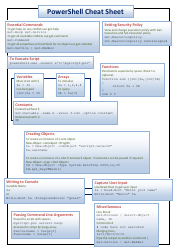
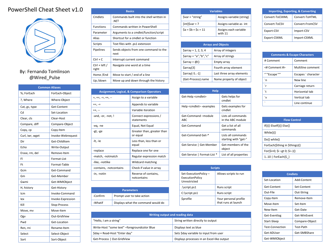
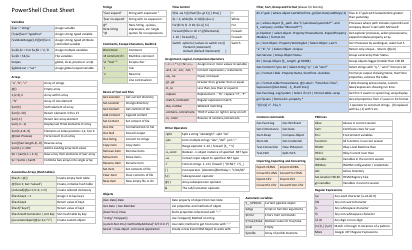
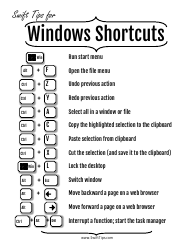
Powershell Active Directory Cheat Sheet
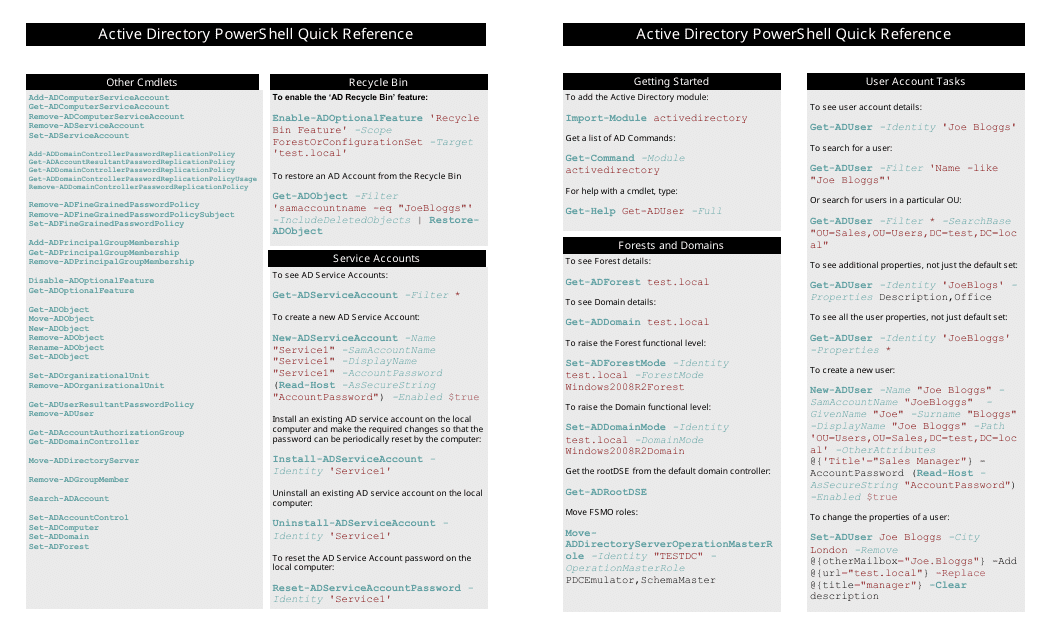
The Powershell Active Directory Cheat Sheet is a document that provides quick reference information and commands for managing Active Directory using PowerShell. It is useful for system administrators and IT professionals who need to perform Active Directory management tasks efficiently.
FAQ
Q: What is PowerShell?
A: PowerShell is a command-line shell and scripting language created by Microsoft.
Q: What is Active Directory?
A: Active Directory is a directory service developed by Microsoft that provides a centralized database for managing and authenticating resources in a network.
Q: What can you do with PowerShell in Active Directory?
A: With PowerShell in Active Directory, you can perform various tasks such as creating users, managing groups, modifying permissions, and querying information.
Q: How do I connect to Active Directory using PowerShell?
A: You can connect to Active Directory using the 'Import-Module ActiveDirectory' command in PowerShell.
Q: What are some useful PowerShell cmdlets for Active Directory?
A: Some useful PowerShell cmdlets for Active Directory include: Get-ADUser, Get-ADGroup, New-ADUser, Set-ADUser, Remove-ADUser, Add-ADGroupMember, and Remove-ADGroupMember.
Q: Is PowerShell the only way to manage Active Directory?
A: No, PowerShell is just one of the ways to manage Active Directory. You can also use tools like Active Directory Users and Computers (ADUC) or Active Directory Administrative Center (ADAC).
Q: Can I automate tasks in Active Directory using PowerShell?
A: Yes, PowerShell is great for automation. You can write scripts or use pre-built scripts to perform repetitive tasks in Active Directory.