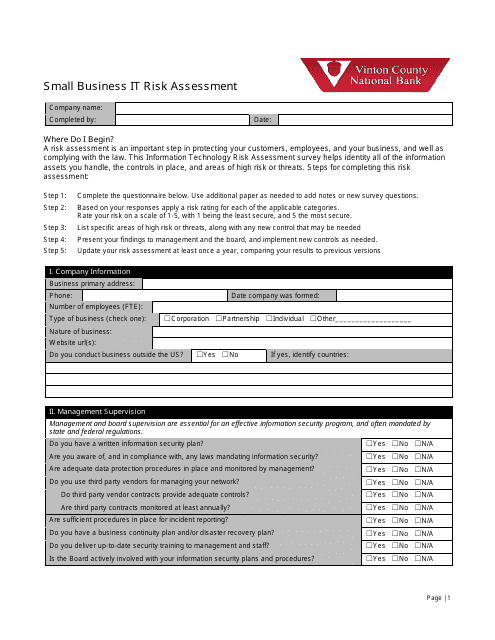
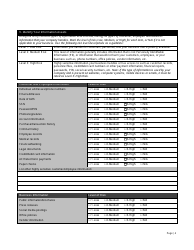
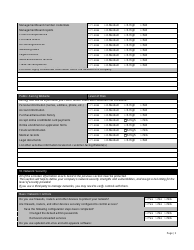
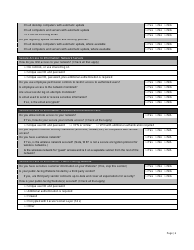
Small Business It Risk Assessment Form - Vinton County National Bank
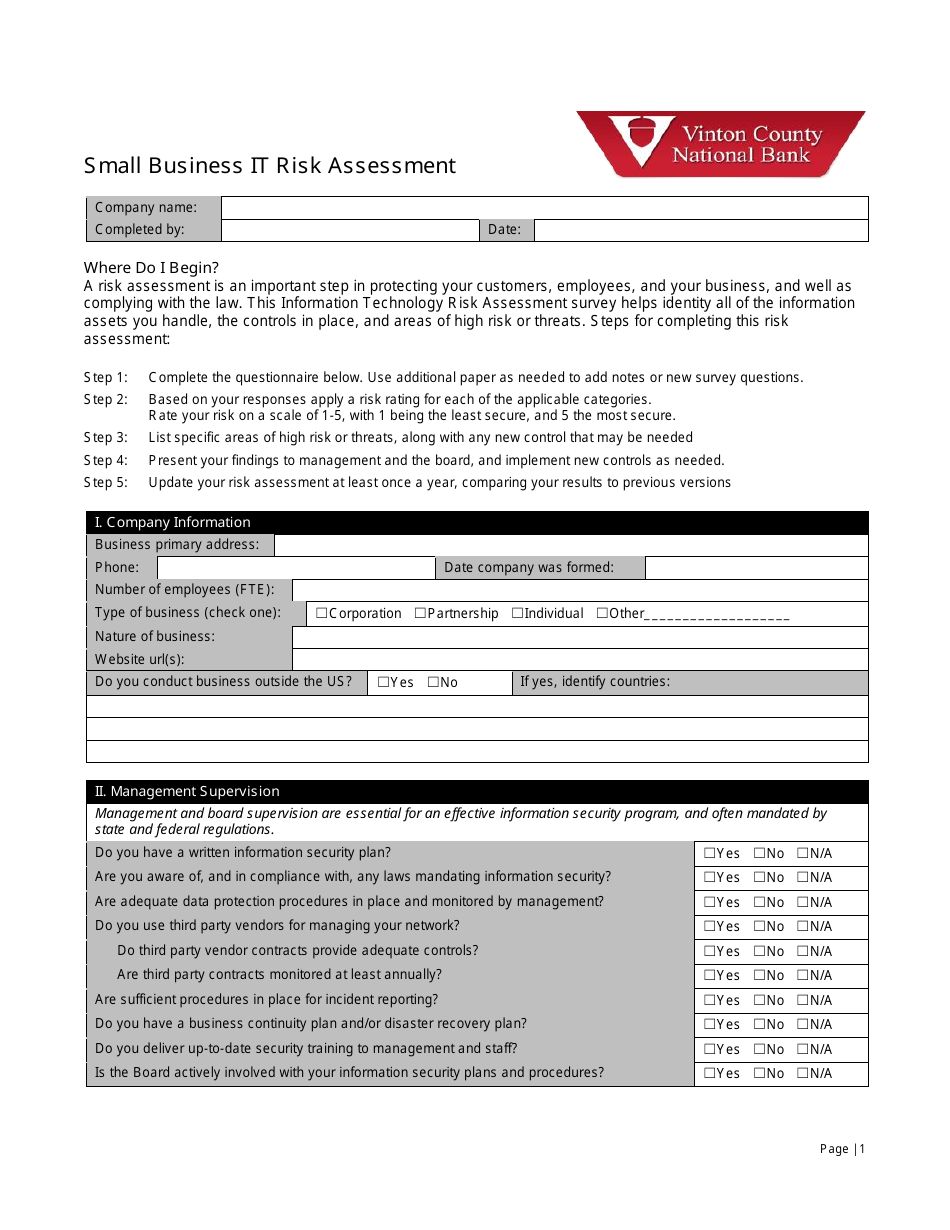
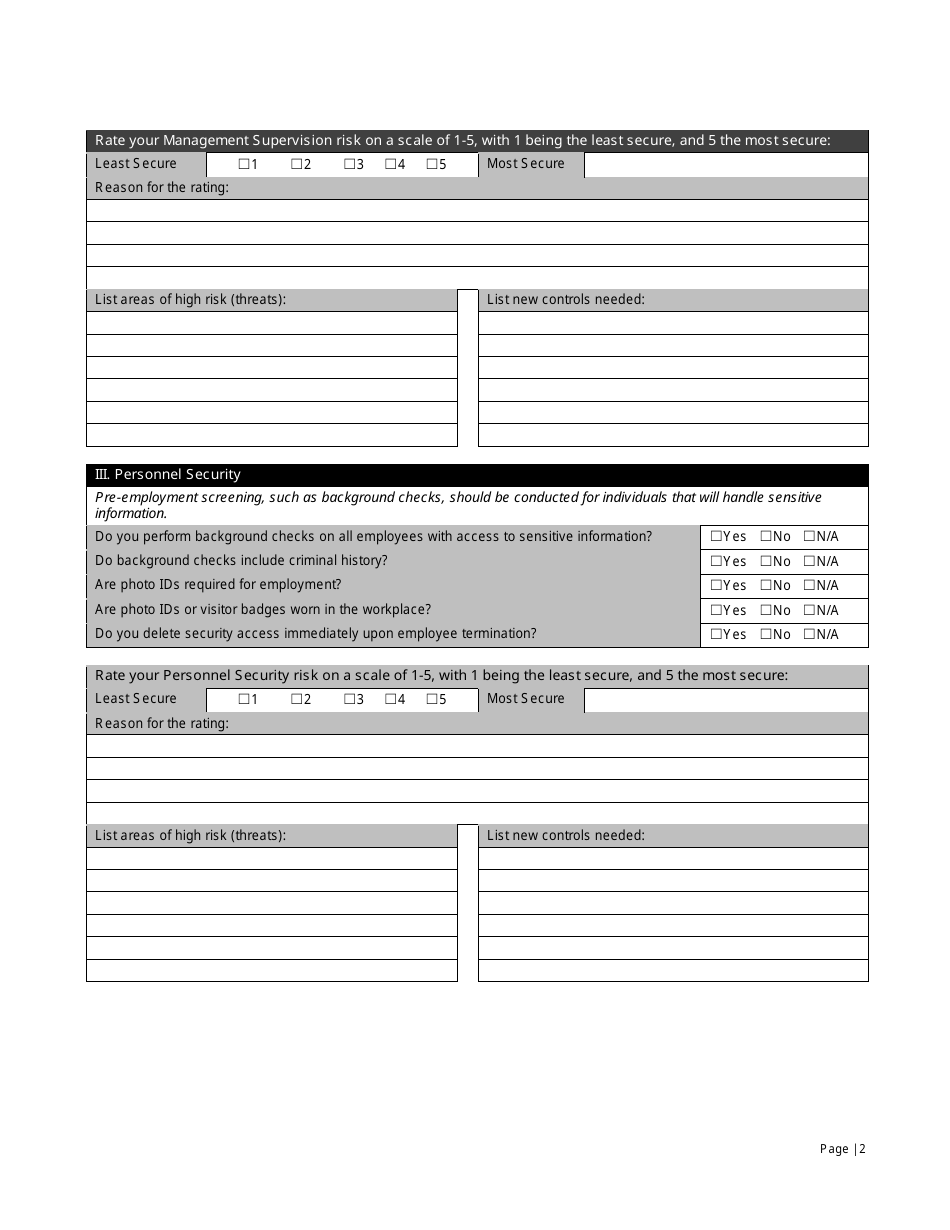
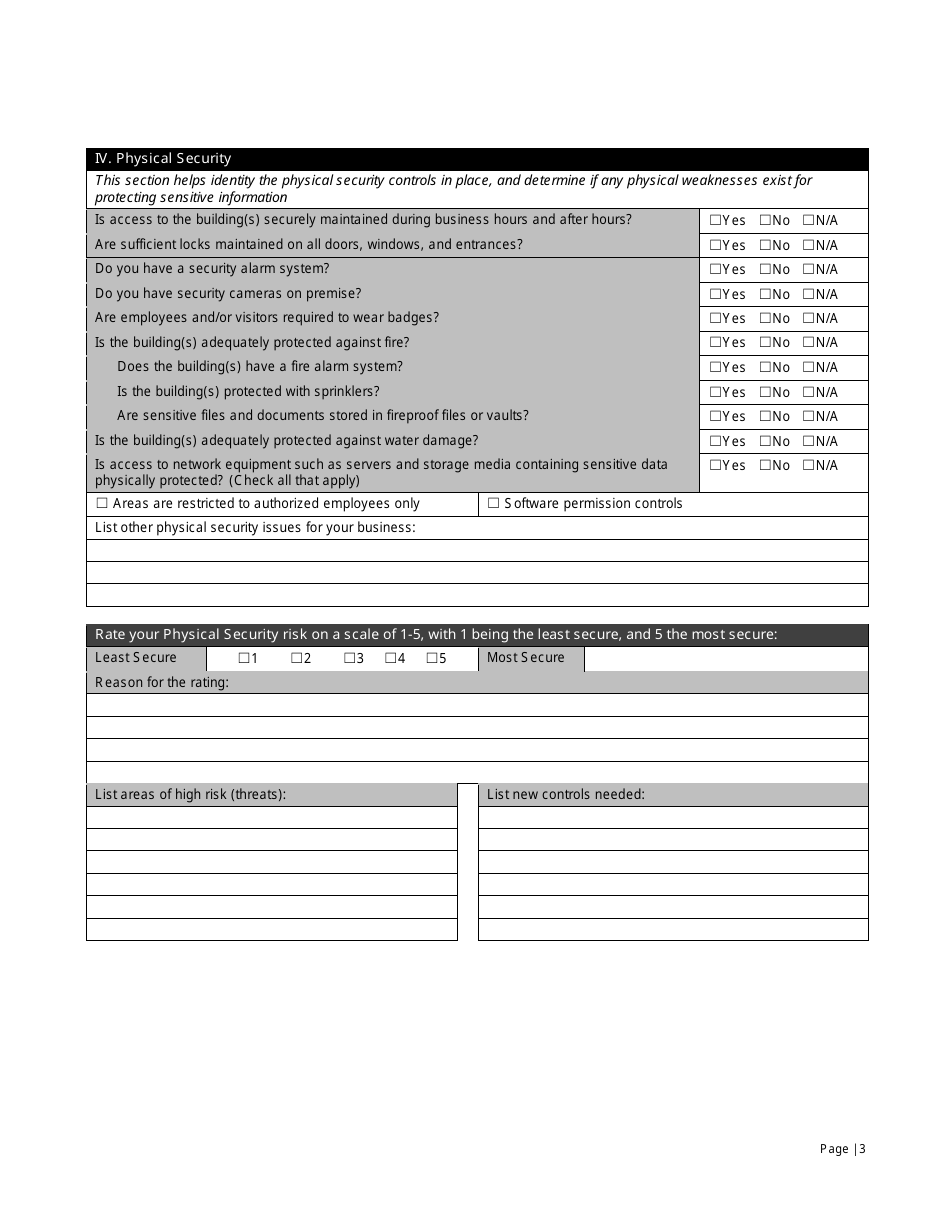
The Small Business IT Risk Assessment Form is used by Vinton County National Bank to assess the potential IT risks faced by small businesses. It helps identify and evaluate any vulnerabilities or weaknesses in their IT systems and create strategies to mitigate those risks.
FAQ
Q: What is the Small Business IT Risk Assessment form?
A: The Small Business IT Risk Assessment form is a tool used by Vinton County National Bank to evaluate the potential risks to small businesses in terms of their IT systems and infrastructure.
Q: Why is a Small Business IT Risk Assessment important?
A: A Small Business IT Risk Assessment is important because it helps identify and prioritize potential risks to a business's IT systems, allowing for the implementation of appropriate security measures to protect against those risks.
Q: Who should use the Small Business IT Risk Assessment form?
A: Small business owners or IT professionals responsible for assessing and managing the IT security of the business should use the Small Business IT Risk Assessment form.
Q: What does the Small Business IT Risk Assessment form include?
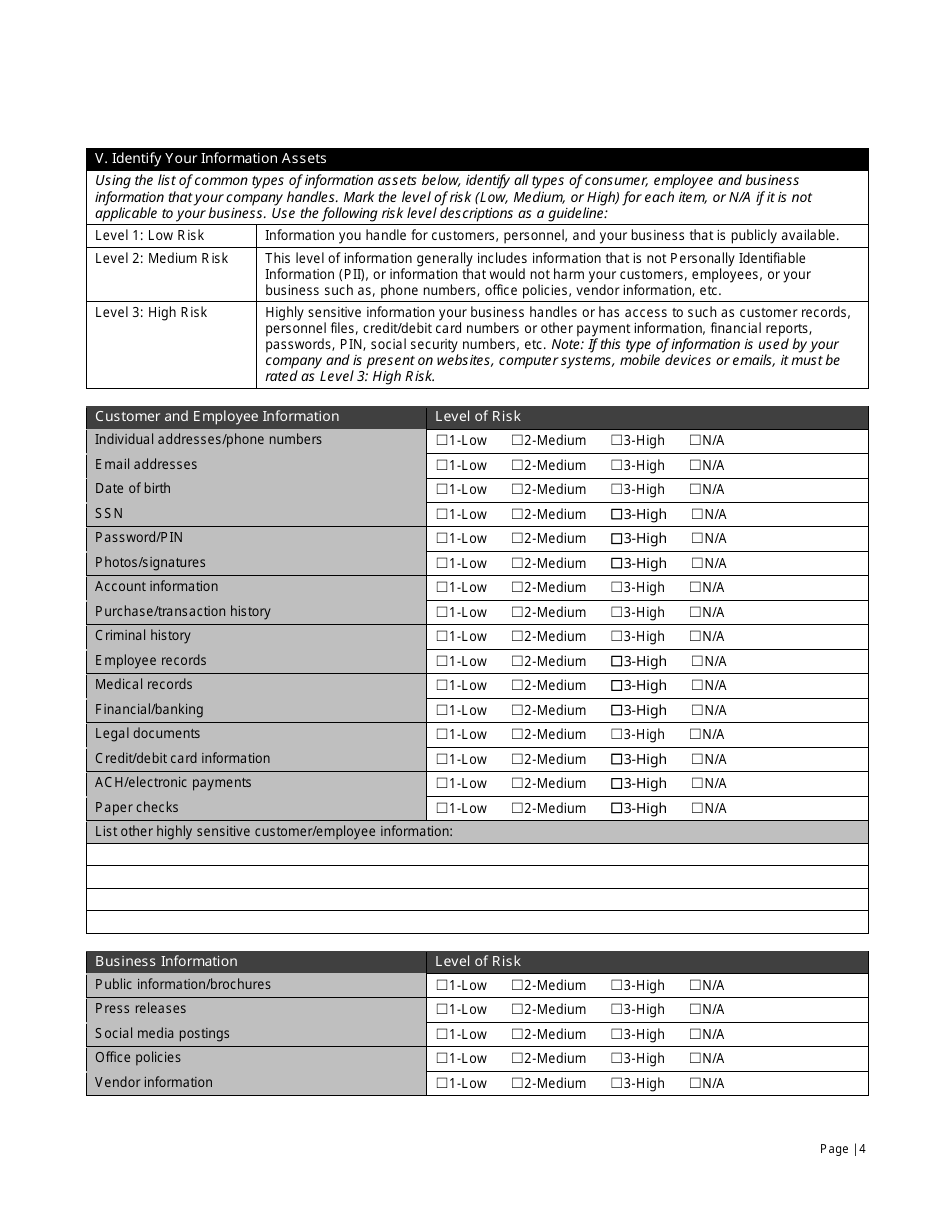
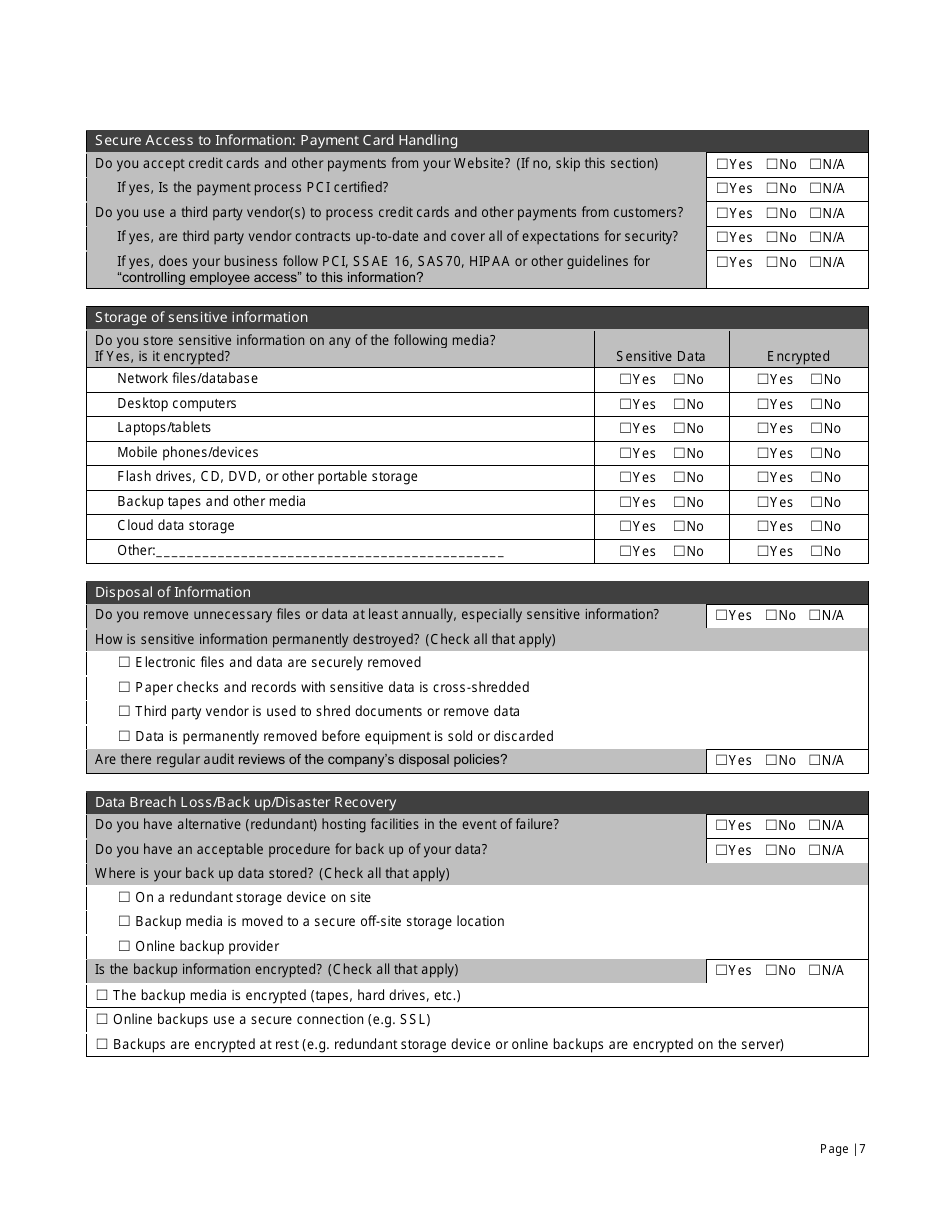
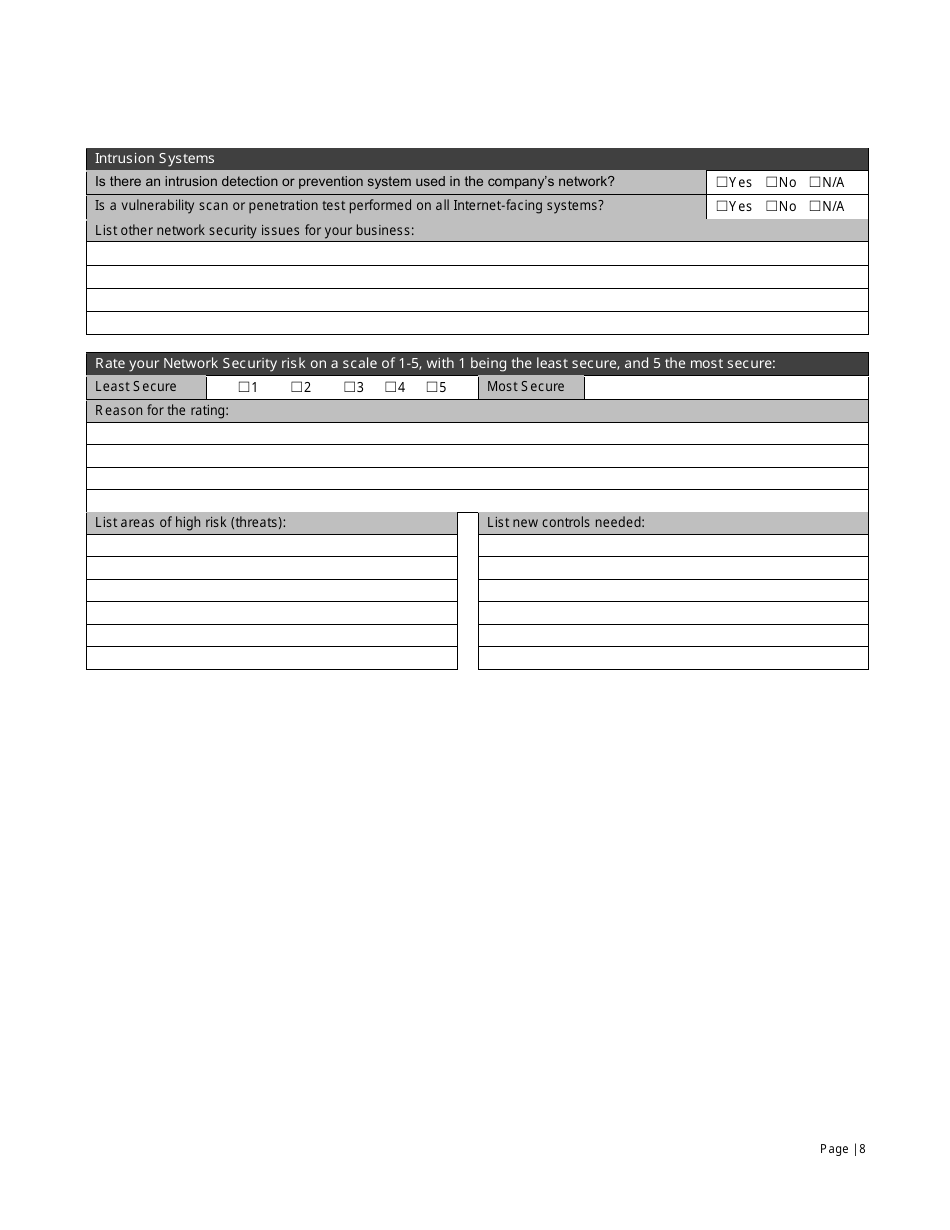
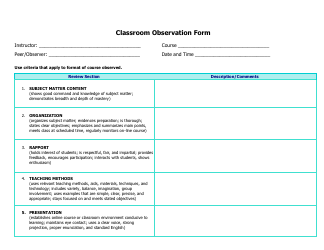
A: The Small Business IT Risk Assessment form typically includes sections to assess the business's hardware and software, network security, data backup procedures, employee training, and disaster recovery plans.
Q: How can the Small Business IT Risk Assessment form be used?
A: The Small Business IT Risk Assessment form can be used as a guide to conduct a comprehensive assessment of a small business's IT risks and to identify areas for improvement in terms of IT security.