Log Monitoring Templates
Log Monitoring, also known as Monitoring Log or Monitor Log, is an essential process for various industries and sectors. It involves the systematic tracking and analysis of log data to ensure the smooth functioning and security of systems and applications.
In today's digital age, businesses generate a vast amount of log data from various sources such as servers, networks, applications, and security devices. These logs contain valuable information about system performance, errors, security incidents, and user activities. By monitoring and analyzing these logs, organizations can gain insights into their infrastructure, identify potential issues, and take proactive measures to enhance their operations.
Log monitoring plays a crucial role in maintaining the overall health and security of an organization's IT environment. It enables businesses to detect and respond to anomalies, such as unauthorized access attempts, system failures, or unusual user behavior. By continuously monitoring logs, organizations can quickly identify and address potential security breaches or operational inefficiencies, mitigating the risk of data breaches, downtime, and financial loss.
Furthermore, log monitoring facilitates compliance with industry regulations and standards. Many sectors, including healthcare, finance, and government, have specific requirements regarding data privacy, security, and incident reporting. By implementing robust log monitoring practices, organizations can demonstrate their compliance and effectively respond to regulatory audits.
Implementing an effective log monitoring solution requires the right tools and practices. Automated log management systems can collect, centralize, and analyze logs from various sources, making it easier to identify patterns, detect anomalies, and generate meaningful insights. These solutions often include customizable dashboards, real-time alerts, and advanced analytics capabilities, empowering organizations to proactively address issues and improve their overall performance.
Whether you refer to it as Log Monitoring, Monitoring Log, or Monitor Log, implementing a comprehensive log monitoring strategy is crucial for any organization. It provides valuable insights into system performance, security incidents, and user activities, enabling businesses to detect and respond to potential issues promptly. By leveraging log monitoring solutions, organizations can enhance their operations, ensure regulatory compliance, and safeguard their valuable data and resources.
Documents:
11
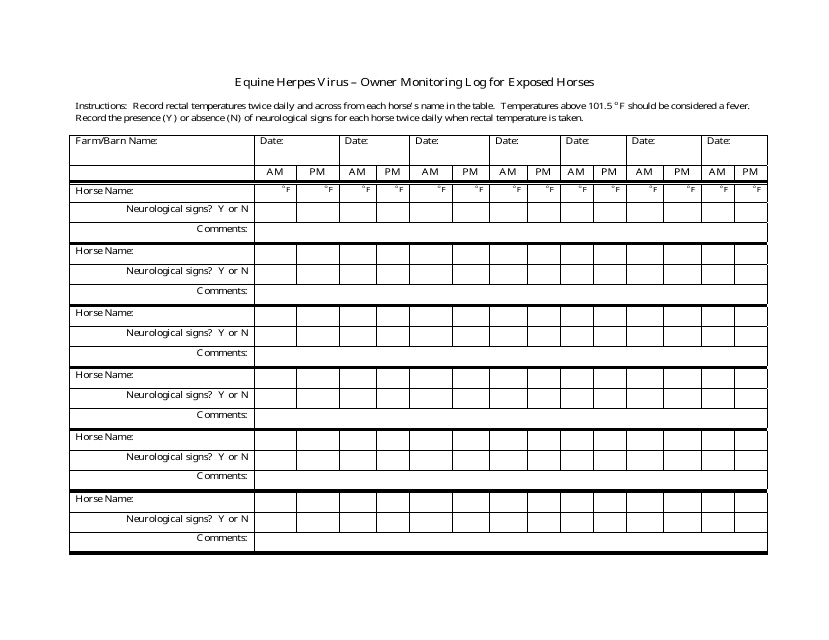
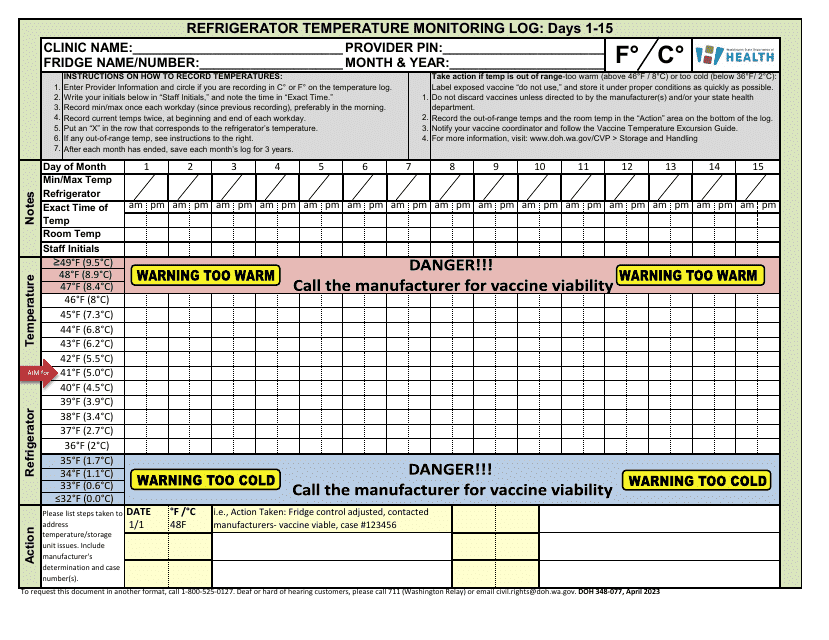
This document is used for monitoring and tracking exposed horses for Equine Herpes Virus in Nevada. It helps horse owners keep a record of potential infections and ensure proper health management.
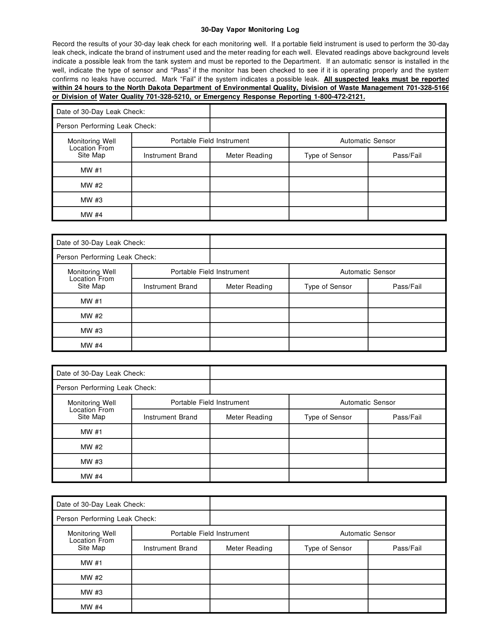
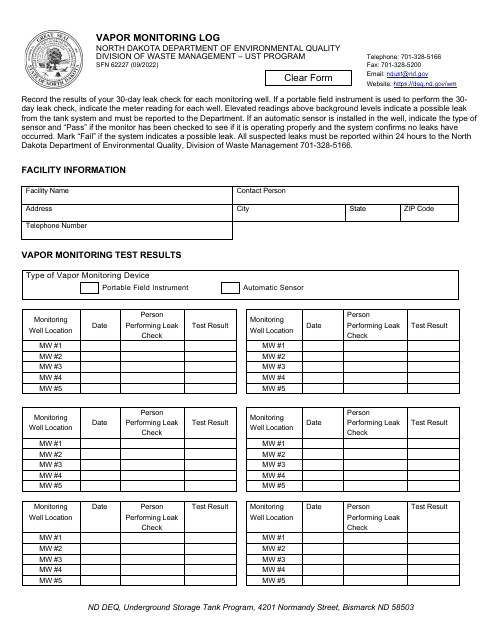
This document is used for keeping track of vapor monitoring for a 30-day period in North Dakota.
This Form is used for logging vapor monitoring activities in North Dakota. It is a record-keeping document for tracking and documenting vapor monitoring data.
This document is a cheat sheet for Splunk, a software platform that allows users to search and analyze machine-generated data. It provides quick reference information and tips for using Splunk effectively.
This document provides a quick reference guide for using Splunk, a platform for analyzing and visualizing machine-generated data. It includes key commands, search syntax, and tips for using Splunk effectively.
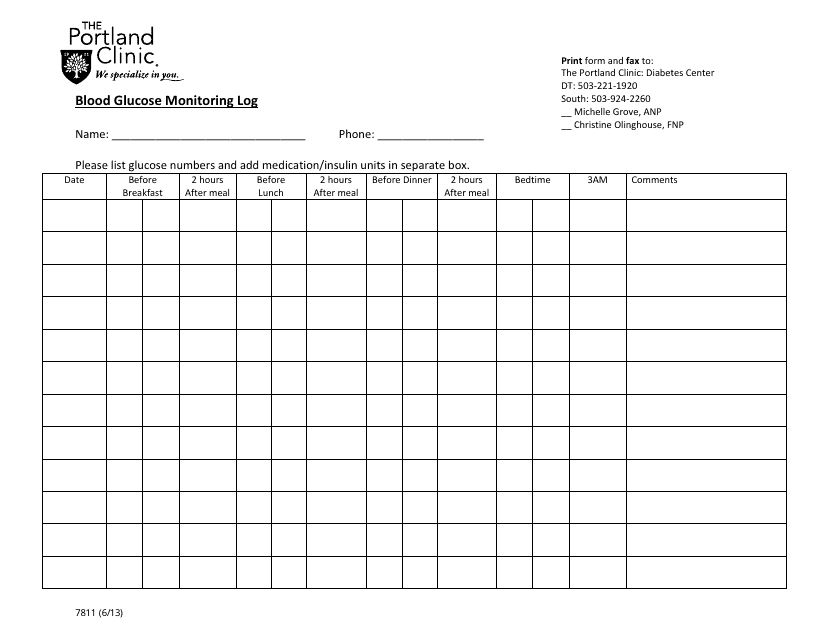
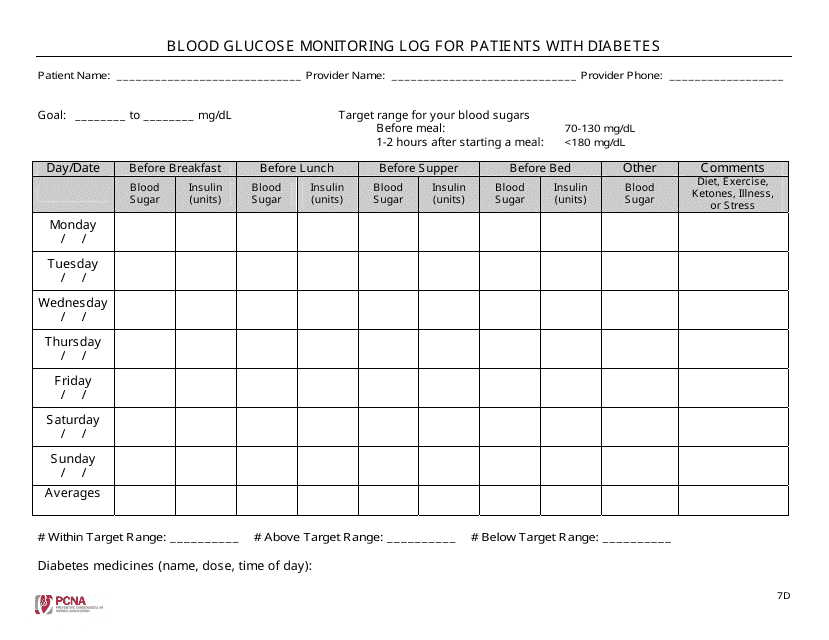
This document is designed for diabetes patients to track and record their blood sugar levels regularly, aiding in managing their condition effectively. It assists medical professionals in adjusting treatment plans based on logged glucose readings.
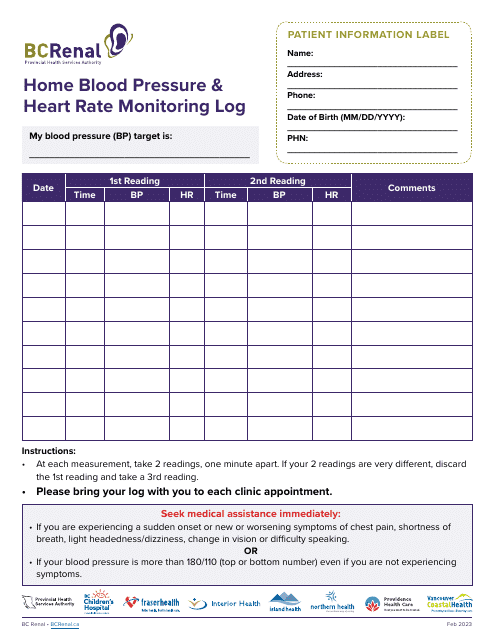
This document is intended for recording and tracking personal blood pressure and heart rate readings at home. It aids in consistently monitoring health status and helps provide valuable data for doctors.