Nist Risk Assessment Template
What Is NIST Risk Assessment?
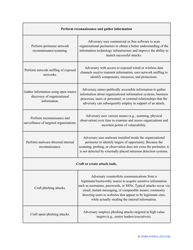
A NIST Risk Assessment refers to a system of evaluating the security of your company following the regulations established by the National Institute of Standards and Technology (NIST). Obligatory for all government contractors and entities that have business deals with the government, this analysis will help you recognize the risks you may face any day of work and prepare your management to deal with security and privacy threats.
Alternate Name:
- NIST Security Risk Assessment.
You can download a printable NIST Risk Assessment template through the link below. You will be able to discover the most vulnerable points in your security system, determine a timeline to collect evidence and find which improvements are possible and affordable, mitigate the negative consequences of any issue the company may encounter, and monitor the safety of the entity in the future.
How to Perform a NIST Risk Assessment?
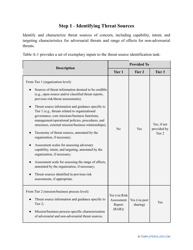
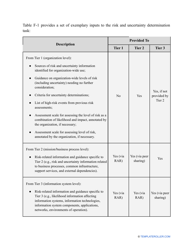
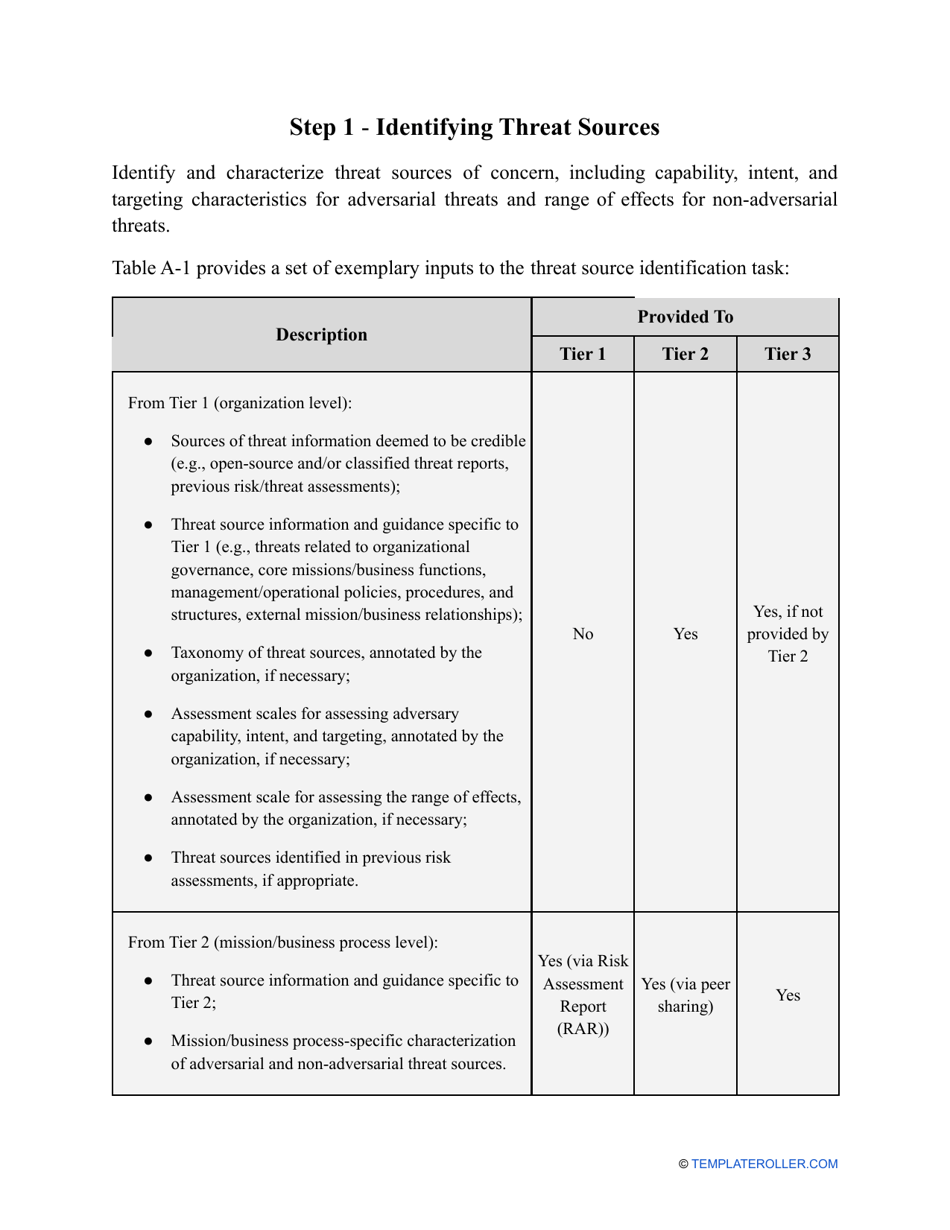
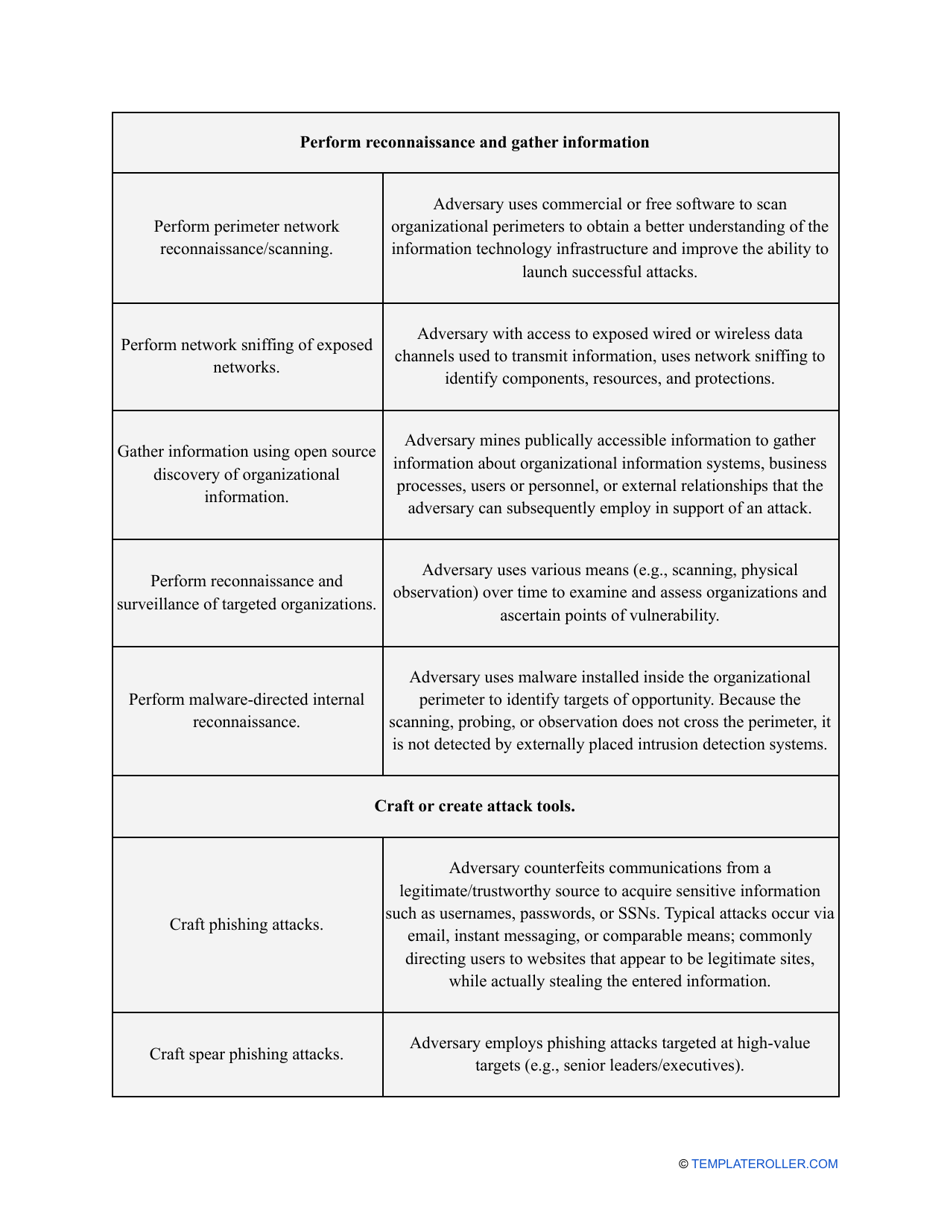
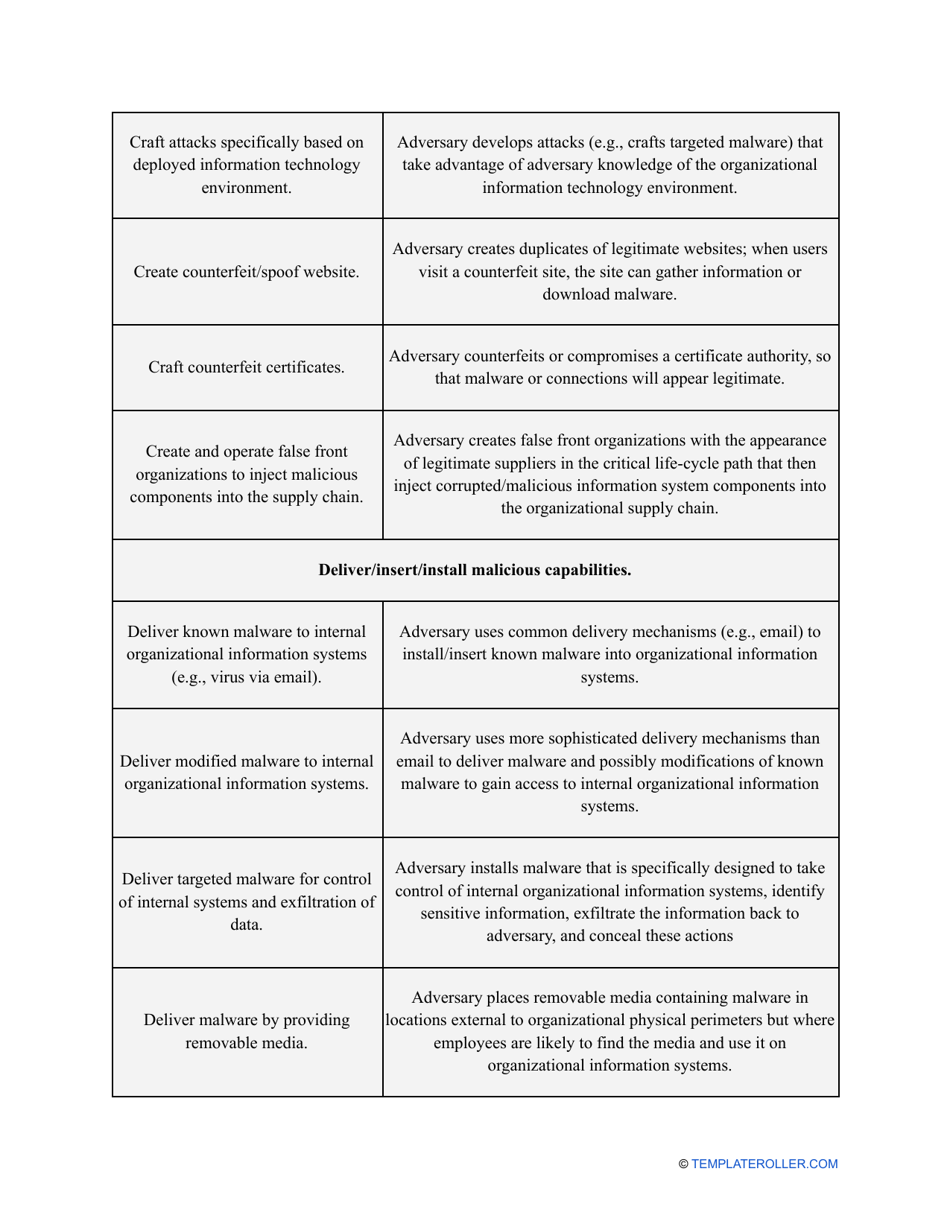
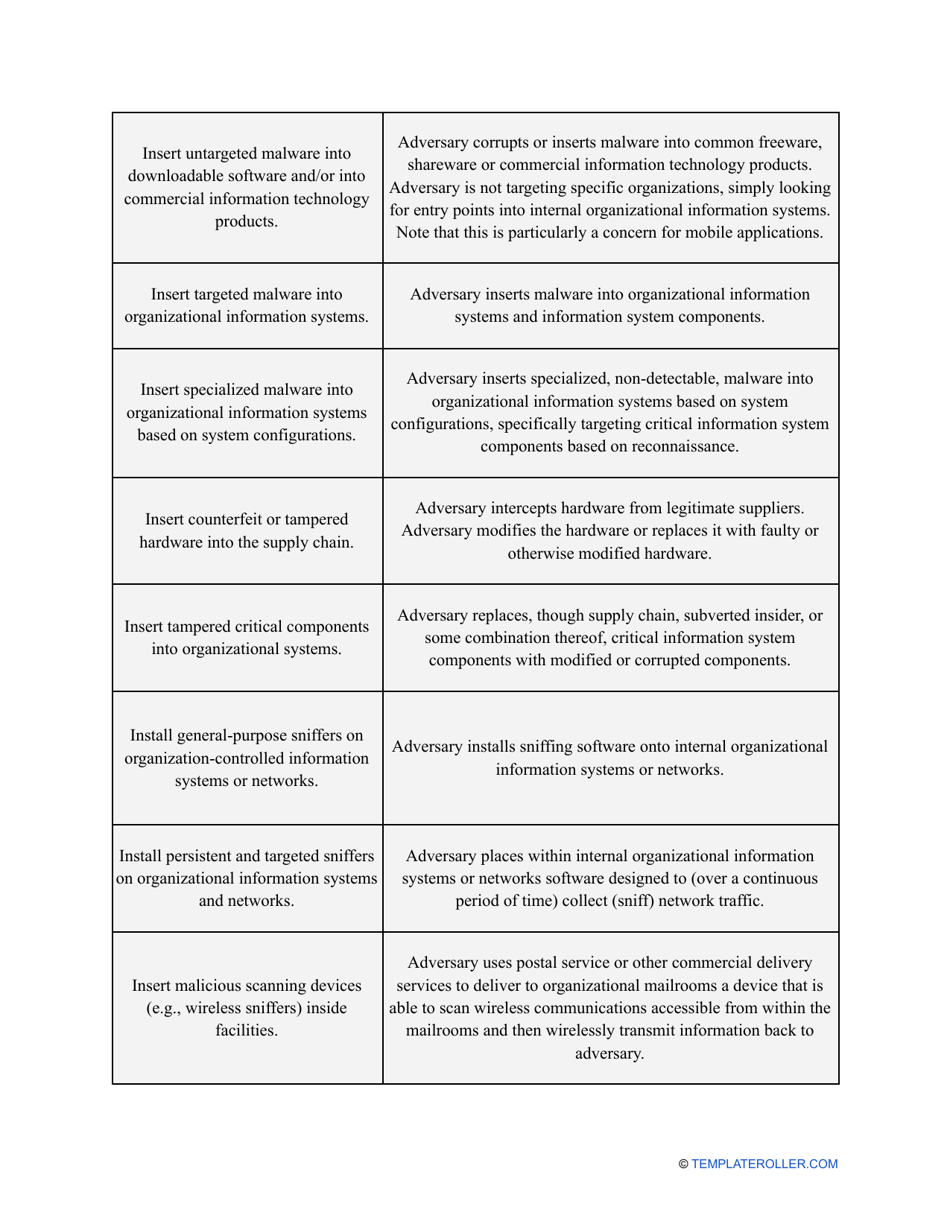
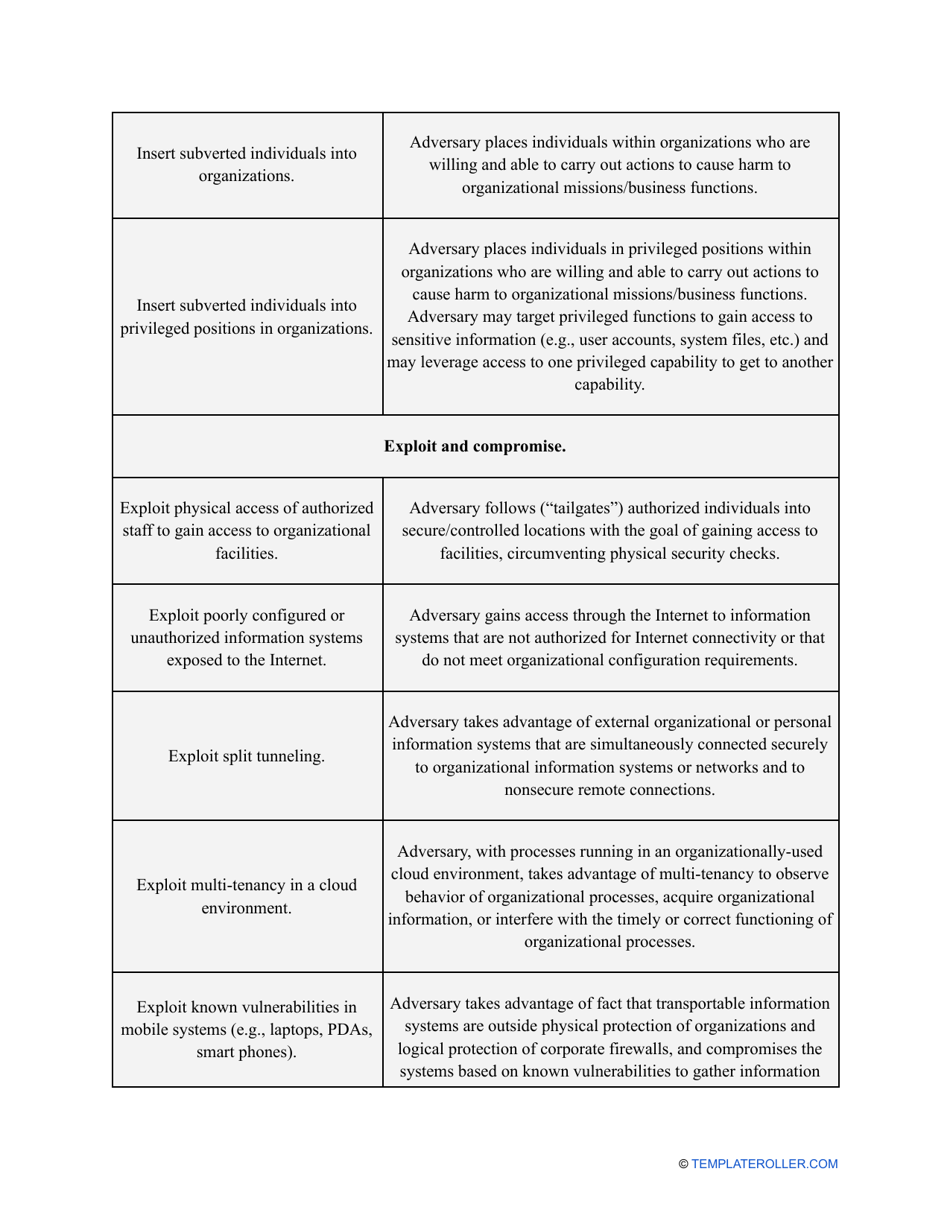
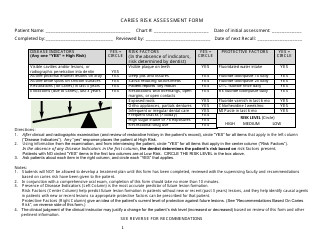
Go through the NIST Risk Assessment Checklist to identify hazards and assess risks in accordance with the NIST standards and practices:
- Indicate the date the assessment takes place . State the name of the employee in charge of the risk assessment.
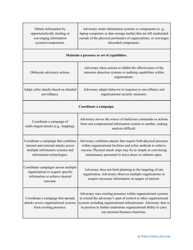
- Write down the purpose of the procedure - your goal is to understand how big is the security risk to your company and learn what information technology will minimize the risk to your business, its mission, and day-to-day activities.
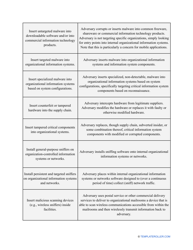
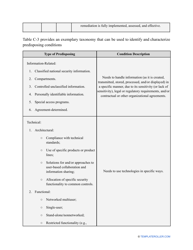
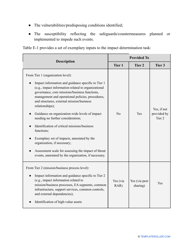
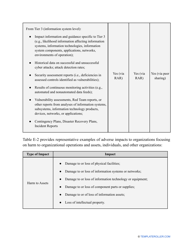
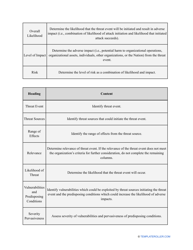
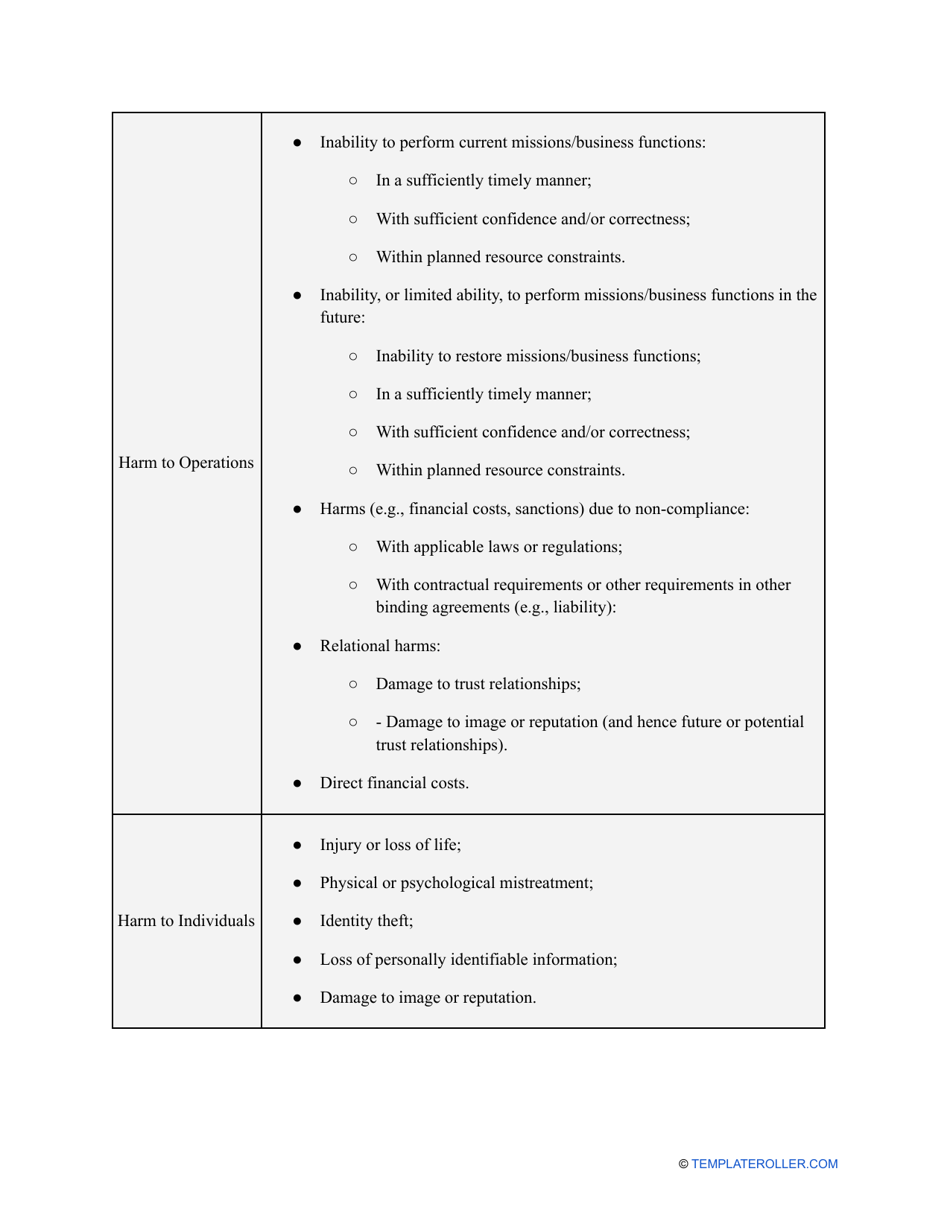
- Describe the scope of the evaluation - for example, you can list all the valuable assets the organization possesses that can be harmed by cyberattacks and lead to monetary loss.
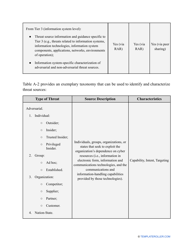
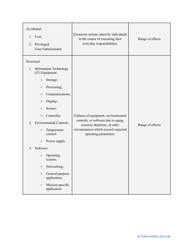
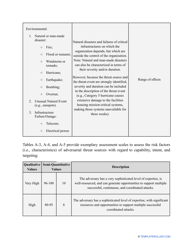
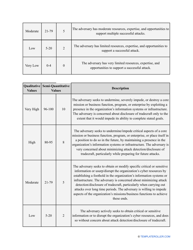
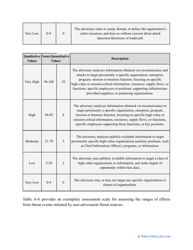
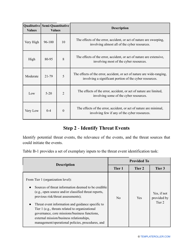
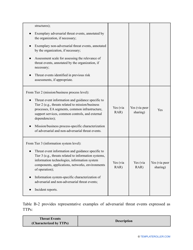
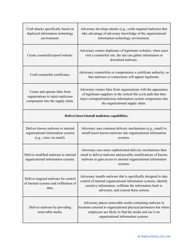
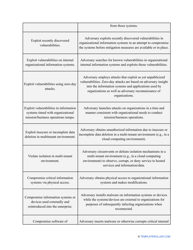
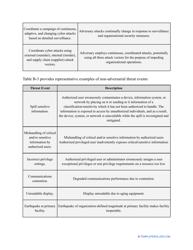
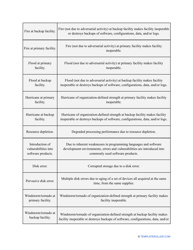
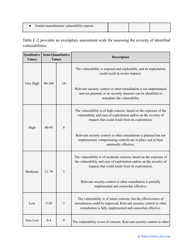
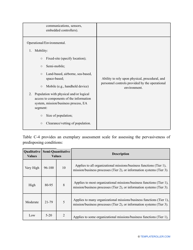
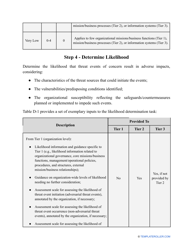
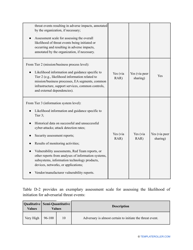
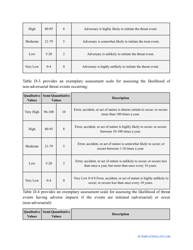
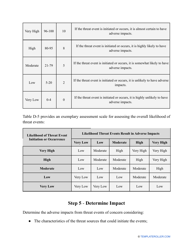
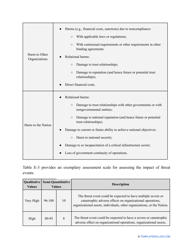
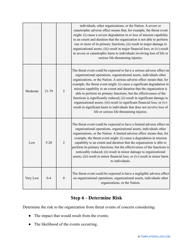
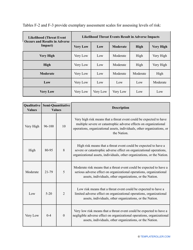
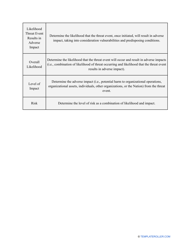
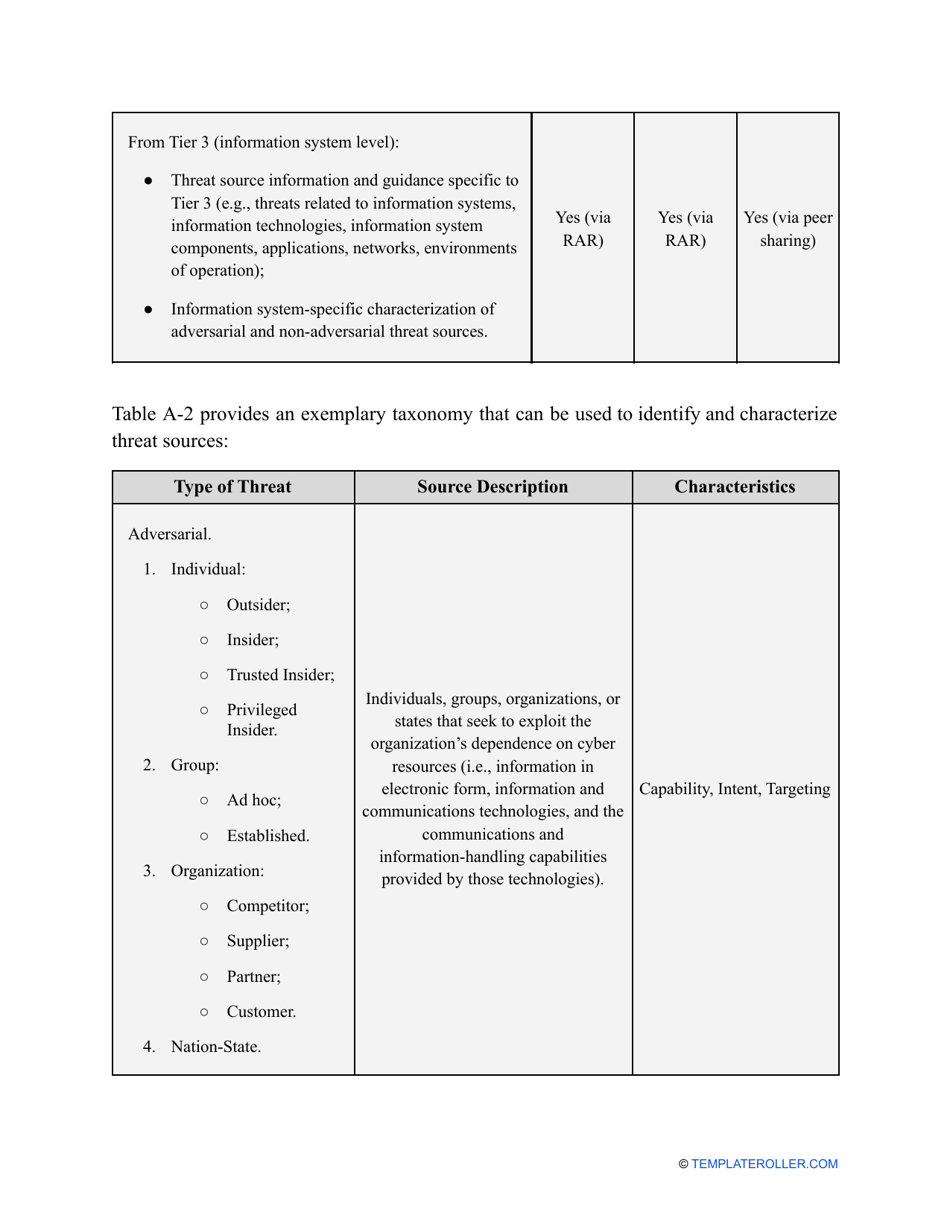
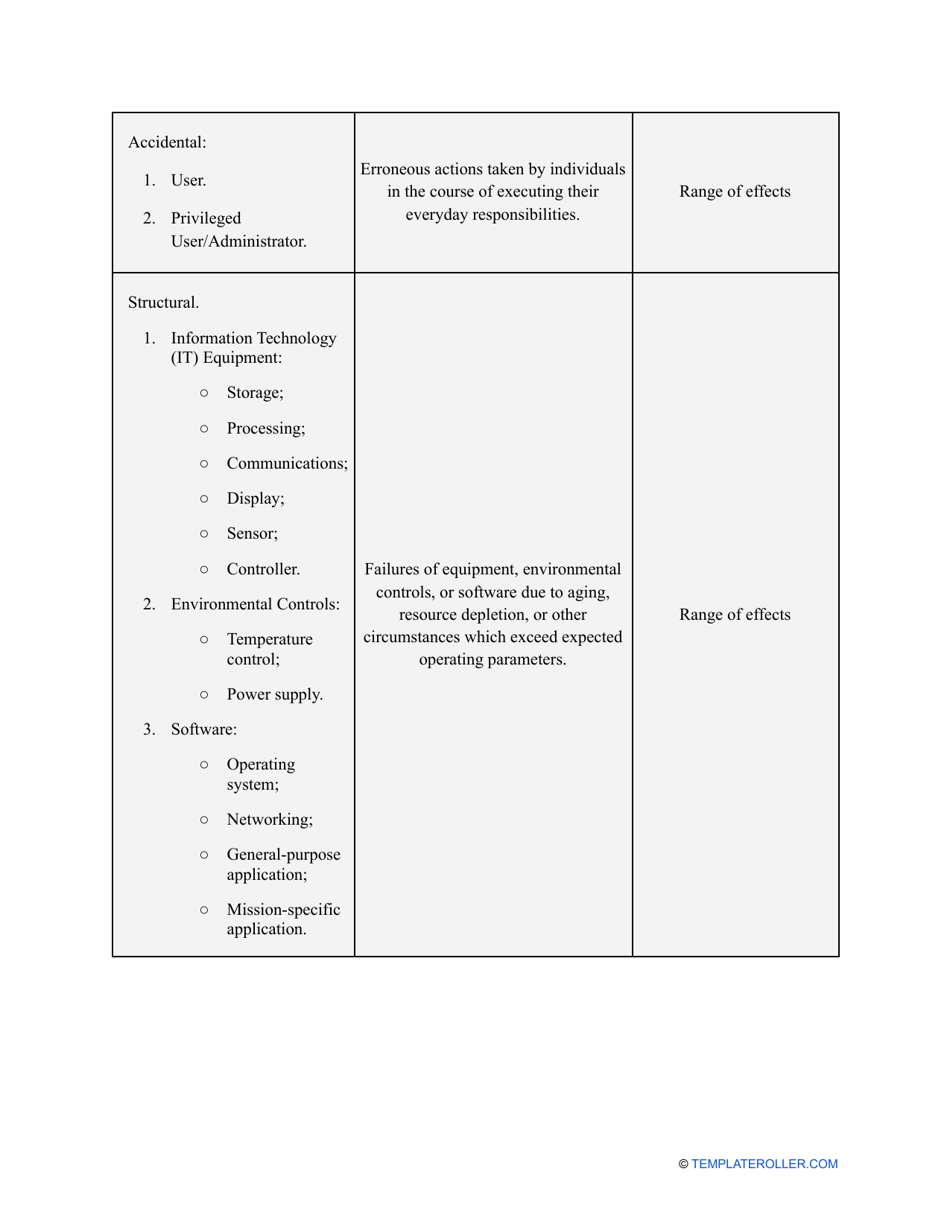
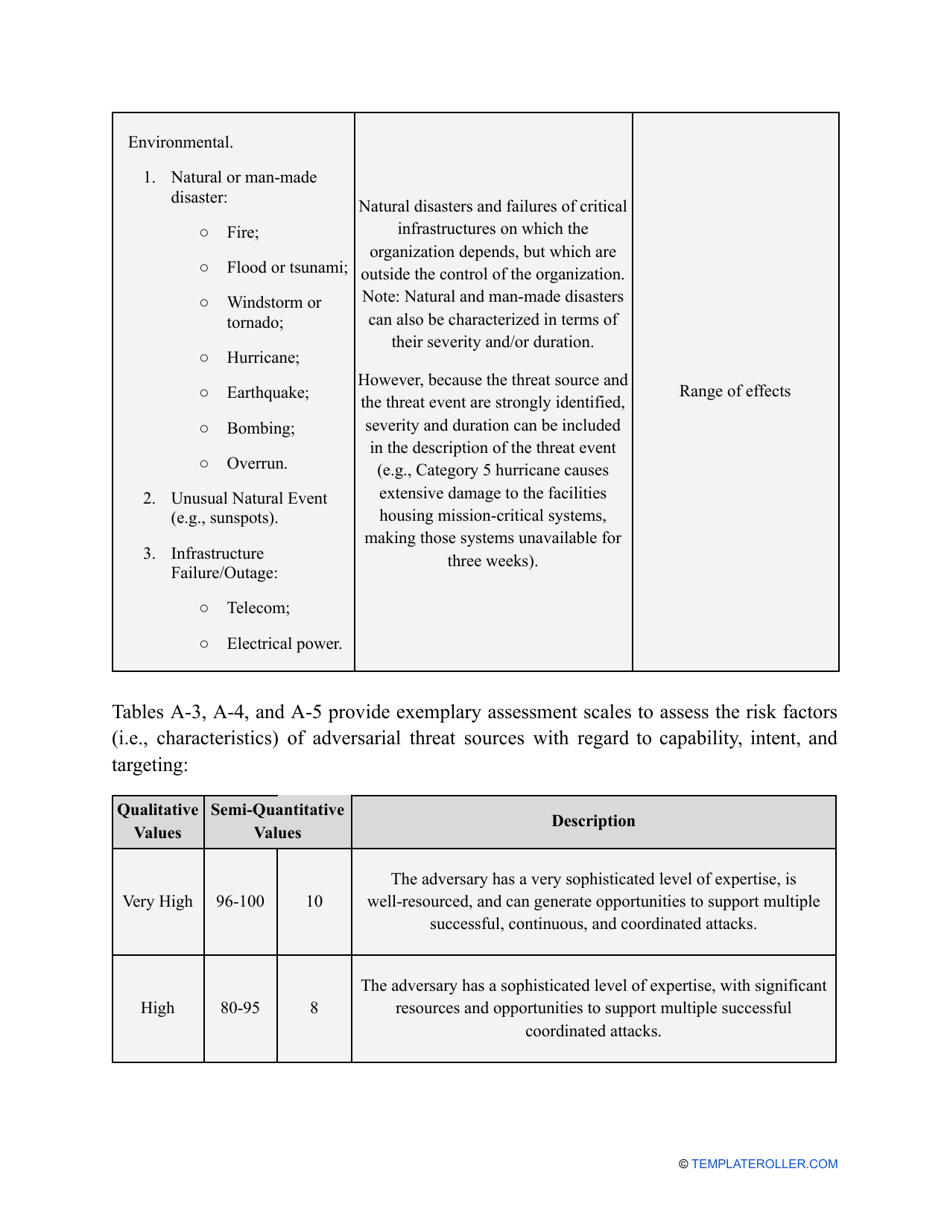
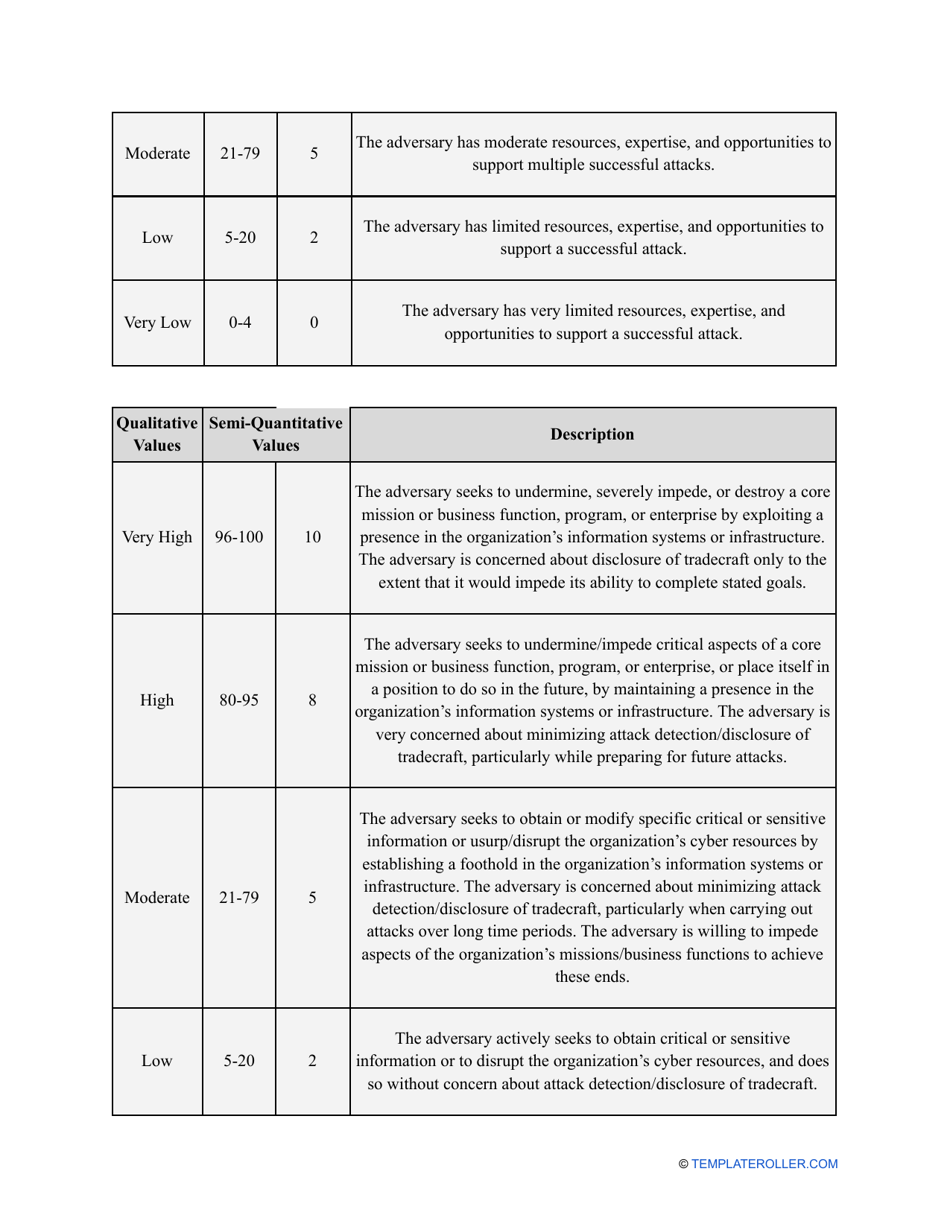
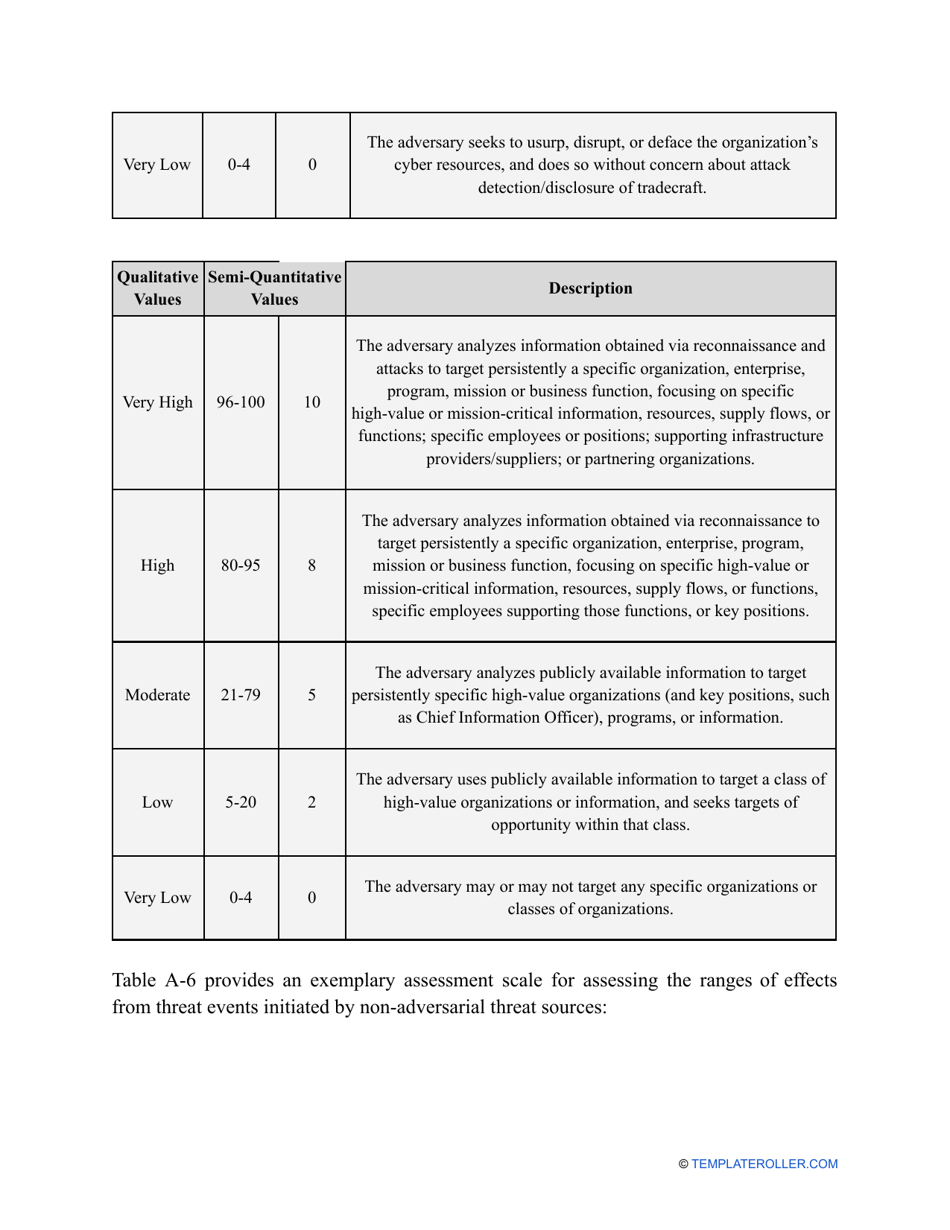
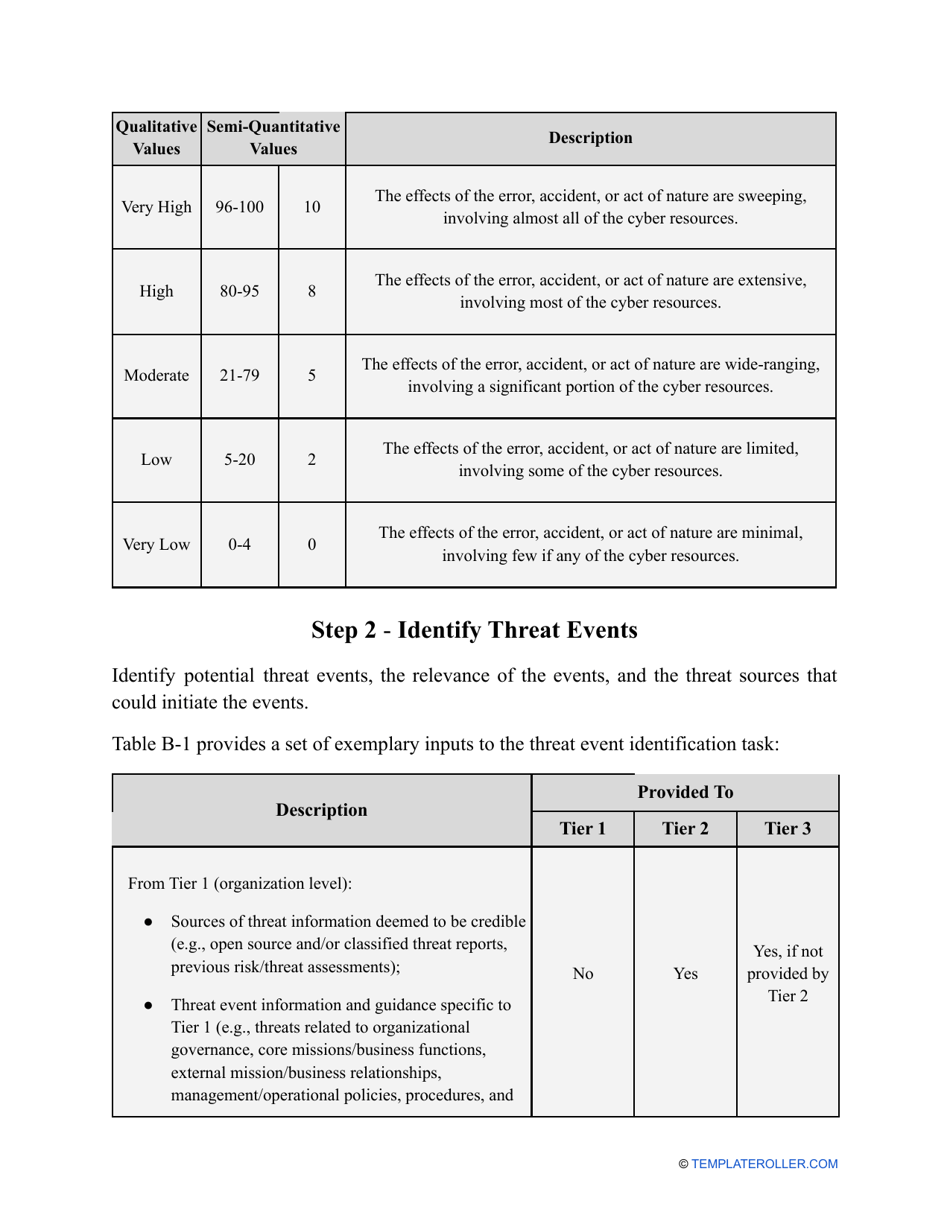
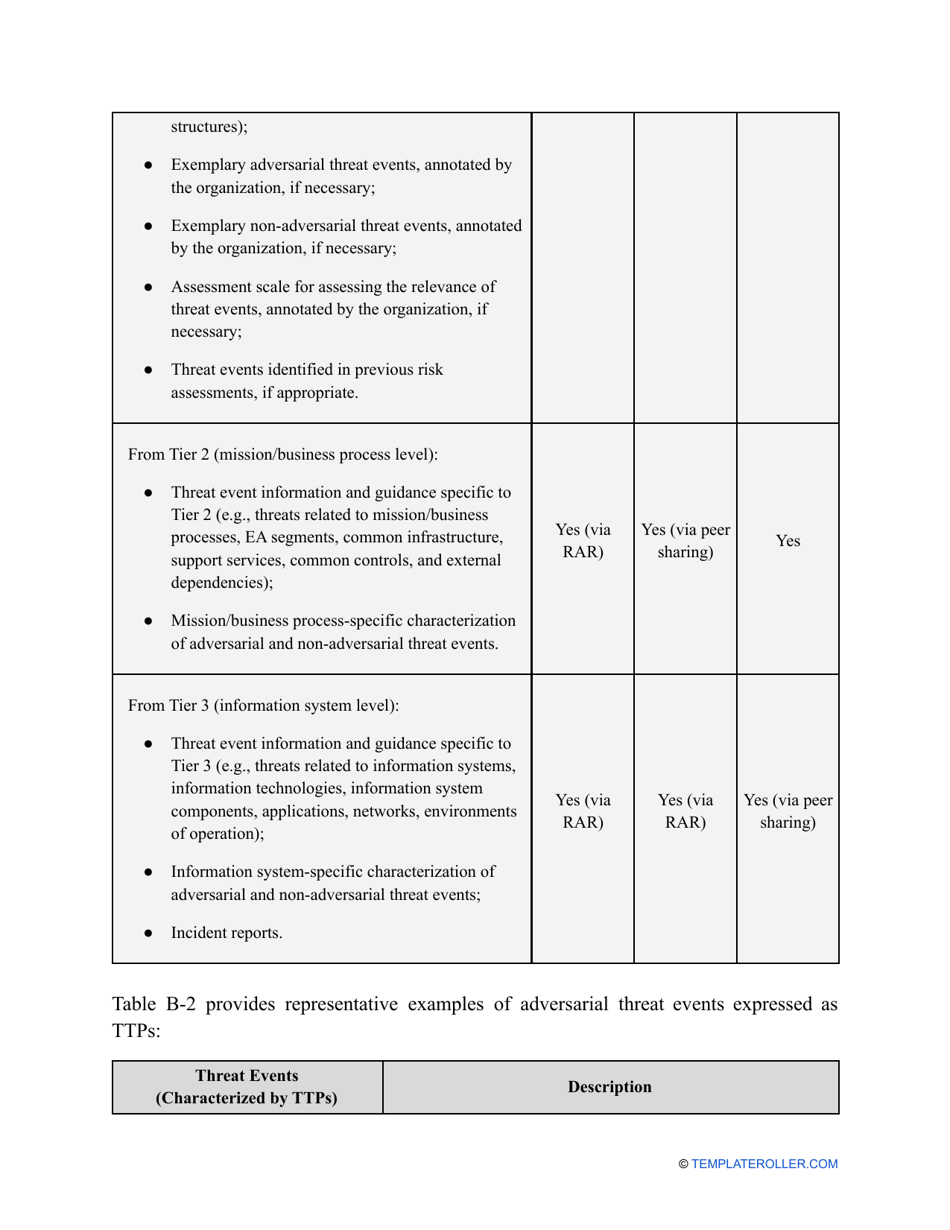
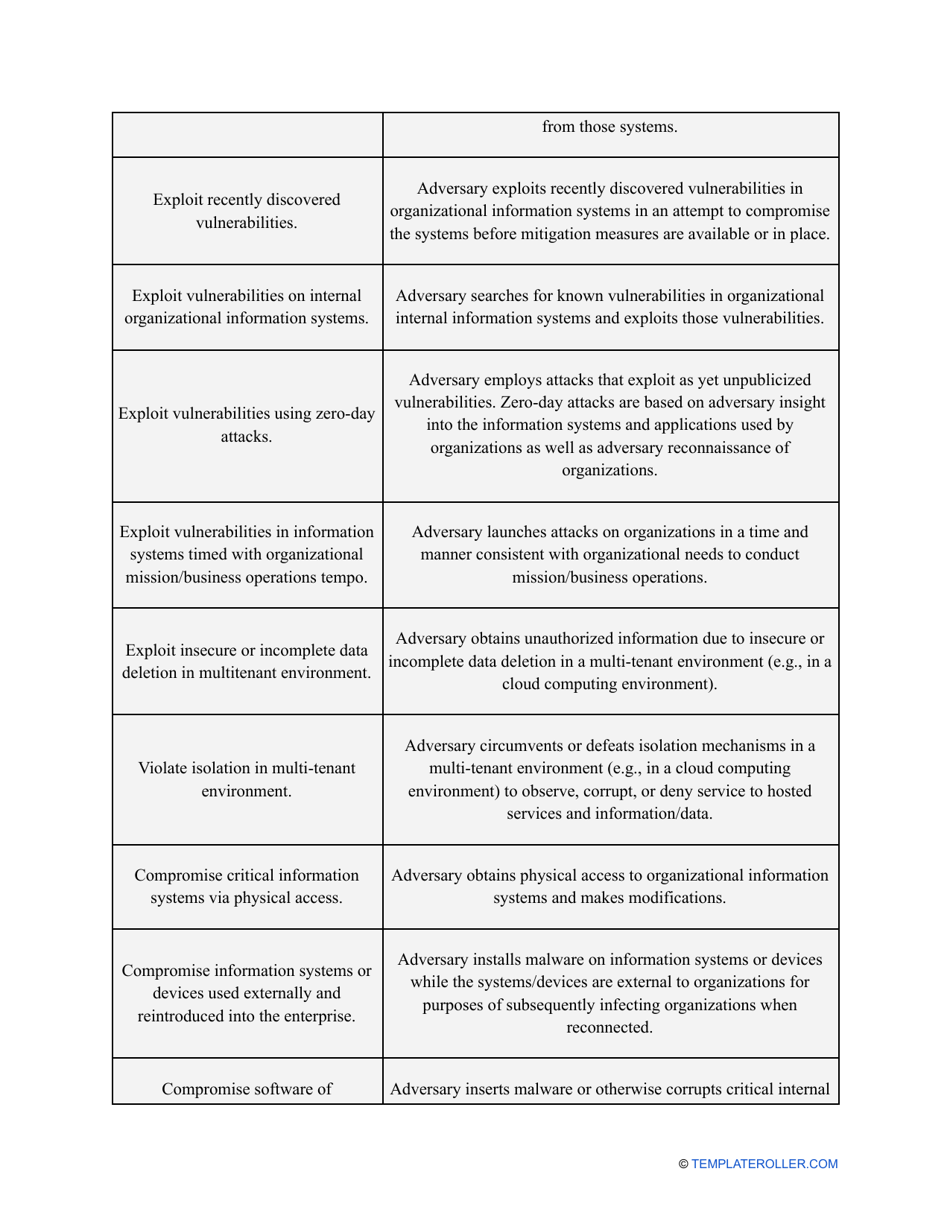
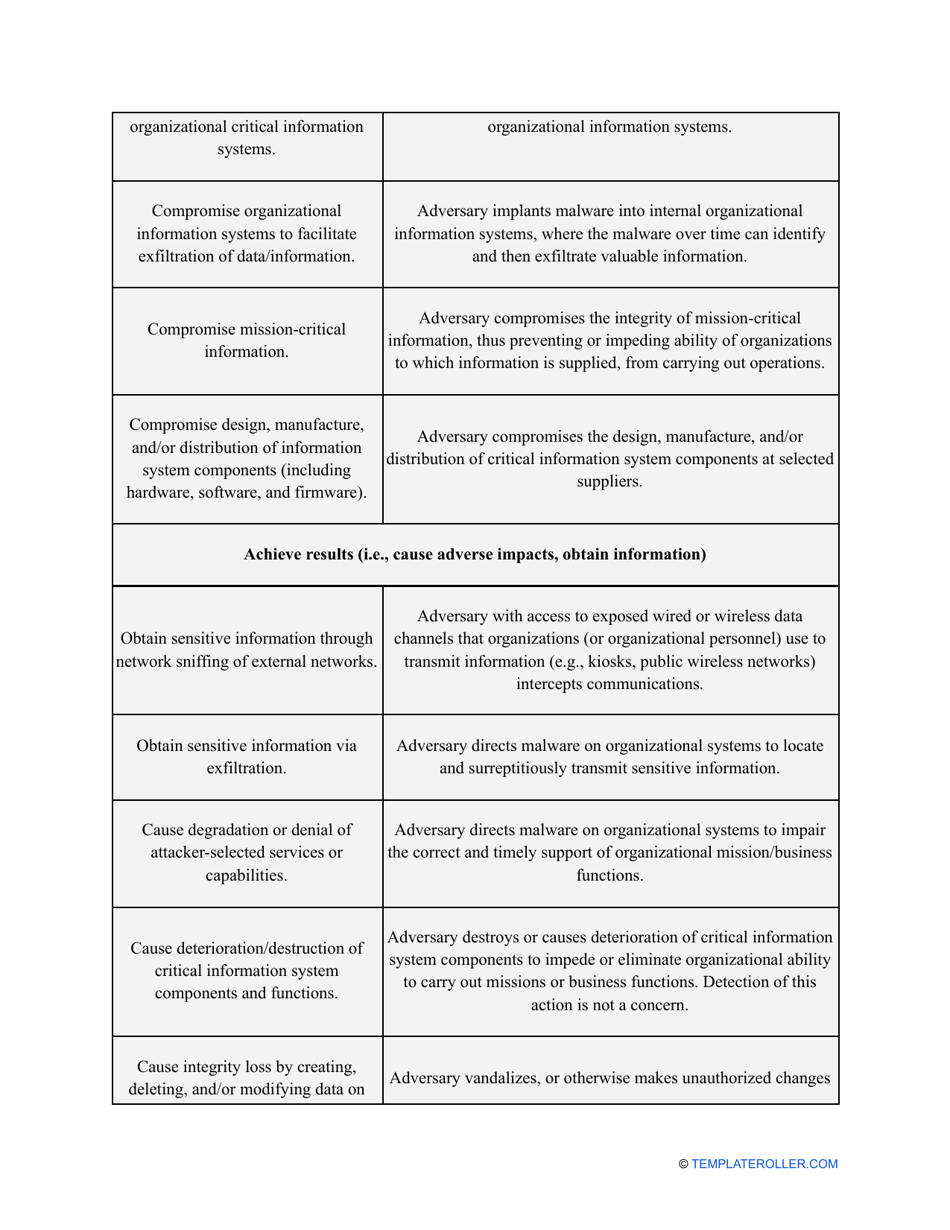
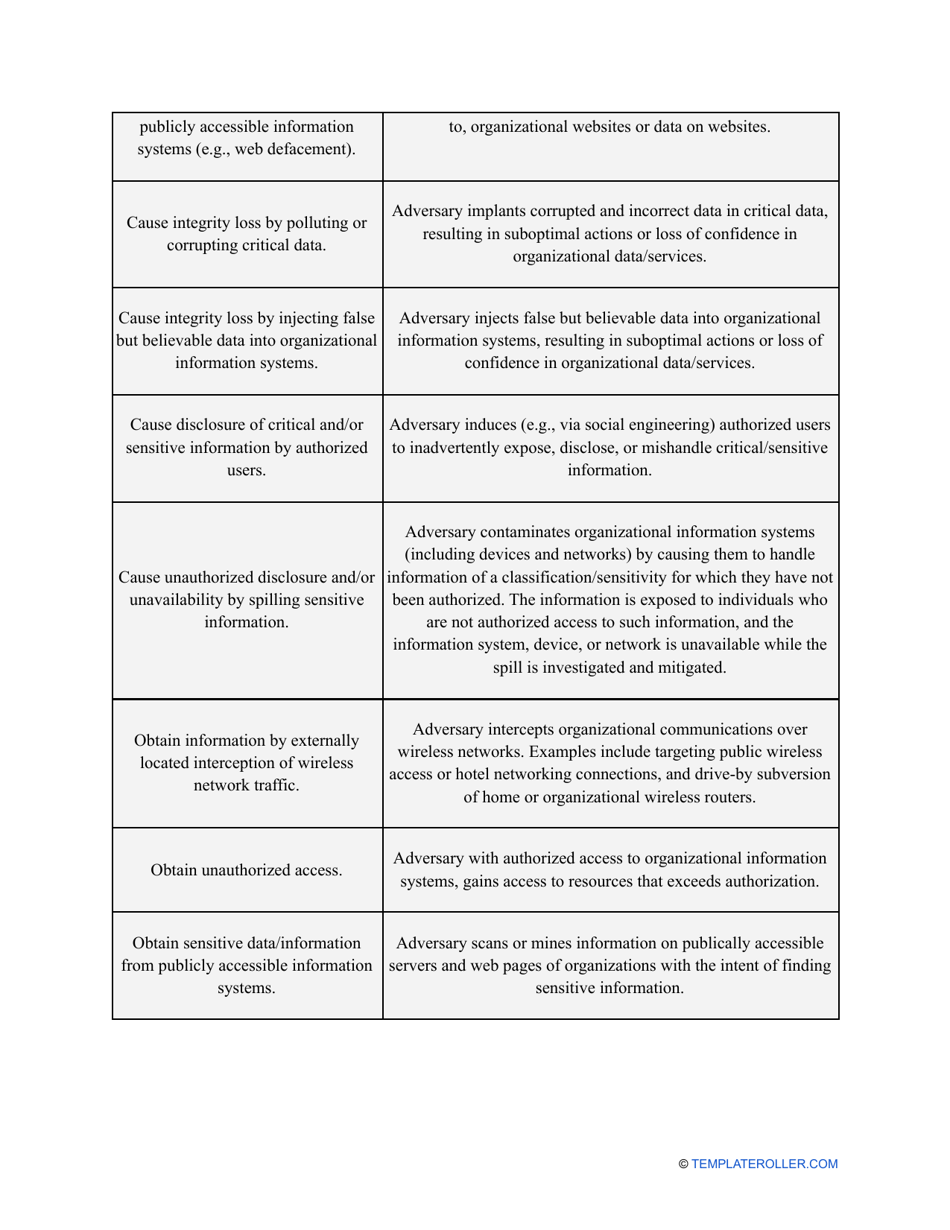
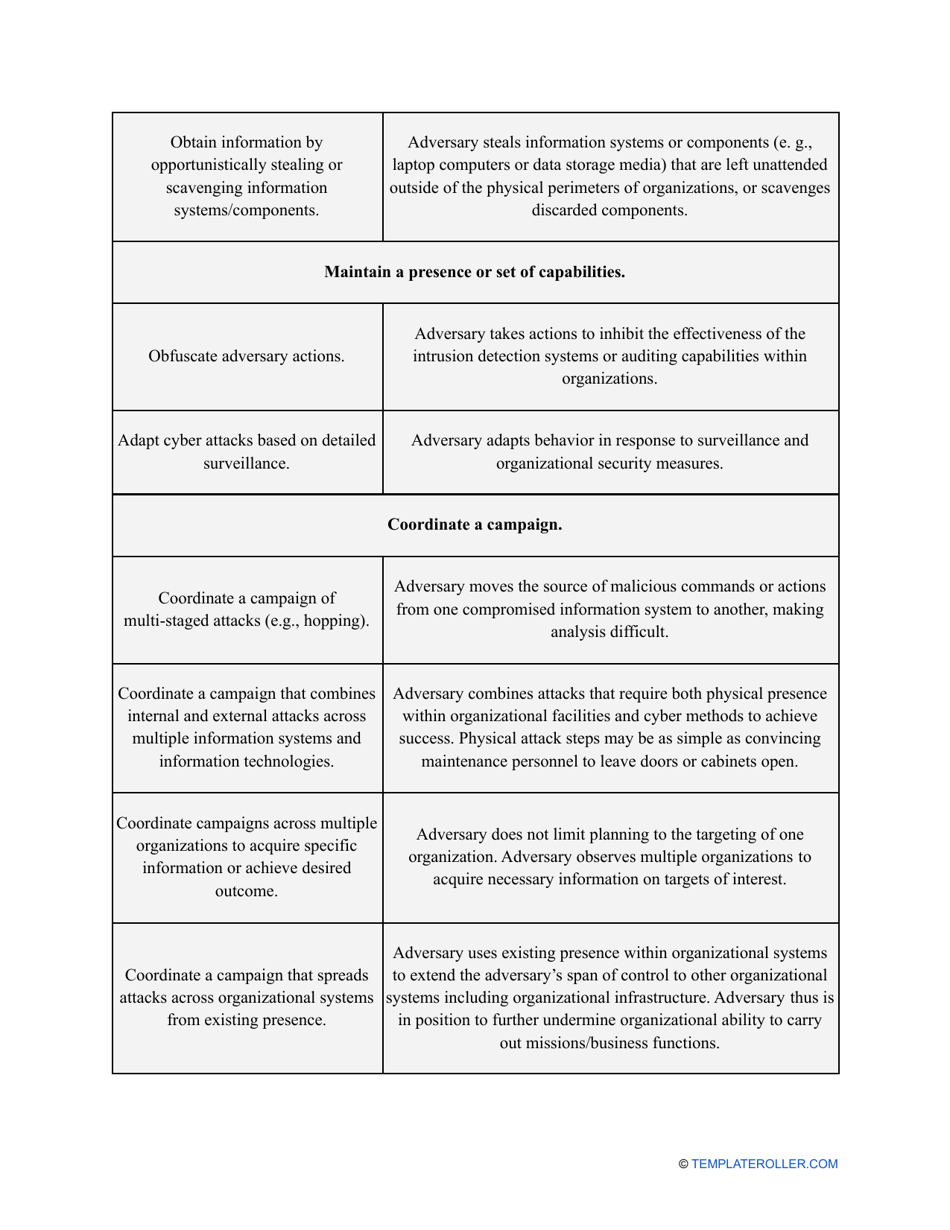
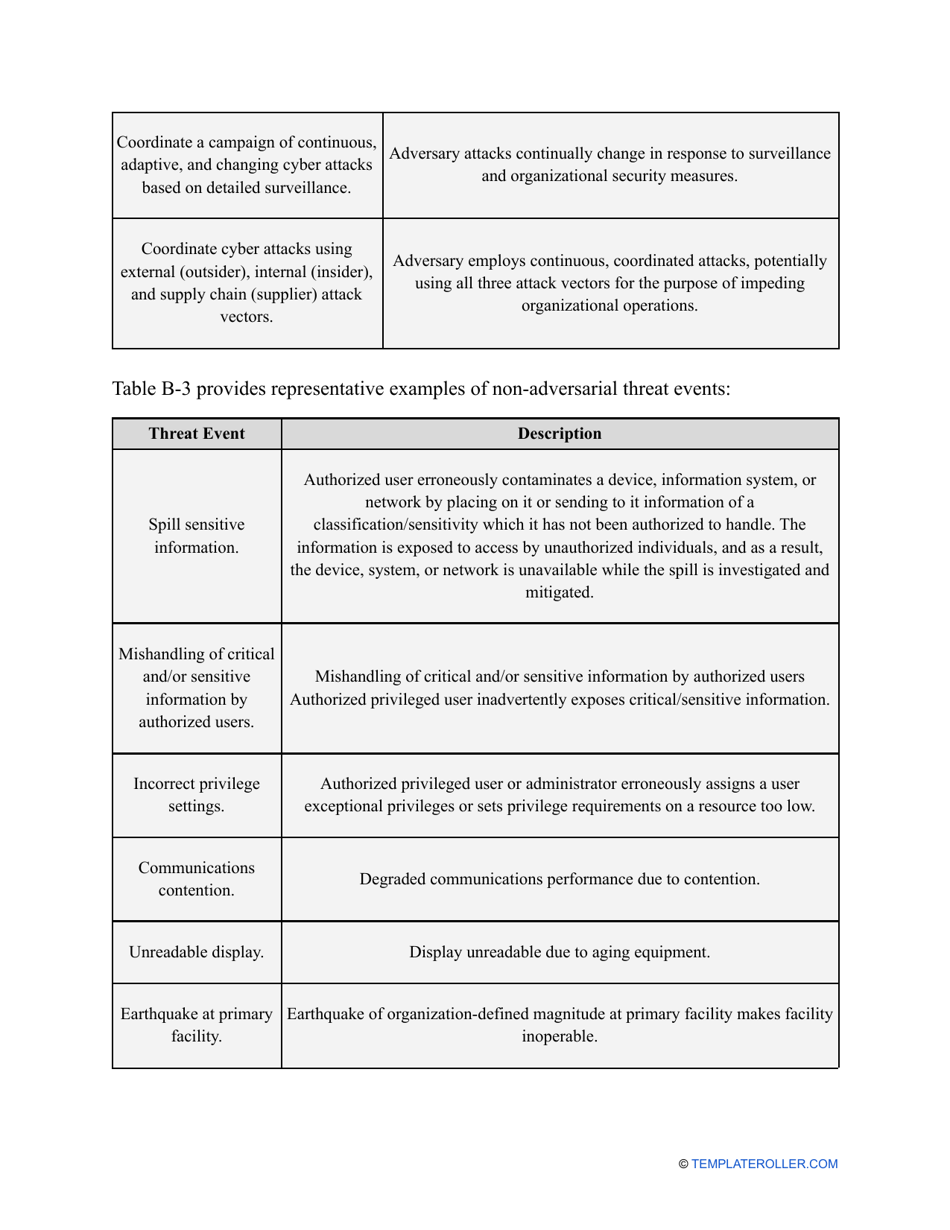
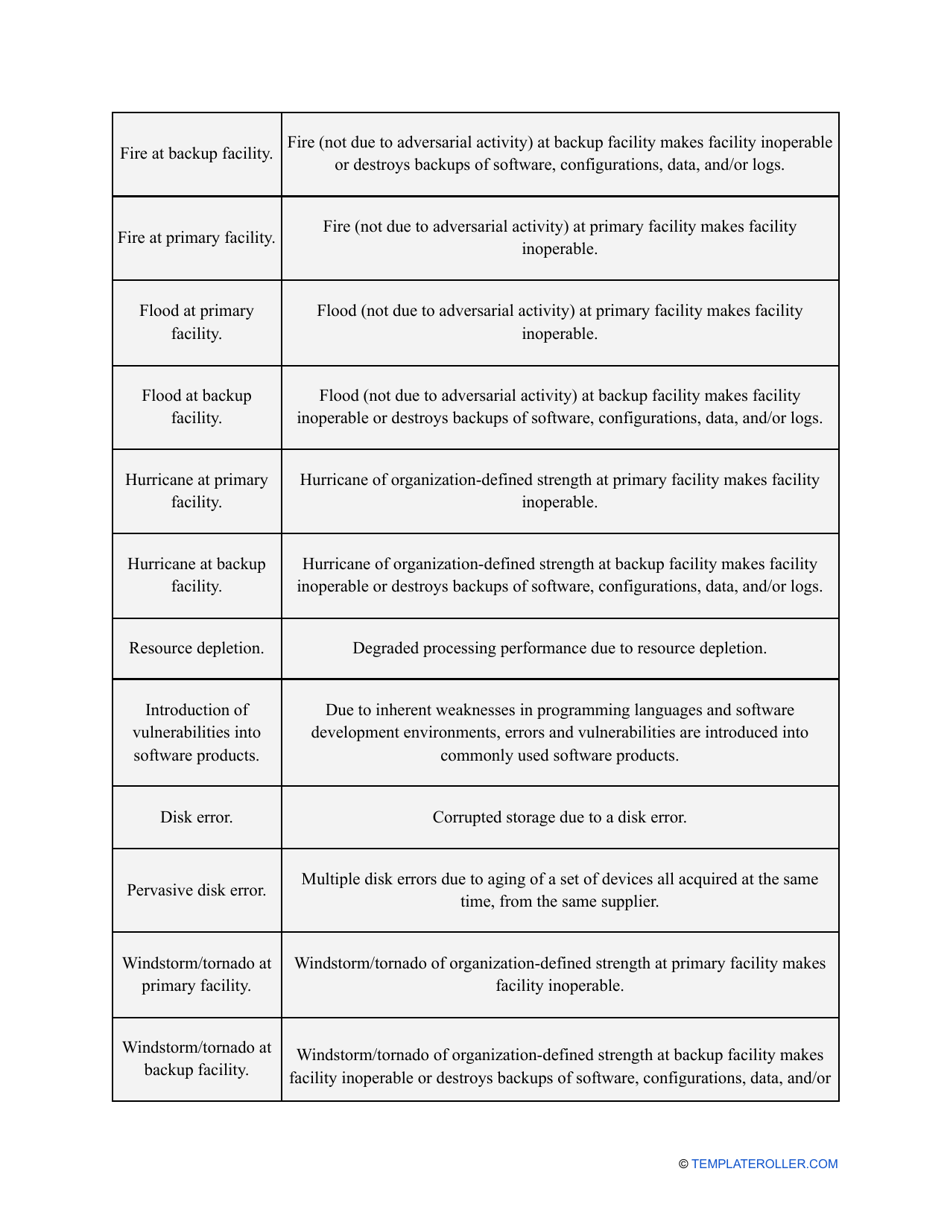
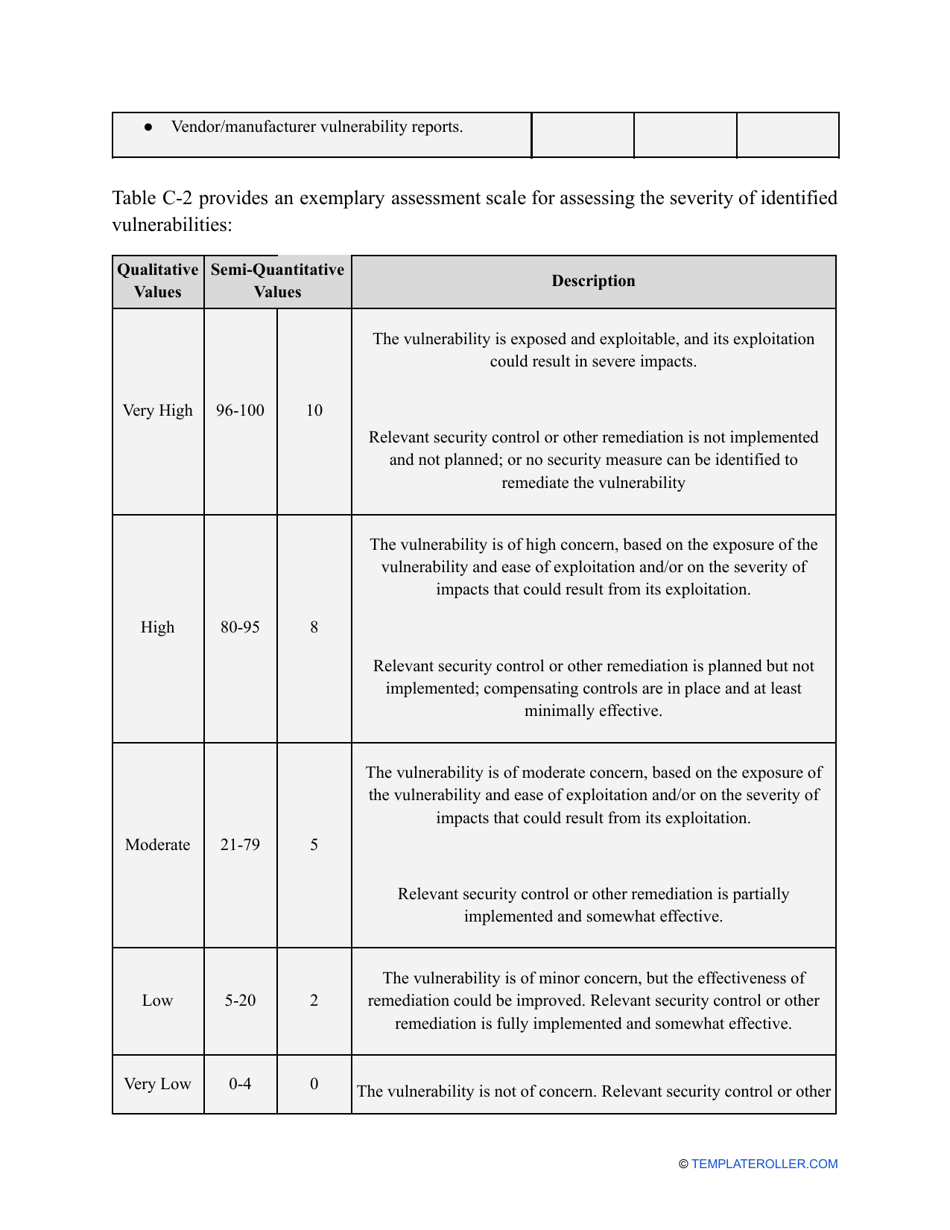
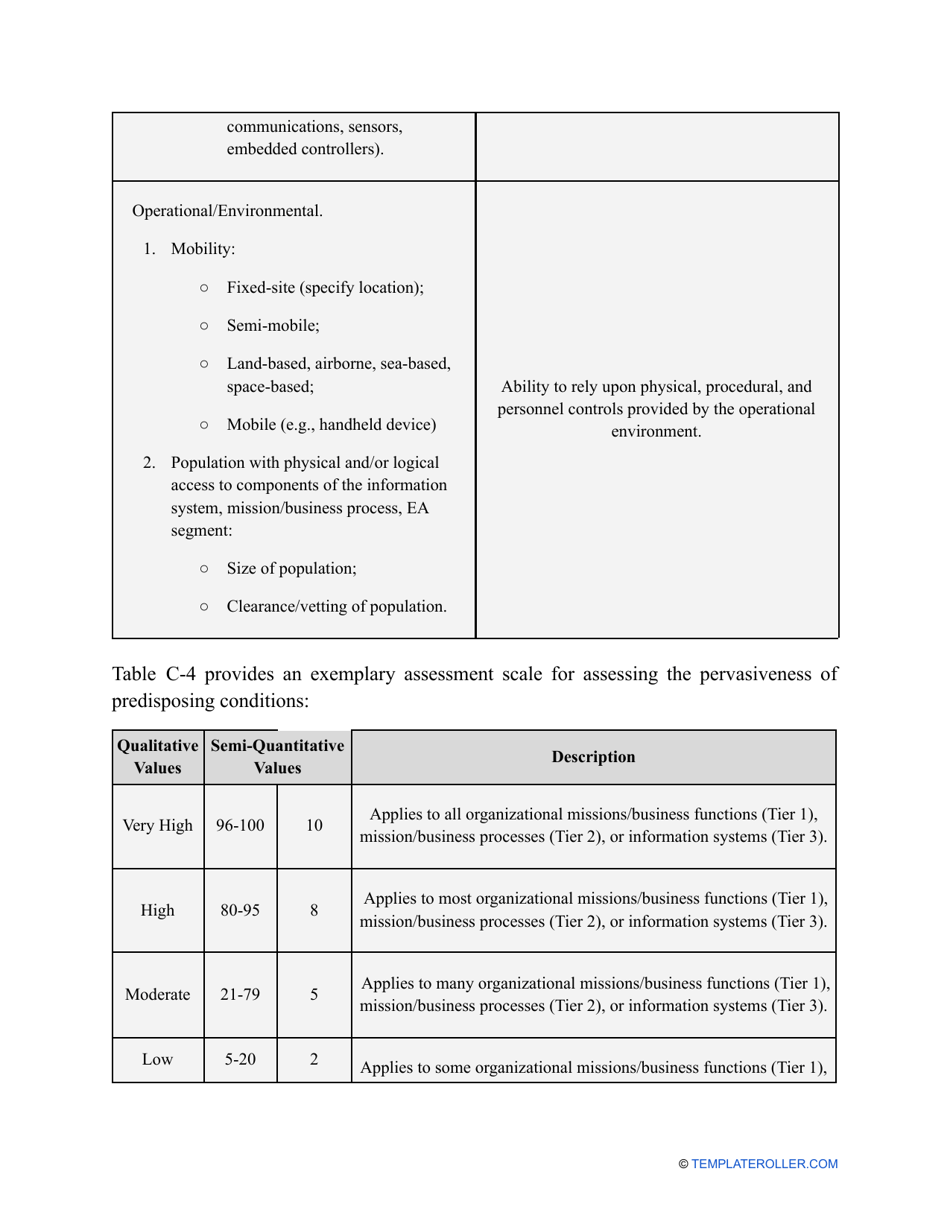
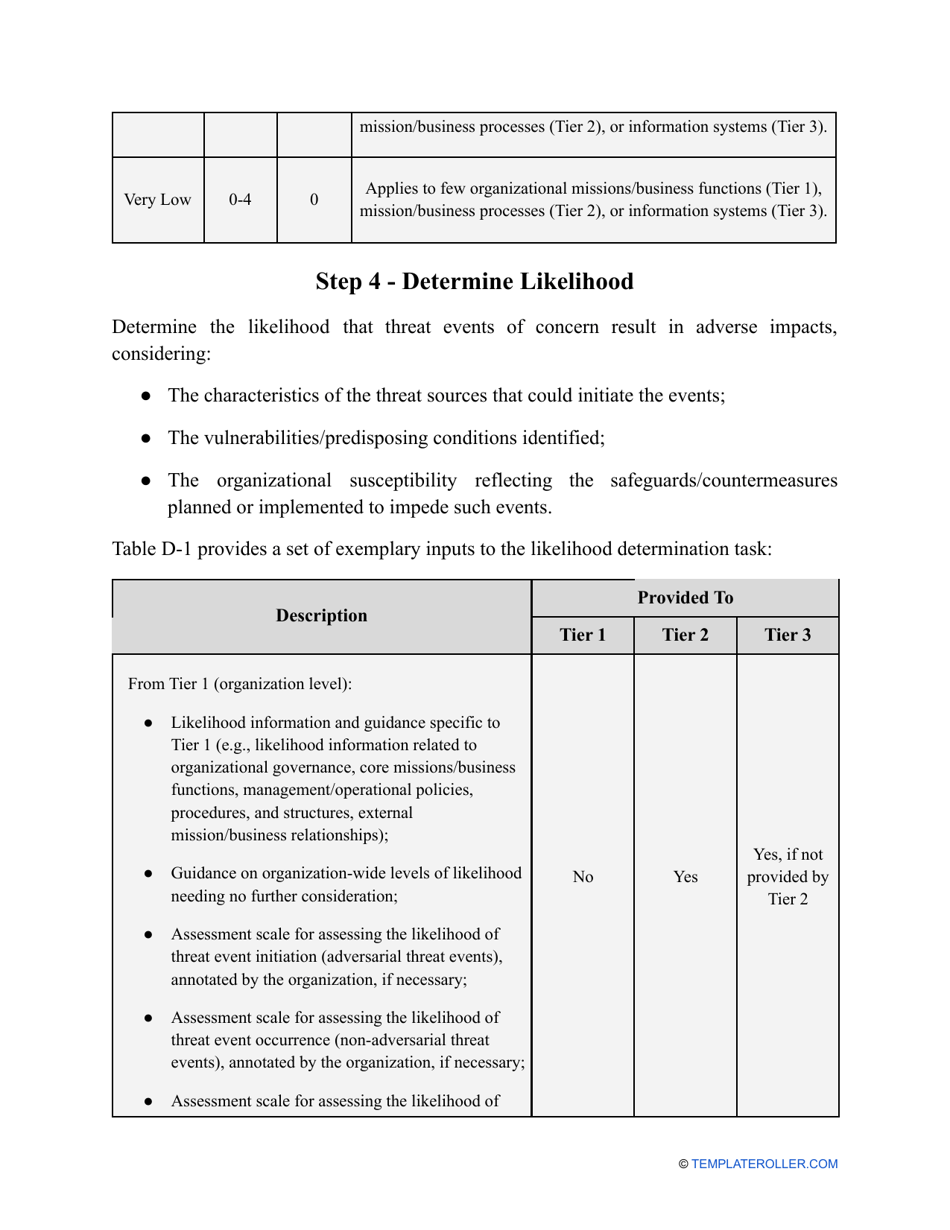
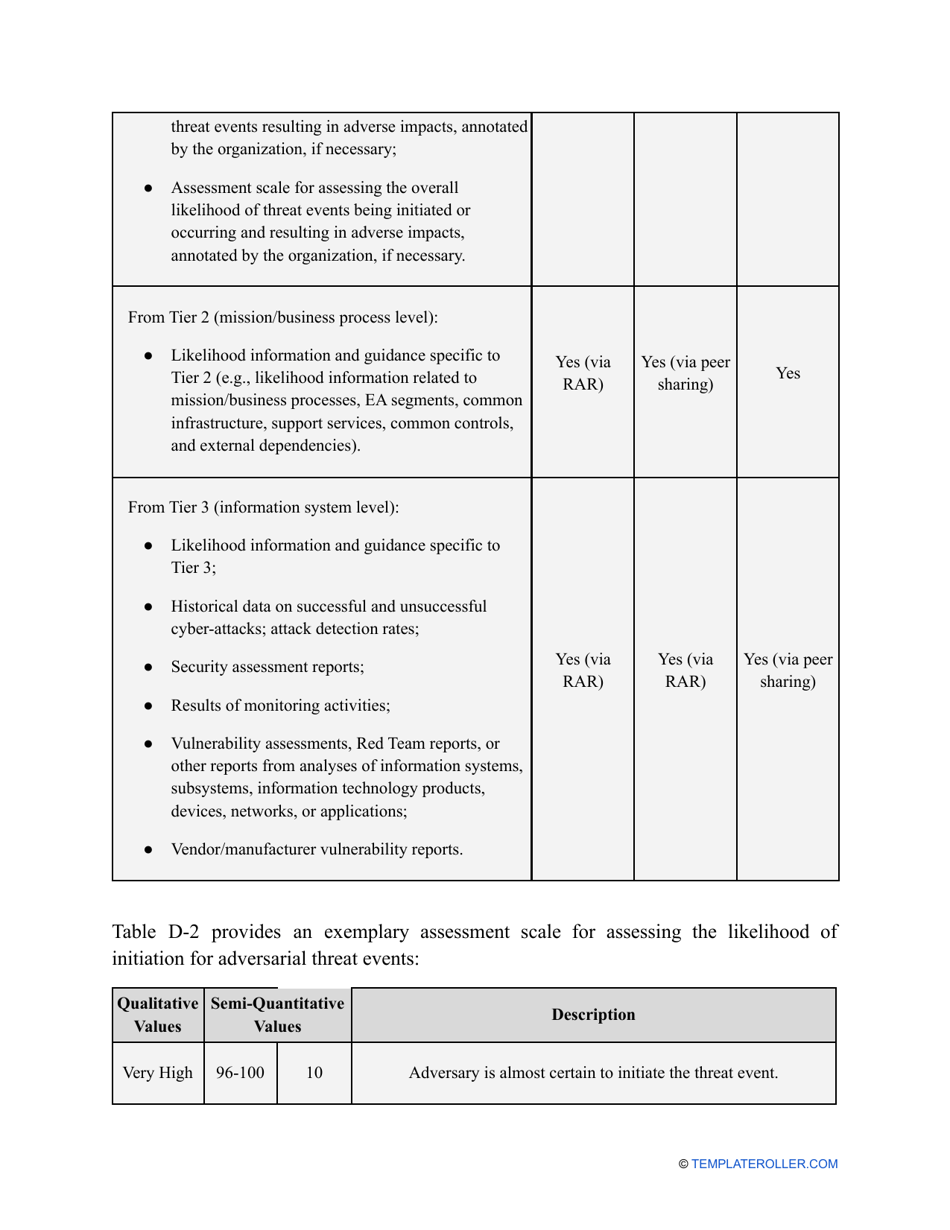
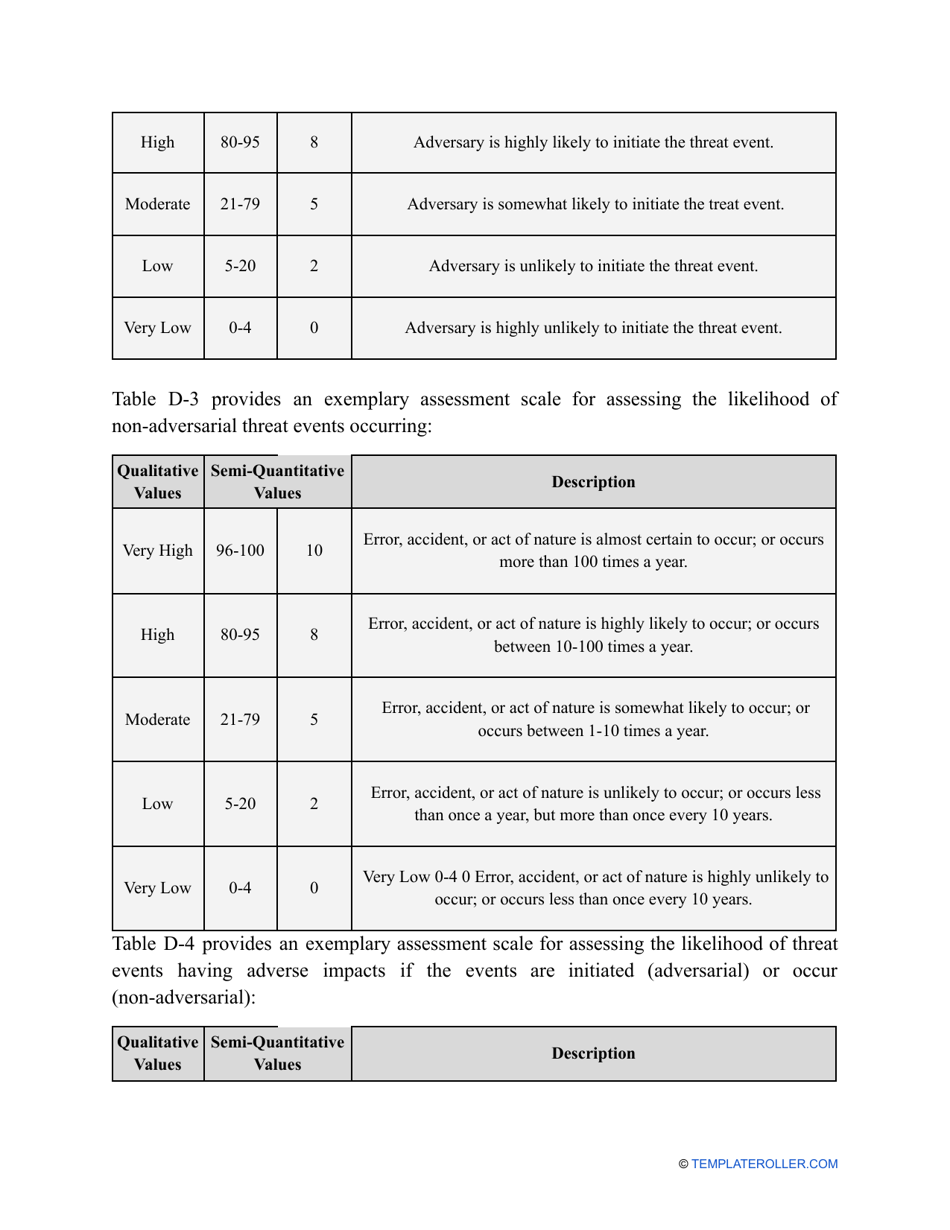
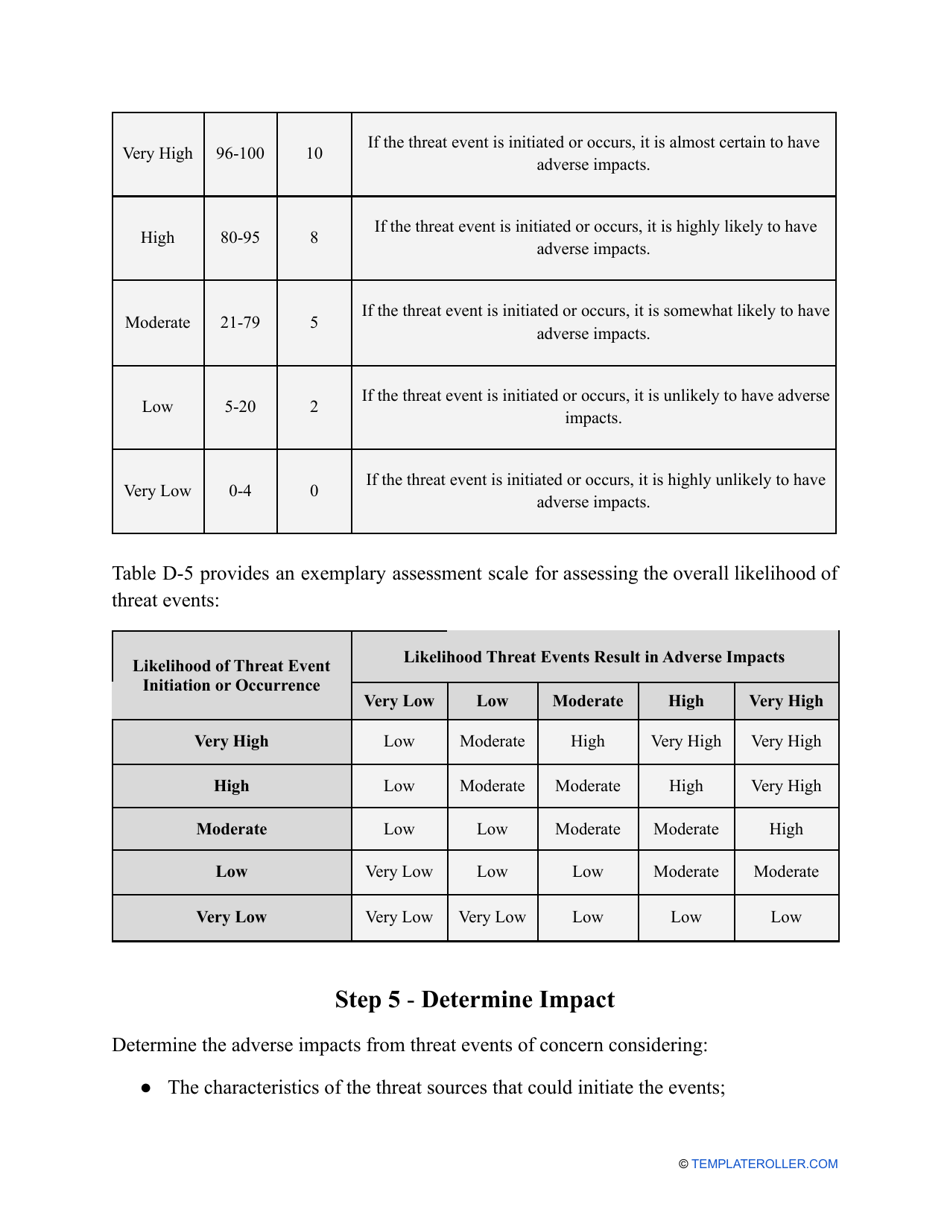
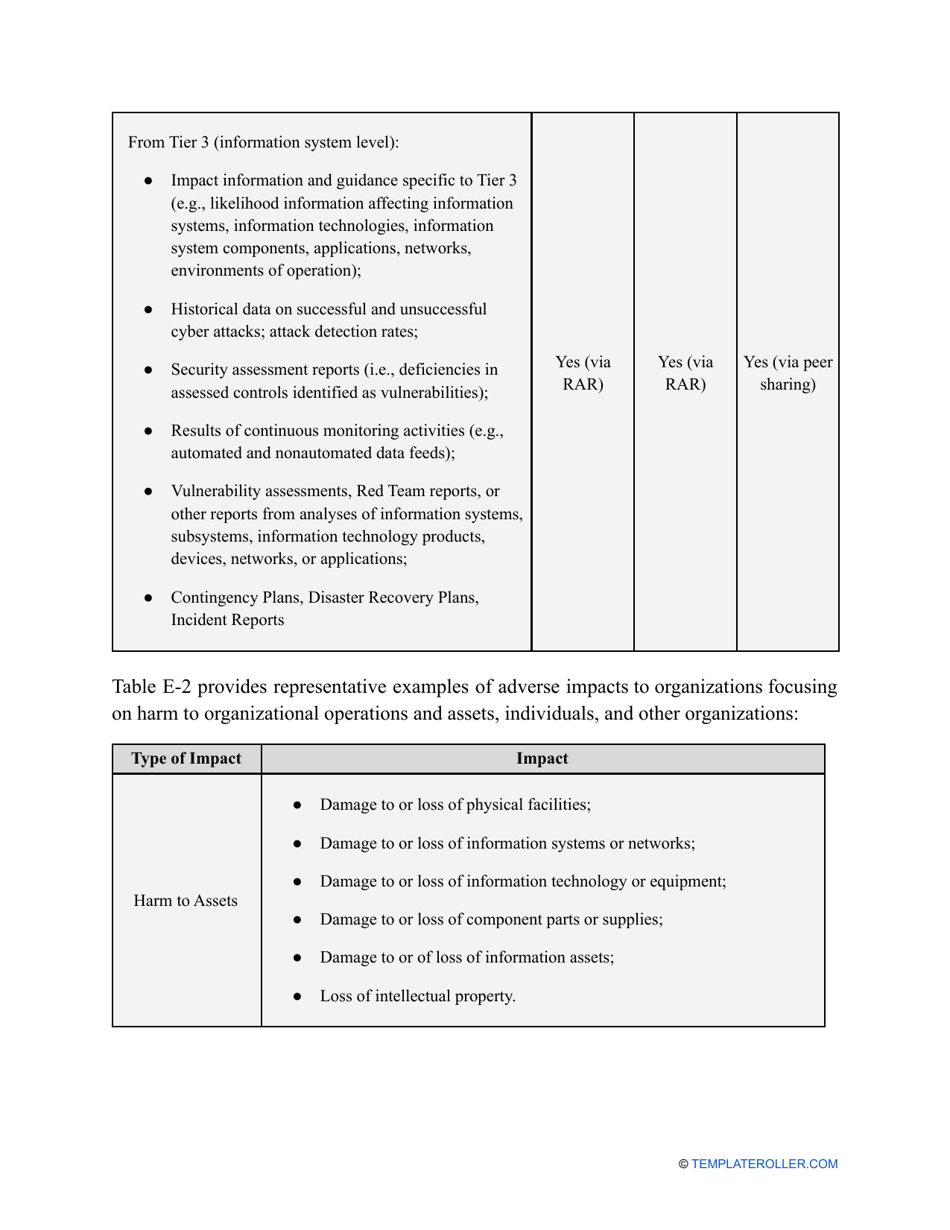
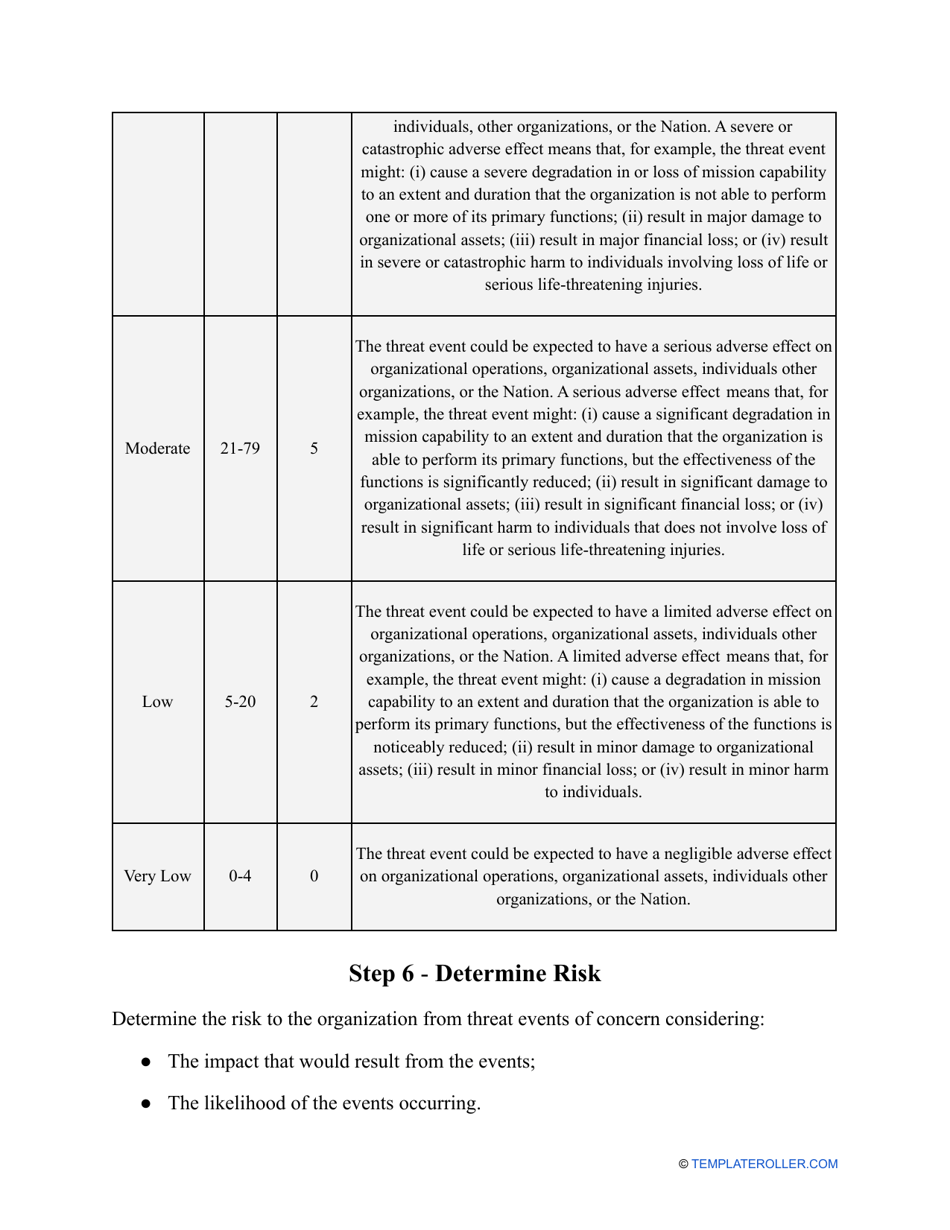
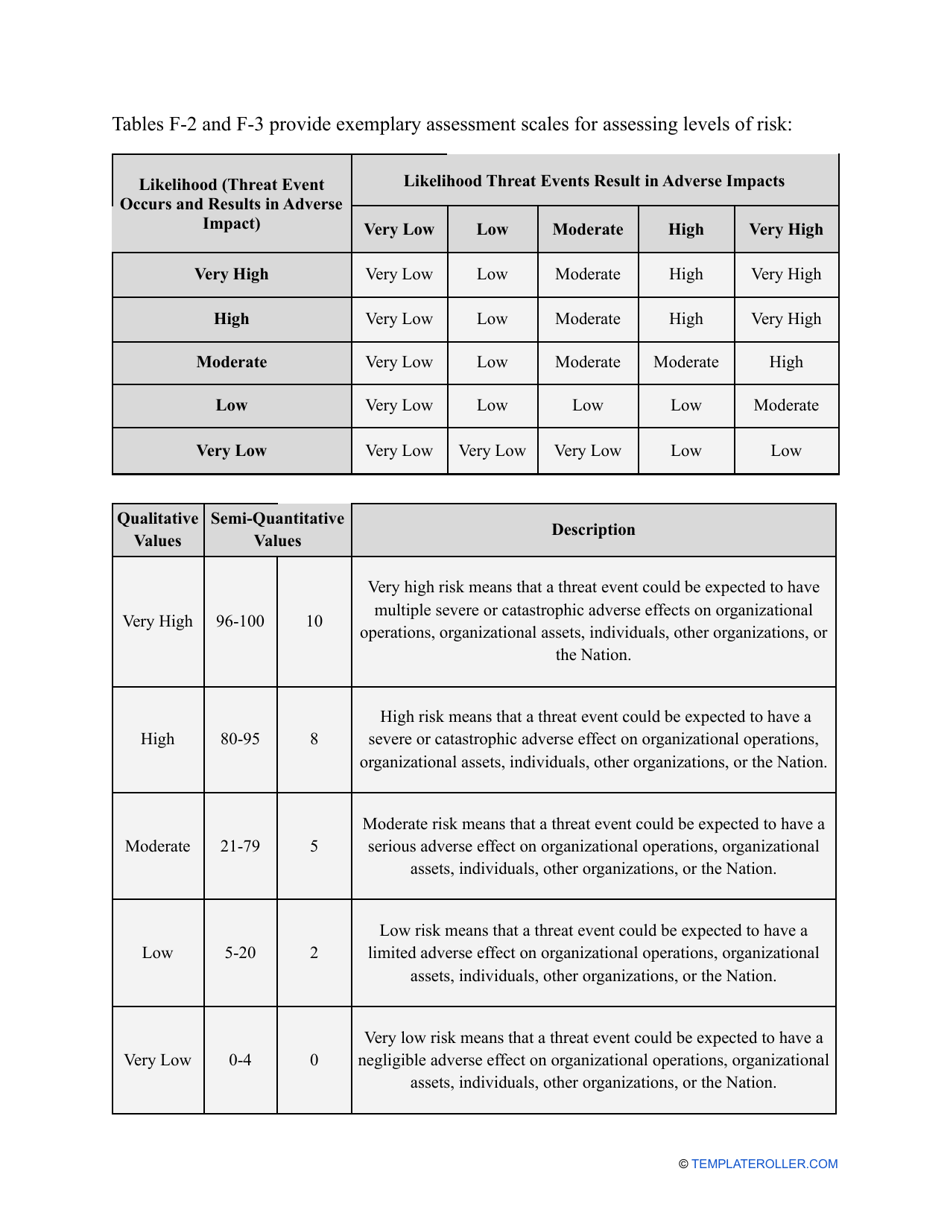
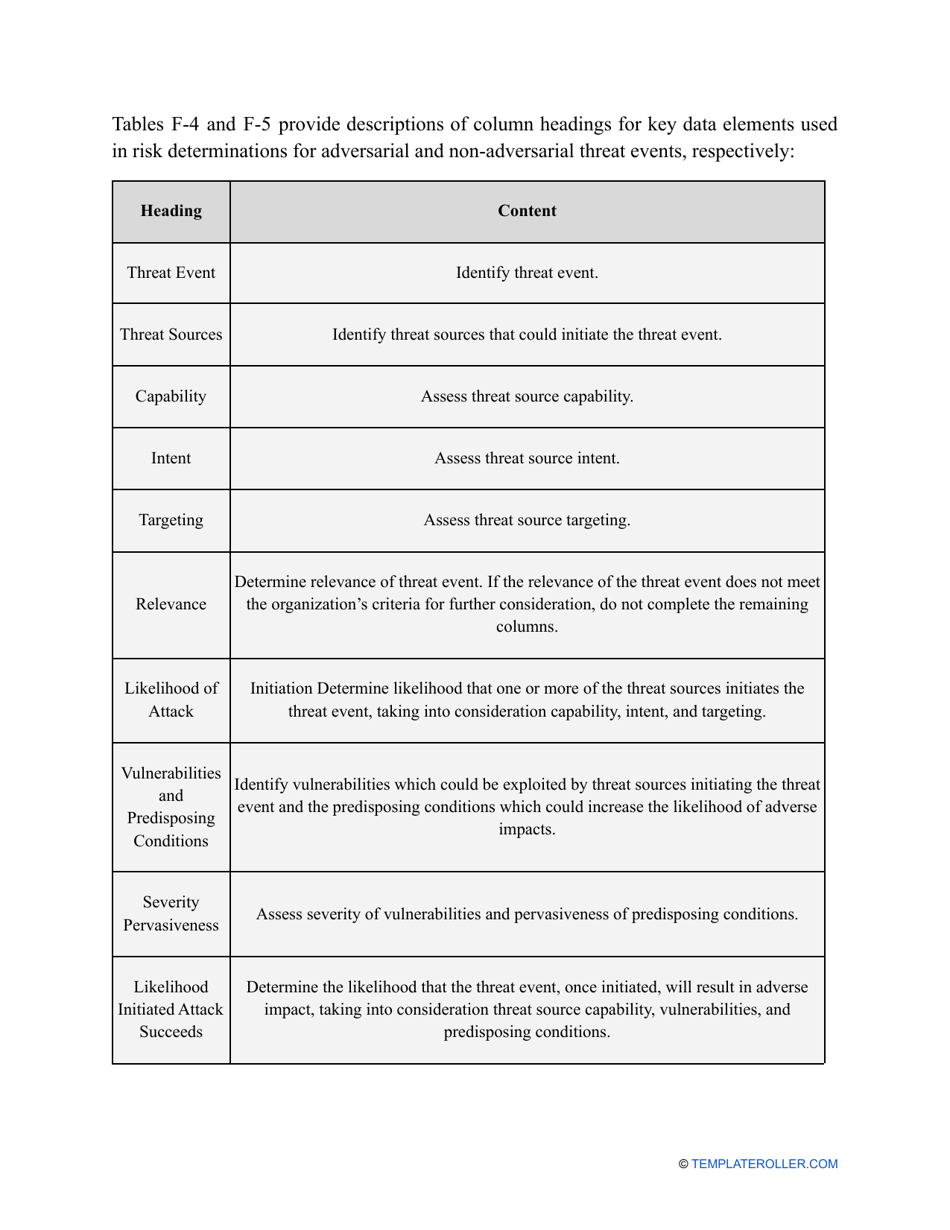
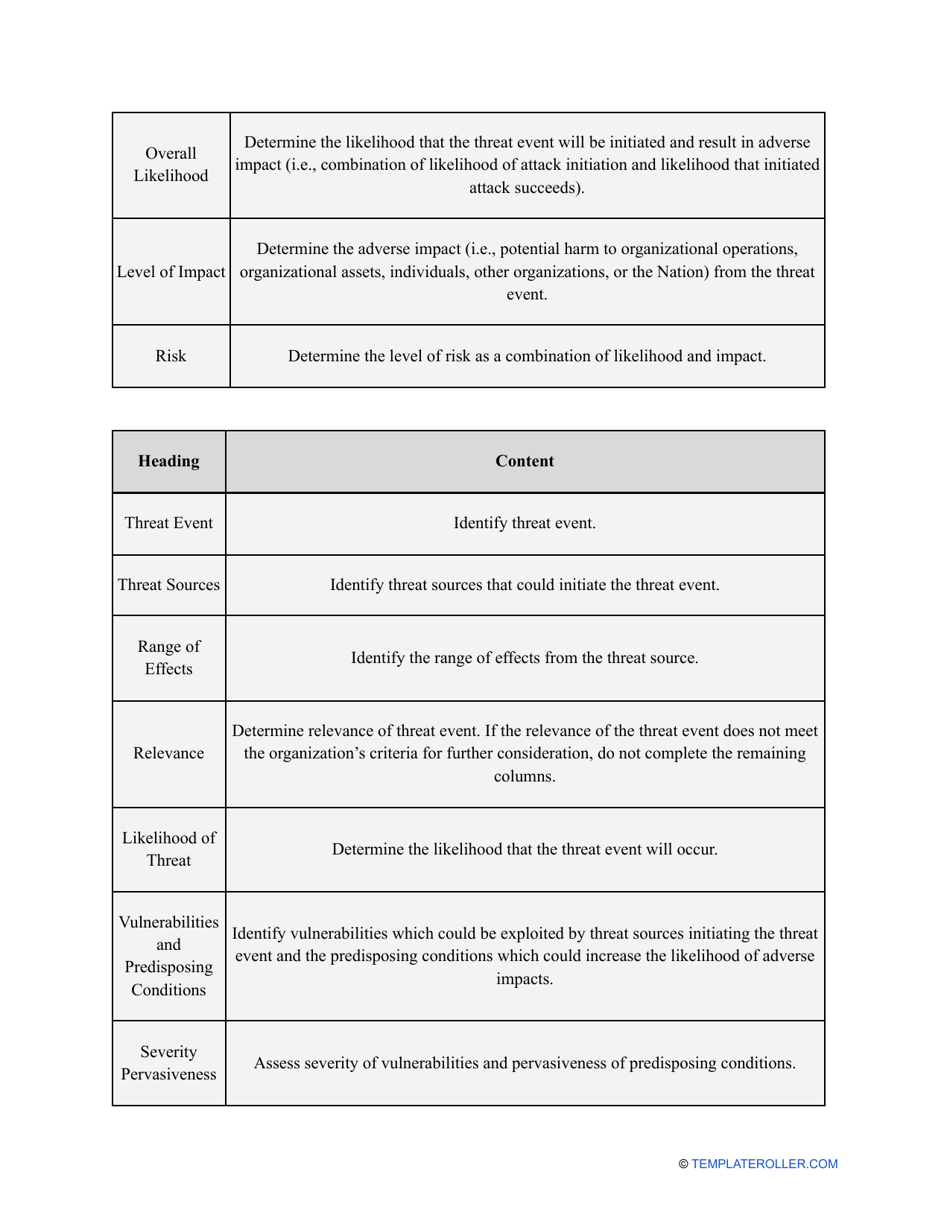
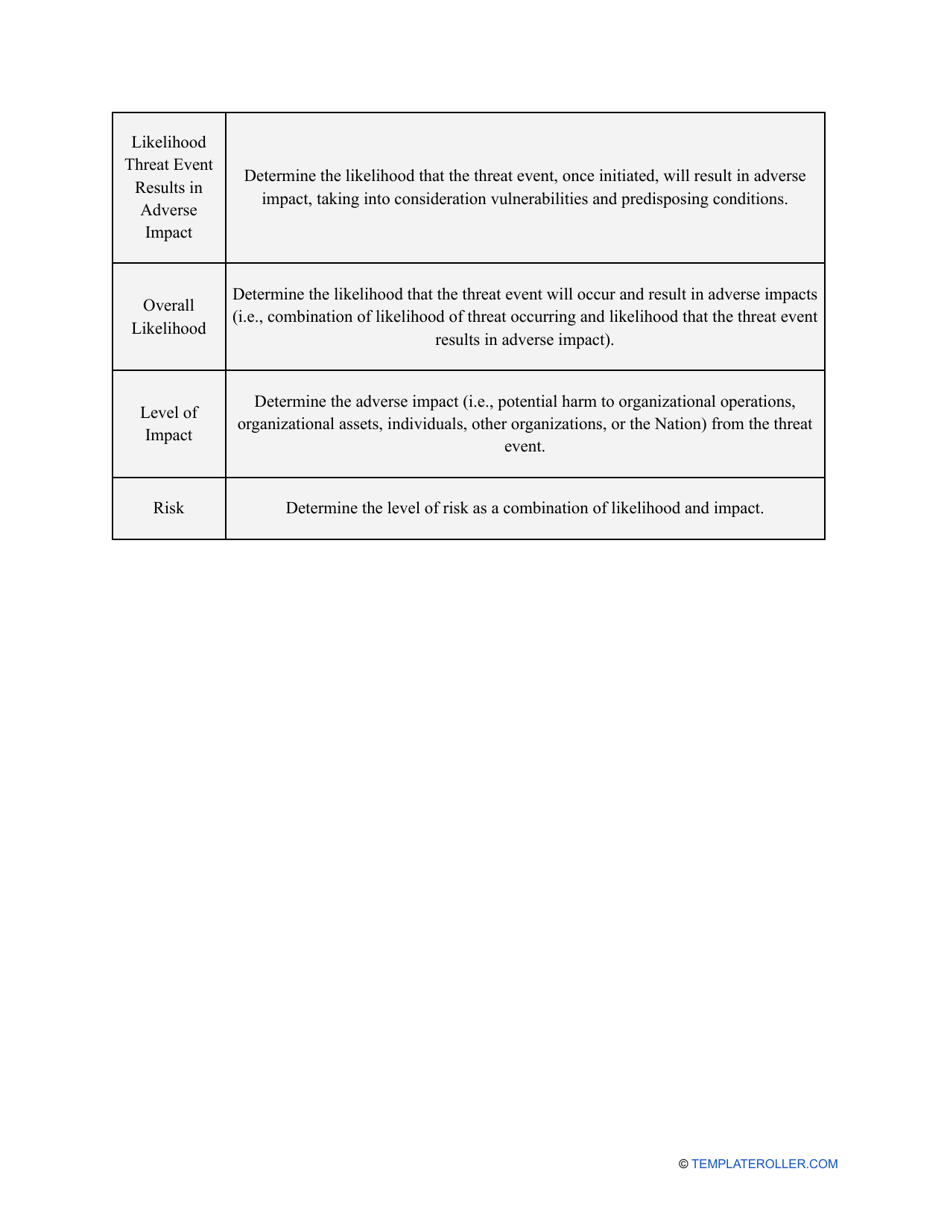
- Outline the threats to your entity - harmful human actions, accidental human errors, system failure, etc. You may use a scale to indicate the level of risk - from very low to very high.
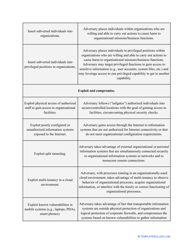
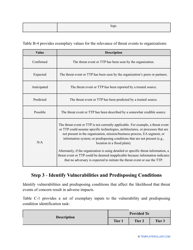
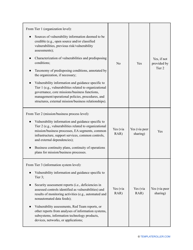
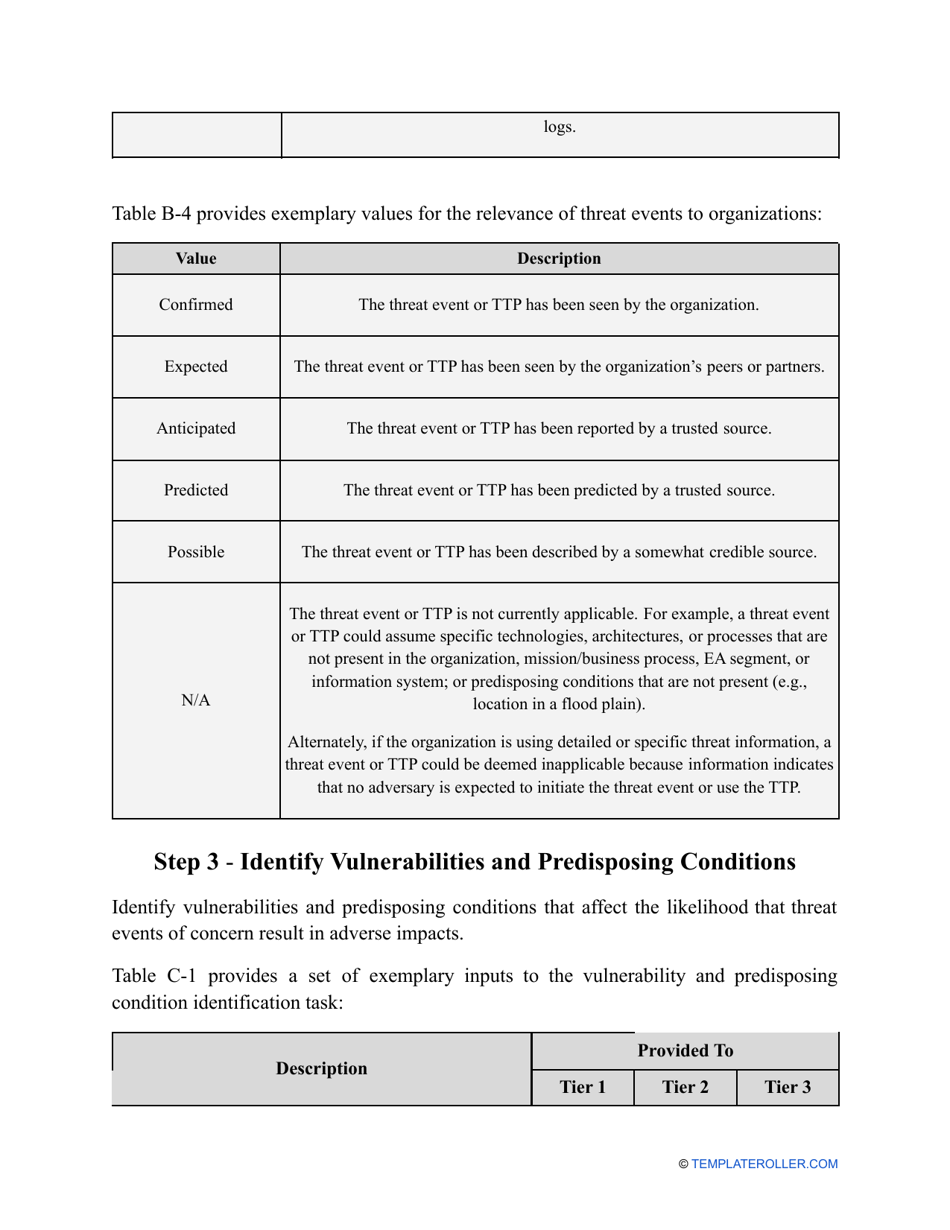
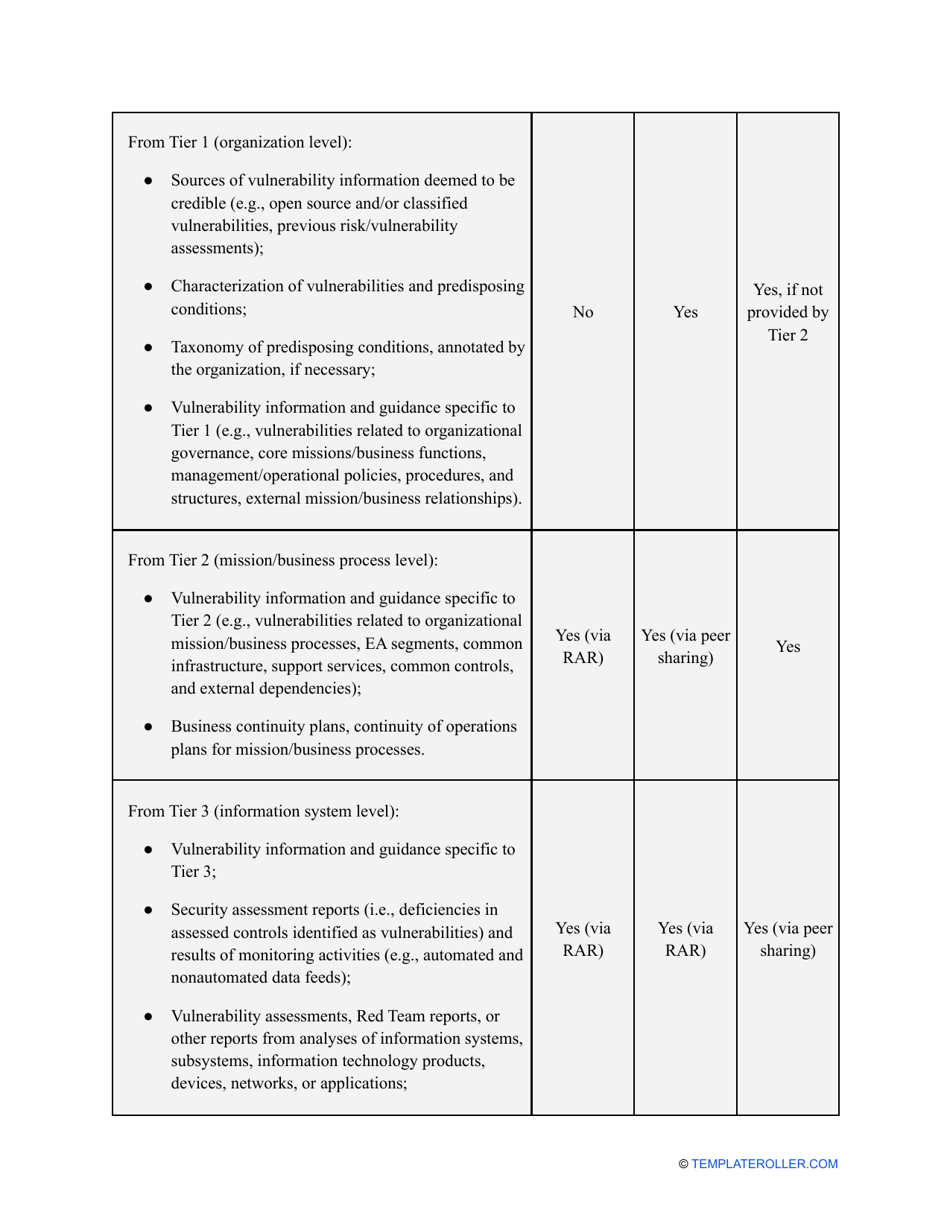
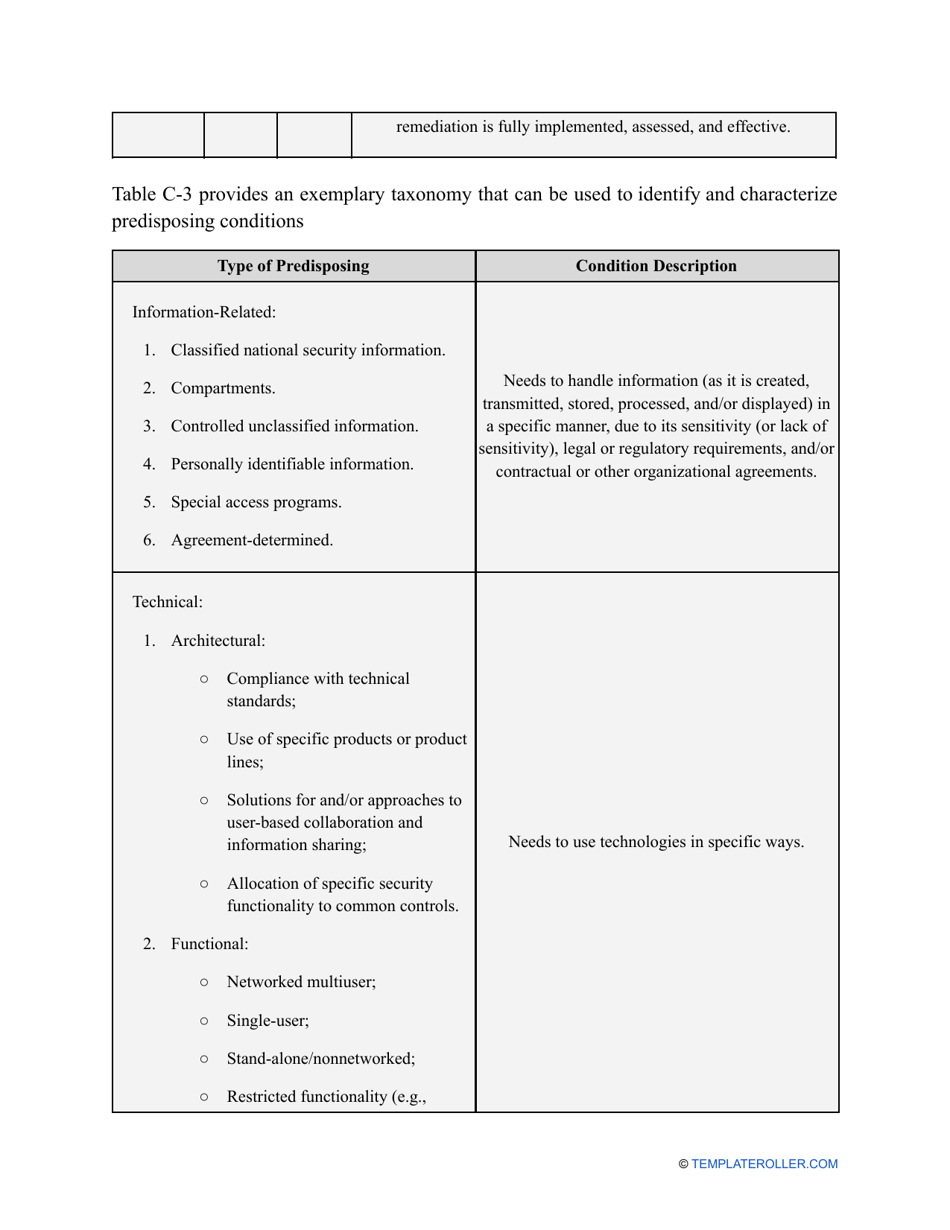
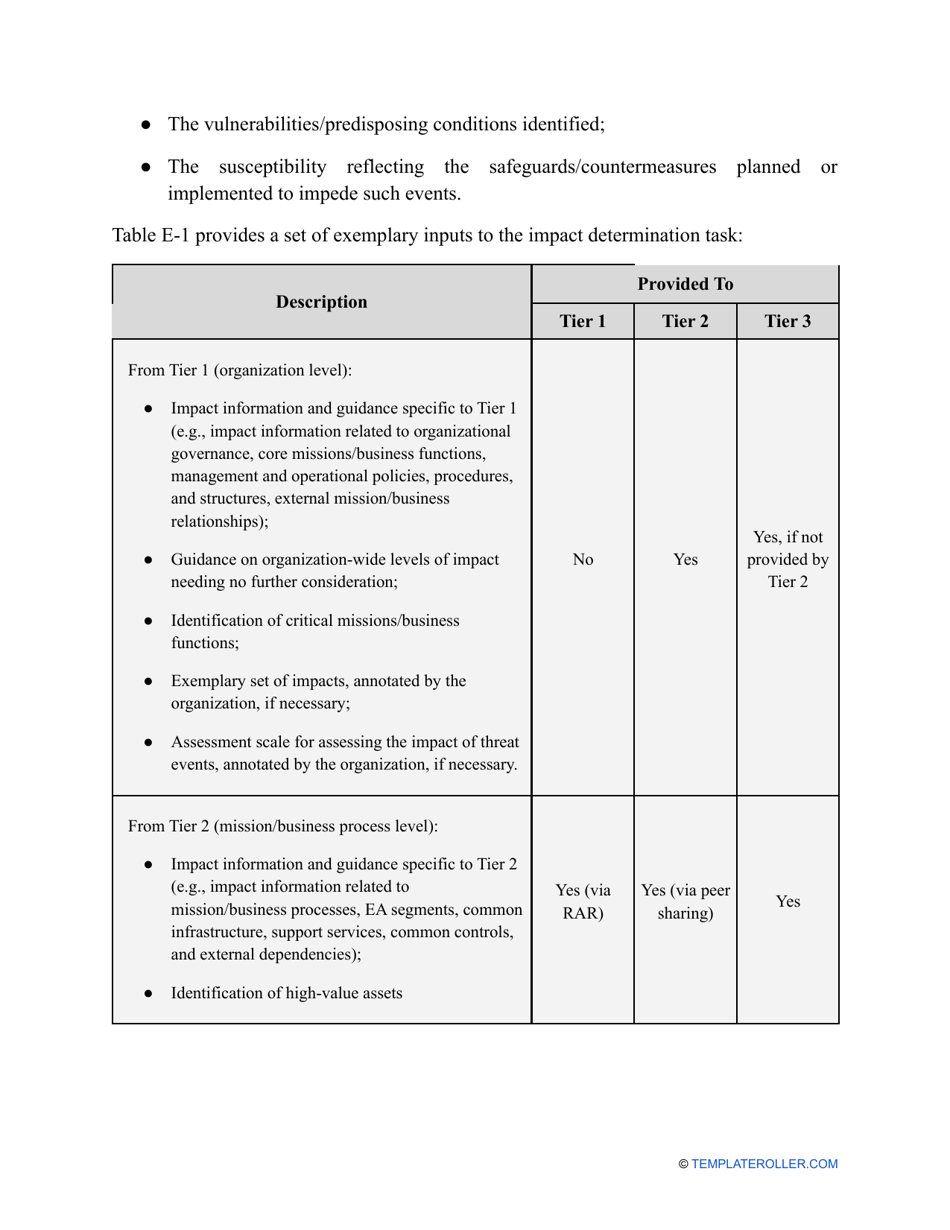
- Find out about the vulnerabilities of your organization . Are you ready to confront threats right away? If not, you might need to purchase new equipment that can withstand the attacks better, limit access to the most sensitive data your organization keeps in digital form and hard copy, and train personnel to teach them how to identify flaws of the system and protect the interests of the business.
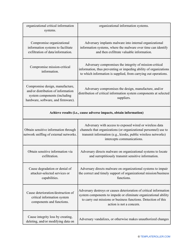
- Conduct interviews with employees responsible for cybersecurity . They will tell you about their experience of dealing with software and confidential information on a daily basis - this way, you will learn about potential issues first-hand. Record their observations and assess them to find out what measures you are ready to take to avoid more problems in the future.
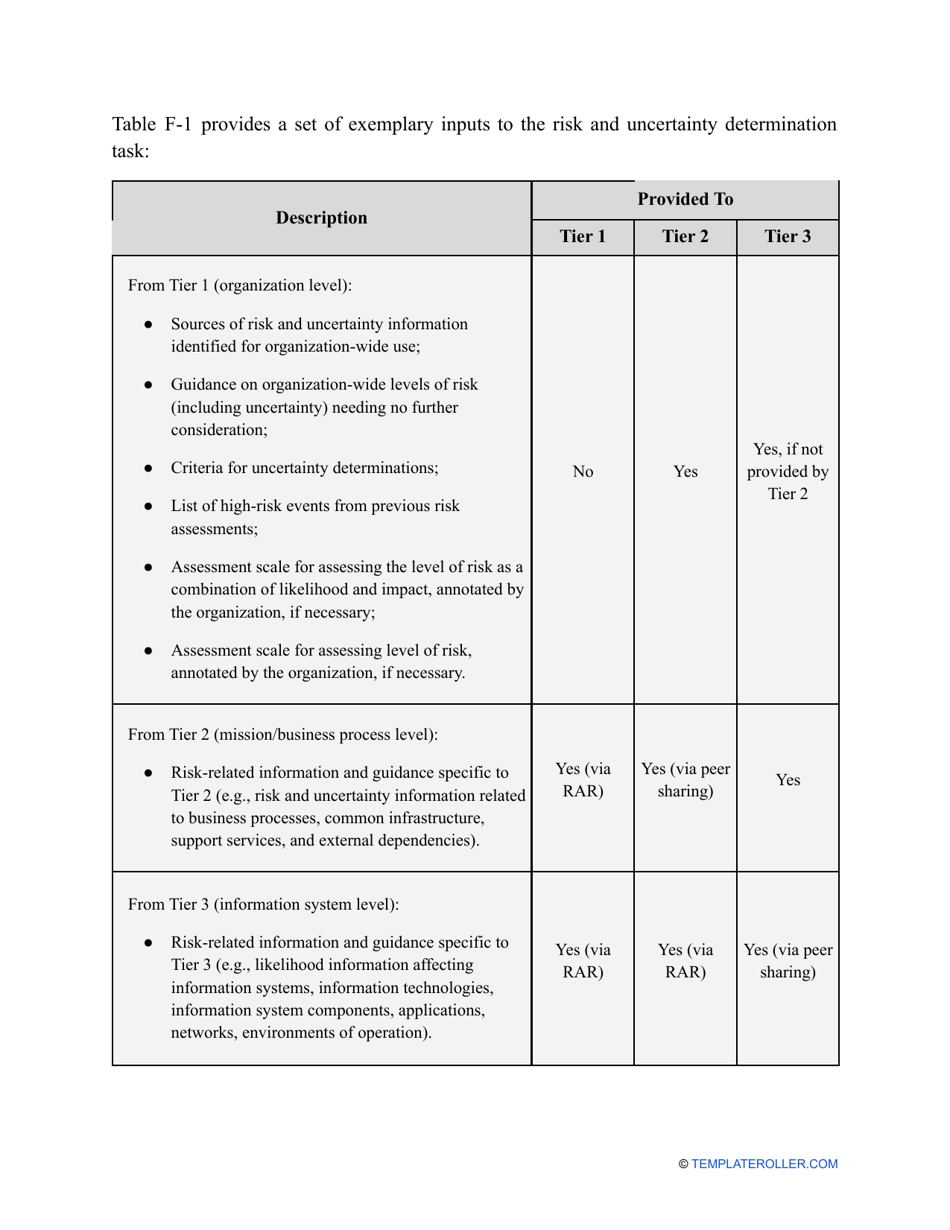
- List uncertainties you have faced during the evaluation and explain how they will affect your decisions from now on.
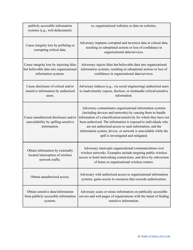
- Add tables and graphs that will let the company management see the potential risks - for instance, the likelihood of a cyberattack in case all employees have the same level of access to confidential data.
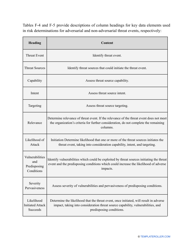
- Make a list of references to relevant NIST regulations you have used during the evaluation . Name employees who conducted the risk assessment and add their contact details.
Haven't found the template you're looking for? Take a look at the related templates below: