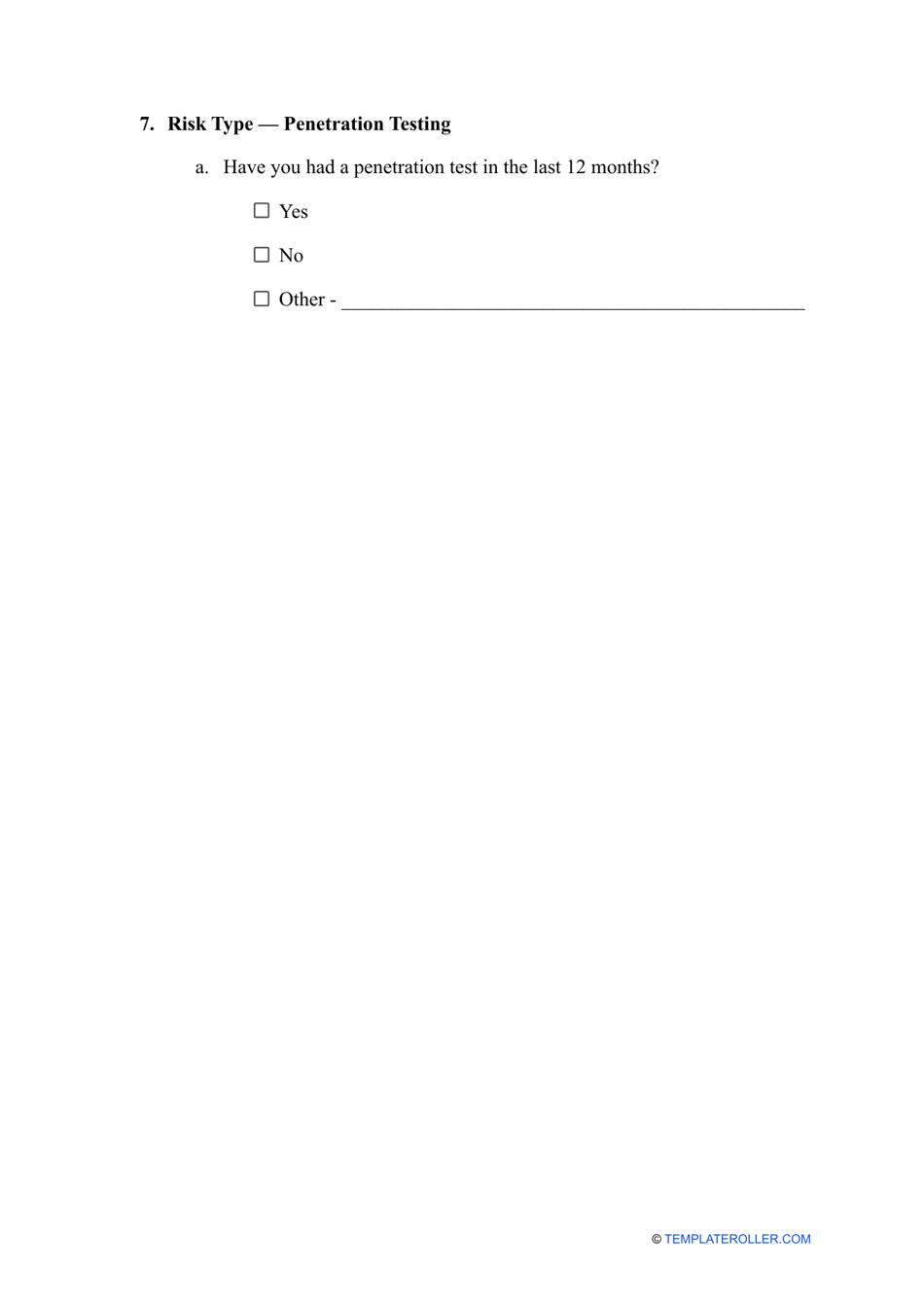Vendor Risk Assessment Template
What Is Vendor Risk Assessment?
A Vendor Risk Assessment is a process of examining and assessing suppliers of goods and services as prospective business partners before entering into agreements with them. Whether you represent a large corporation or just founded a small enterprise, do not sign any contracts with other businesses prior to learning as much about them as you can.
If you make a rash decision and blindly start buying merchandise or services from the company you know little to nothing about, it may bring you severe financial harm and reputation damage you might have to deal with or at least explain to other companies and financial institutions for years. You may download a Vendor Risk Assessment template through the link below.
How to Conduct a Vendor Risk Assessment?
Follow our Vendor Risk Assessment Checklist to find out whether potential suppliers will be a good fit for your organization:
- Identify the company you would like to see as your business partner in the future . It is possible to find these suppliers online or rely on the opinion of the managers of a company you have already done business with - they will recommend a trustworthy and credible entity.
- Perform a background check . You may hire a third-party that conducts screenings for a living or search for necessary details yourself: learn whether the business and the experience they claim to have are legitimate, find out if the company, its owner, and officers have been involved in any legal or financial issues or received bad publicity, and confirm this organization will be able to do the work they are ready to agree to.
- Contact the company to know more about its privacy policy and data security . You need to know the company's regulations regarding data storage, protection against data breaches, and your possible liability in case any details of third parties and consumers end up in the wrong hands, especially if you plan to sign a separate confidentiality agreement.
- Ensure the vendor implements proper disaster recovery protocols - they must be ready to respond quickly and efficiently to natural disasters and cyberattacks in order to continue their day-to-day activities. Ask the management how often they update their business continuity plans and conduct a brief analysis of the methodologies they use.
- Outline a risk management strategy . Even if the vendor seems reliable and you have covered all the bases, there must be escape routes planned: decrease the possibility of damage by constantly monitoring the performance of the business, tracing complaints from third parties and clients, and updating your agreements with the vendor.
- Document the Vendor Risk Assessment process of every company you appraise and create a folder or table to evaluate them based on the criteria listed above . It may be very hard to find a supplier that is prepared to do business with you at the earliest opportunity so keep track of all the advantages and disadvantages of your new potential partner. For instance, you may ignore financial issues you have uncovered in the owner's past if you strongly believe these problems have been dealt with a long time ago and will not influence their company and yours in the months and years to come.
Still looking for a particular template? Take a look at the related templates below: