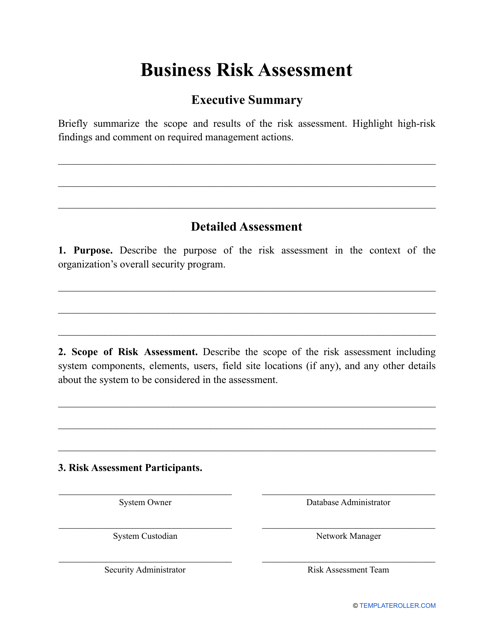
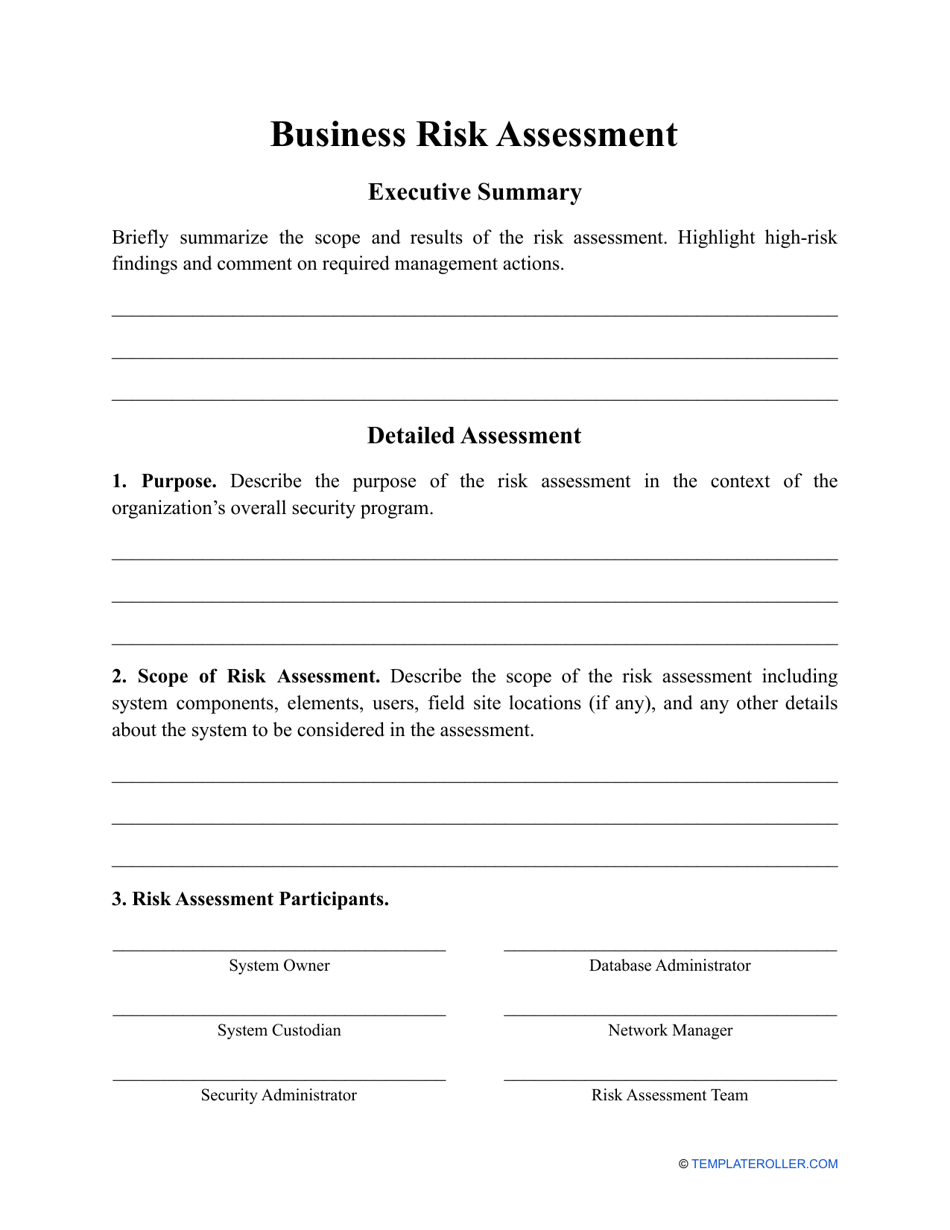
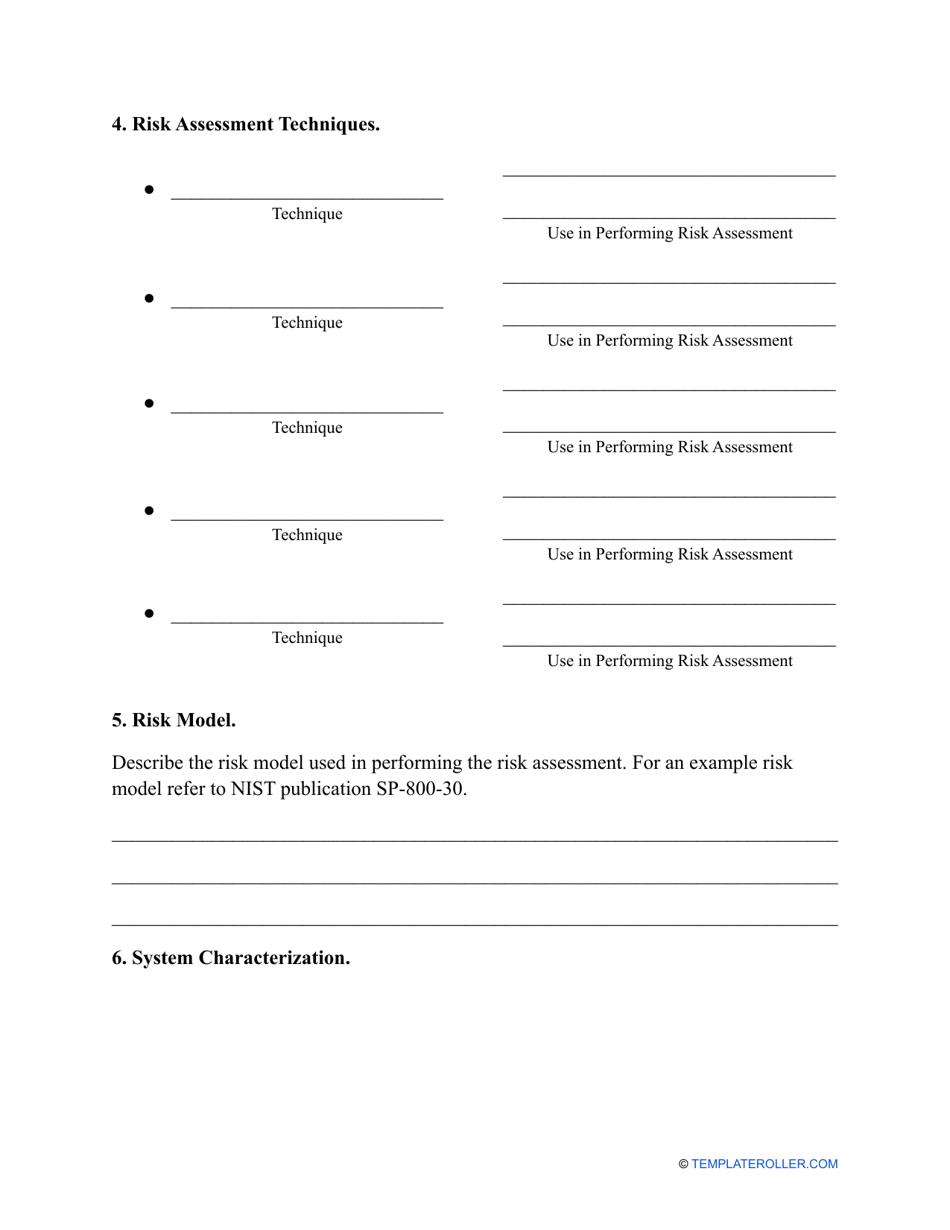
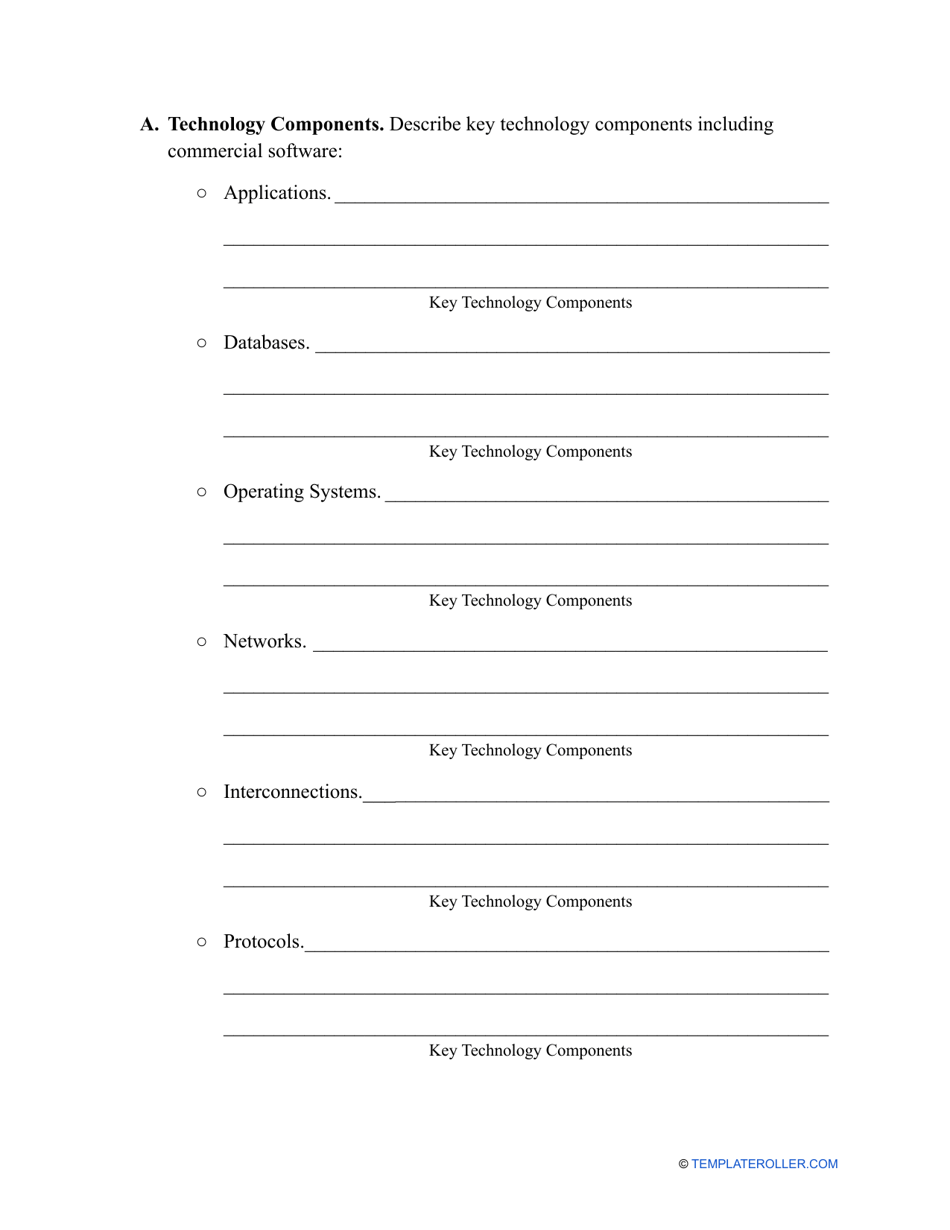
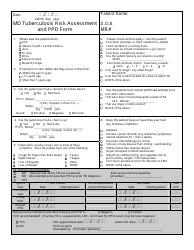
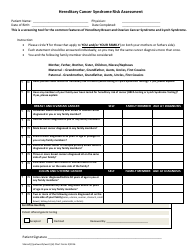
Business Risk Assessment Template
What Is Business Risk Assessment?
A Business Risk Assessment is the process of identifying and evaluating potential risks that can affect the company's well-being. The purpose of this process is to find prospective business hazards and develop strategies that will help to avoid them and cope with them.
It might look like only big companies need a risk assessment since they have larger assets to lose, however, this is not true. A Small Business Risk Assessment helps owners of small companies to determine the potential hazards that can possibly damage their business and slow down the development of their company.
Generally, a risk assessment can be conducted by an employee of the company, or by a consultant specially hired for this purpose. It can be performed at different stages of the company development, or even when an individual is only planning to start a business. Completing a risk assessment can be overwhelming and rather stressful, so if you want to make certain you did not miss anything important you can use our Business Risk Assessment template which can be downloaded below.
How to Perform a Business Risk Assessment?
If you want to perform a Business Risk Assessment but do not know where to start, you can look at our Business Risk Assessment checklist which can help you conduct your inspection:
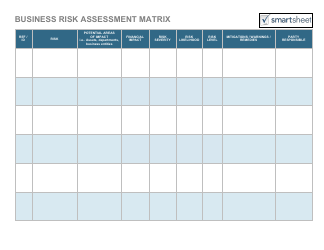
- Identify the Risks . When you perform a Business Risk Assessment first thing you can do is to identify the hazards that can potentially damage your business. Commonly, there are five types of business risks, which include: strategic risks, compliance risks, operational risks, financial risks, and reputational risks. Each one of these risks shall be thoroughly investigated and researched.
- Check What Is at Risk . After you have listed all of the potential risks that can hurt your business, you can try to examine what exactly might be damaged in the worst-case scenario. Knowing what precisely is at risk will help you to develop a more efficient preventive strategy.
- Research the Consequences . Defining the risks and their subjects is only a part of the work, after that, you can try to research what kind of consequences will come into effect if a potentially hazardous situation happens. Knowing the impact can help prepare and develop measures that can be taken to restore the situation.
- Evaluate the Risks . Evaluating all of the risks you have found will help you understand which risks are more likely to happen than others. It can be done in a form of a scale of risks that will help you to understand which risks are high risks since they should be managed more carefully than others.
- Manage the Risks . If you have gathered all of the information listed below you can move to the final part of your Business Risk Assessment. To prevent hazardous situations from happening you can develop strategies or measures, that will decrease the possibility of them happening. In addition to this, to each risk (or group of risks) you can appoint an employee who will be responsible for following the risk preventing strategy and mitigating the risk.
Still looking for a particular template? Take a look at the related templates below: