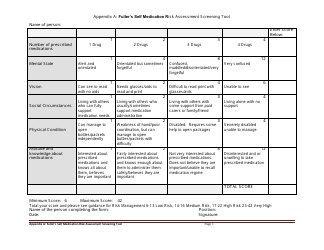
A Risk Assessment Checklist Template is a tool used to evaluate potential risks and hazards in various areas such as workplace, project management, or event planning. It serves as a guide to identify and assess potential risks and develop appropriate mitigation strategies. By using this template, individuals or organizations can ensure that they have considered all the possible risks and taken necessary precautions to minimize them.
The Risk Assessment Checklist Template is typically filed by the organization or the designated risk assessment team within the organization. This can vary depending on the specific policies and procedures followed by the organization. The purpose of the checklist is to identify and evaluate potential risks in order to implement appropriate risk mitigation strategies.
FAQ
Q: What is a risk assessment checklist?
A: A risk assessment checklist is a tool used to identify and evaluate potential risks and hazards in a specific environment or activity.
Q: Why is a risk assessment checklist important?
A: A risk assessment checklist is important because it helps organizations and individuals proactively identify and manage potential risks, ensuring the safety and well-being of people and the protection of assets.
Q: What should be included in a risk assessment checklist?
A: A risk assessment checklist should include a thorough evaluation of potential hazards, identification of people at risk, assessment of likelihood and severity of risks, controls and precautions in place, and a plan for monitoring and reviewing risks.
Q: How do I use a risk assessment checklist?
A: To use a risk assessment checklist, you should review the checklist and identify potential risks and hazards within the specific context. Then, assess the likelihood and severity of each risk and implement controls and precautions to mitigate those risks.